Answered step by step
Verified Expert Solution
Question
1 Approved Answer
For this project, you will be writing a client/server application to implement a somewhat secure brokerage service using TCP s ockets. Secure communication between a
For this project, you will be writing a client/server application to implement a somewhat secure brokerage service using TCP sockets. Secure communication between a client and the broker will be through a four-way handshake using RSA public key encryption (PKE). A third-party program will act as the public-key manager. All communication between client and broker will be secured using RSA PKE.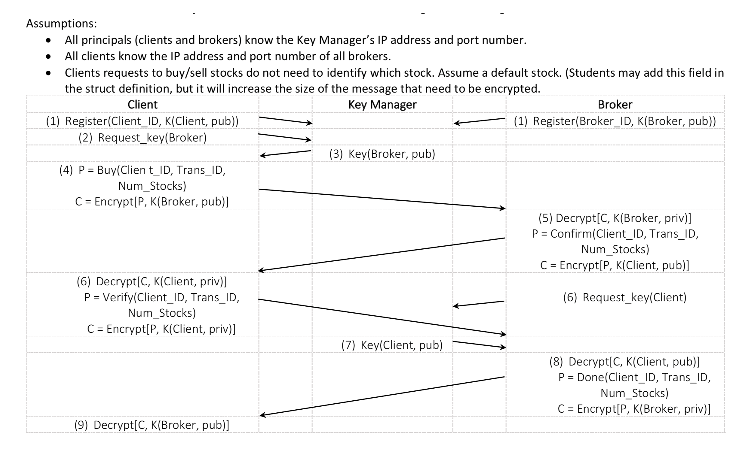
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


