Let P be a family of trapdoor permutations with hardcore predicates. Let Samp be a PPT algorithm which, on input the security parameter A
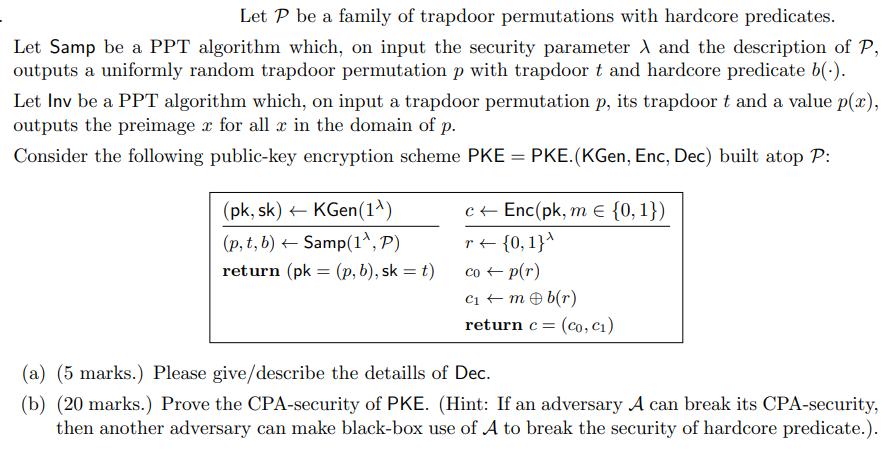
Let P be a family of trapdoor permutations with hardcore predicates. Let Samp be a PPT algorithm which, on input the security parameter A and the description of P, outputs a uniformly random trapdoor permutation p with trapdoor t and hardcore predicate b(.). Let Inv be a PPT algorithm which, on input a trapdoor permutation p, its trapdoor t and a value p(x), outputs the preimager for all x in the domain of p. Consider the following public-key encryption scheme PKE = PKE. (KGen, Enc, Dec) built atop P: (pk, sk) KGen(1) (p, t, b) Samp(1^, P) - return (pk: = (p, b), sk = t) c Enc(pk, me {0, 1}) r {0, 1}^ co p(r) C + m b(r) return c = = (co, C) (a) (5 marks.) Please give/describe the detaills of Dec. (b) (20 marks.) Prove the CPA-security of PKE. (Hint: If an adversary A can break its CPA-security, then another adversary can make black-box use of A to break the security of hardcore predicate.).
Step by Step Solution
There are 3 Steps involved in it
Step: 1
Answer a The decryption algorithm Dec for the given PKE scheme is as follows Decsk c Invp t c1 c2 where sk t is the trapdoor of the permutation p pk c ...
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


