Gina is preparing to monitor network activity using packet sniffing. Which technology is most likely to interfere with this effort if used on the
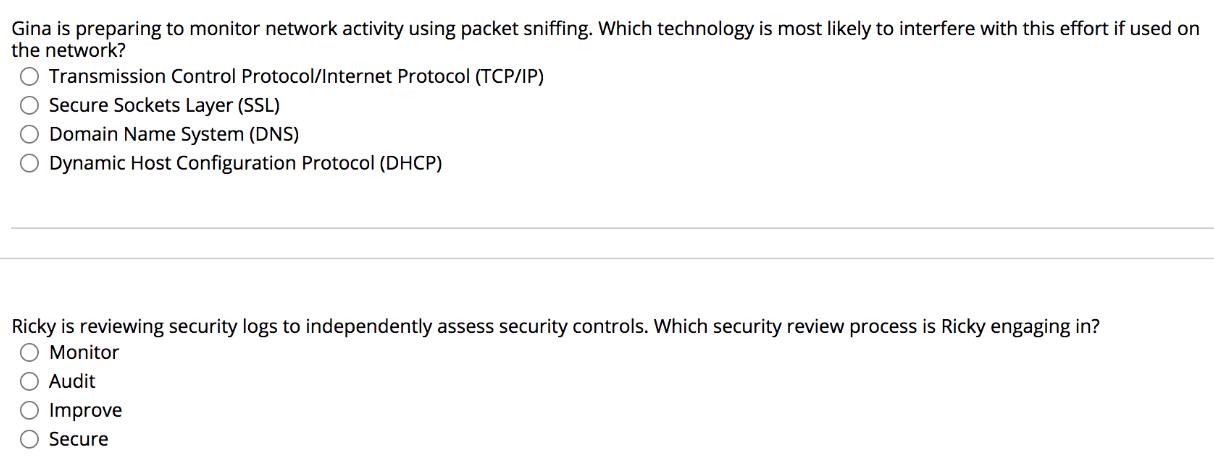
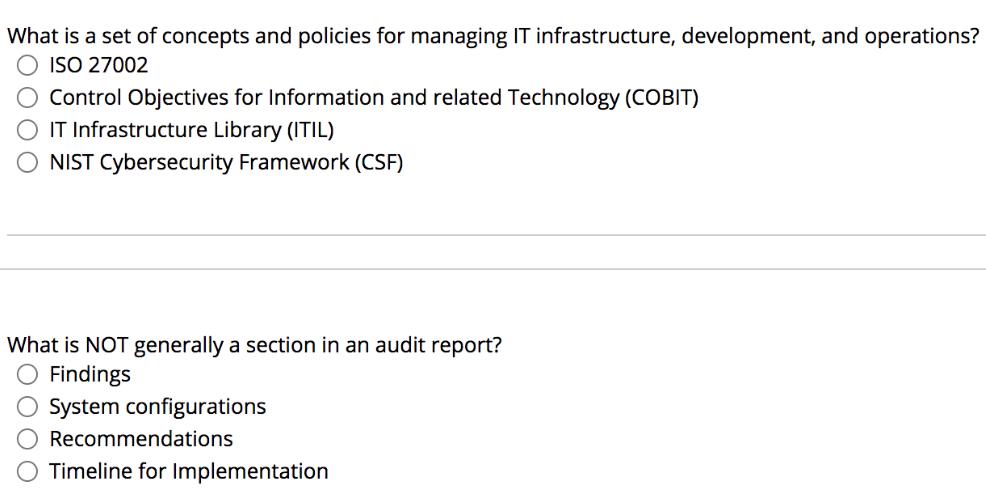
Gina is preparing to monitor network activity using packet sniffing. Which technology is most likely to interfere with this effort if used on the network? O Transmission Control Protocol/Internet Protocol (TCP/IP) O Secure Sockets Layer (SSL) O Domain Name System (DNS) O Dynamic Host Configuration Protocol (DHCP) Ricky is reviewing security logs to independently assess security controls. Which security review process is Ricky engaging in? O Monitor O Audit O Improve Secure What is a set of concepts and policies for managing IT infrastructure, development, and operations? ISO 27002 Control Objectives for Information and related Technology (COBIT) IT Infrastructure Library (ITIL) NIST Cybersecurity Framework (CSF) What is NOT generally a section in an audit report? O Findings O System configurations Recommendations Timeline for Implementation
Step by Step Solution
3.31 Rating (154 Votes )
There are 3 Steps involved in it
Step: 1
The detailed answer for the above question is provided below 1Secure Socket LayerSSL SSL is protocol ...
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


