Question
Hello, I was looking for a little help with filling out this chart for practicing for an exam. I'm supposed to put an intrusion, security
Hello, I was looking for a little help with filling out this chart for practicing for an exam.
I'm supposed to put an intrusion, security goal violated, and the justification for why I chose the specified Intrusion and Security goal for each situation.
These are the intrusions available:
Interruption, Interception, Modification, Fabrication, and Invasion
These are the Security Goals available:
Confidentially, Integrity, Authentication, non-repudiation, Access control, and availability
The first one is an example and the next few are ones I attempted.
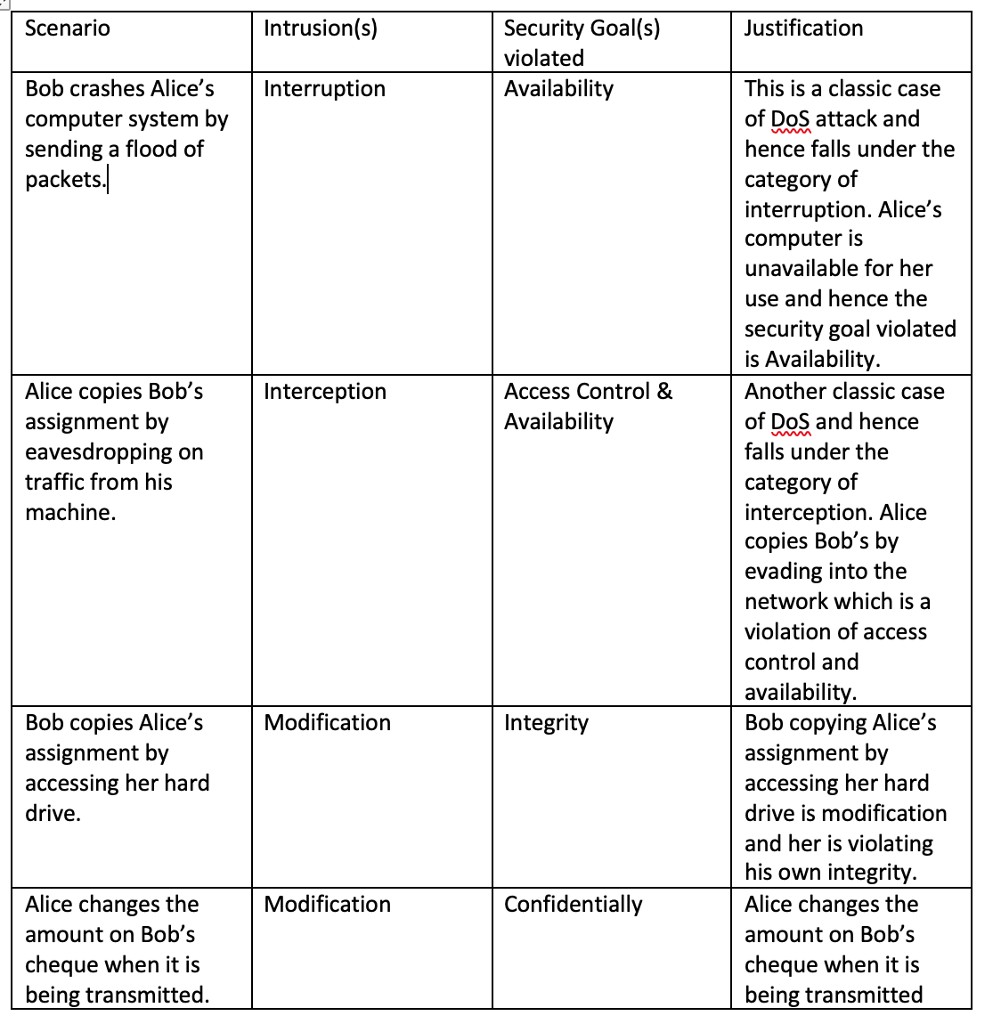
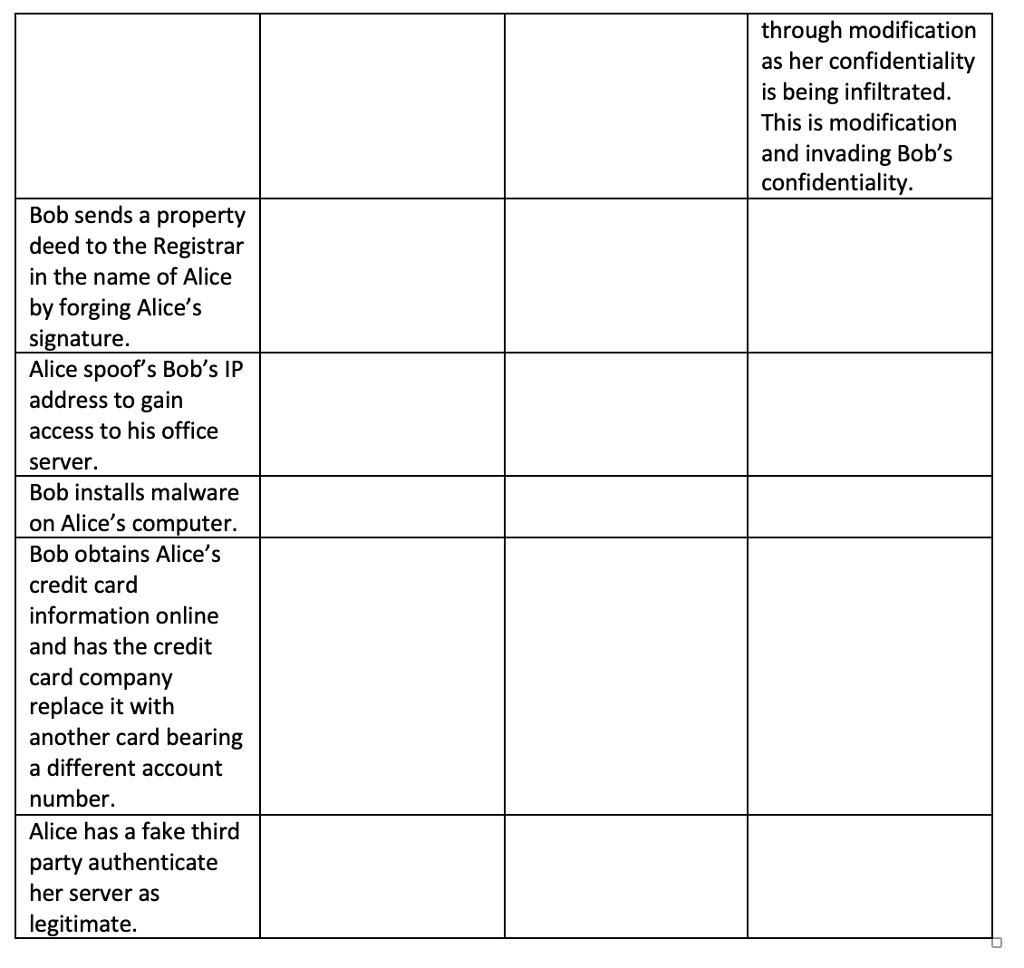
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


