Question
Here is some partial code to get you started. You write the Encode and Decode procedures. .586 ;Target processor. Use instructions for Pentium class machines

Here is some partial code to get you started. You write the Encode and Decode procedures.
.586 ;Target processor. Use instructions for Pentium class machines
.MODEL FLAT ;Use the flat memory model, standard calling convention
INCLUDE io.h
.STACK 4096 ;Define a stack segment of 1KB
.DATA ;Create a near data segment. Local variables are declared here
strprmpt BYTE "Enter a string of 40 characters or less", 0
enclabel BYTE "encoded data, as a string:", 0
declabel BYTE "decoded string:", 0
numkeys DWORD 7
keys DWORD 1, 4, 2, 3, 6, 7, 5
masks BYTE 00110100b, 00000000b, 00101010b, 00001100b, 00110110b, 00110110b, 00101010b
rawstr BYTE 41 DUP (?)
decstr BYTE 41 DUP (?)
encdata BYTE 41 DUP (?)
encstr BYTE 81 DUP (?)
.CODE ;Indicates the start of a code segment.
_MainProc PROC
input strprmpt, rawstr, 40 ; ask for the string to be encoded
lea esi, rawstr
pushd esi ; pass address of raw string to routine
lea esi, encdata
pushd esi ; pass the address for result
lea esi, masks
pushd esi ; pass the array of masks to use
lea esi, keys
pushd esi ; pass the array of masks to use
pushd numkeys ; and the number of masks
call Encode
add esp, 20 ; fix the stack
lea esi, encdata ; pass encoded data (hex) to the procedure
push esi
lea esi, encstr ; pass address for resulting string
push esi
push eax ; return from Decode is the number of bytes
call IntArrToString
add esp, 12 ; fix the stack
output enclabel, encstr ; write out the encoded string
lea esi, encdata
pushd esi ; pass address of raw string to routine
lea esi, decstr
pushd esi ; pass the address for result
lea esi, masks
pushd esi ; pass the array of masks to use
lea esi, keys
pushd esi ; pass the array of masks to use
pushd numkeys ; and the number of masks
call Decode
add esp, 20 ; fix the stack
output declabel, decstr ; write out the encoded string
nop
ret ; go back to Windows?
_MainProc ENDP
; IntArrToString converts an array of byte numeric values into a string array for output
; Inputs in order pushed:
; addr of source byte array (32 bits)
; addr for storing the resulting string
; N: num of bytes to be printed (note: resulting string will be 2N+1)
; no meaningful return value
IntArrToString PROC
push ebp ; save EBP
push esi ; points to the source byte array
push edi ; points to the destination
push ecx ; loop count
mov ebp,esp ; establish stack frame
mov esi, [ebp+28] ; copy the address of the input array
mov edi, [ebp+24] ; and the destination address
mov ecx, [ebp+20] ; get the length
IntArrLp:
mov al, [esi] ; get current byte
shr al, 4 ; upper nybble into lower
and al, 00Fh ; clear top four bits
cmp al, 9 ; see if it's ten or more (A - F in hex)
jle isNotHex1
add al, 007h ; add a bit more if A-F
isNotHex1:
add al, 030h ; convert to ASCII
mov [edi], al
inc edi
mov al, [esi] ; get current byte
and al, 00Fh ; clear top four bits
cmp al, 9 ; see if it's ten or more (A - F in hex)
jle isNotHex2
add al, 007h ; add a bit more if A-F
isNotHex2:
add al, 030h ; convert to ASCII
mov [edi], al
inc edi
inc esi
loop IntArrLp
pop ecx
pop edi
pop esi
pop ebp
ret
IntArrToString ENDP
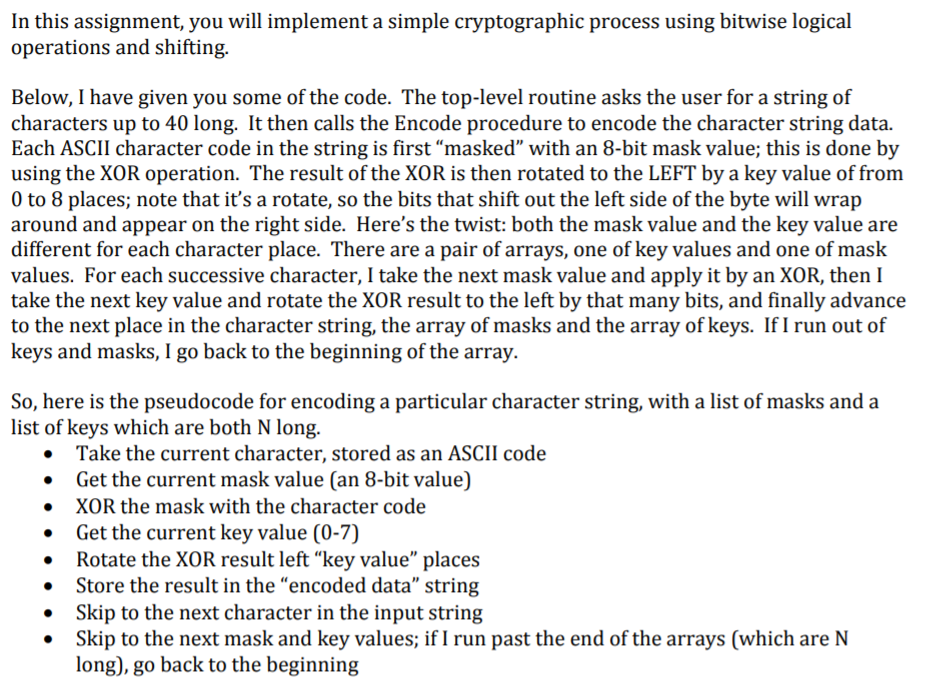
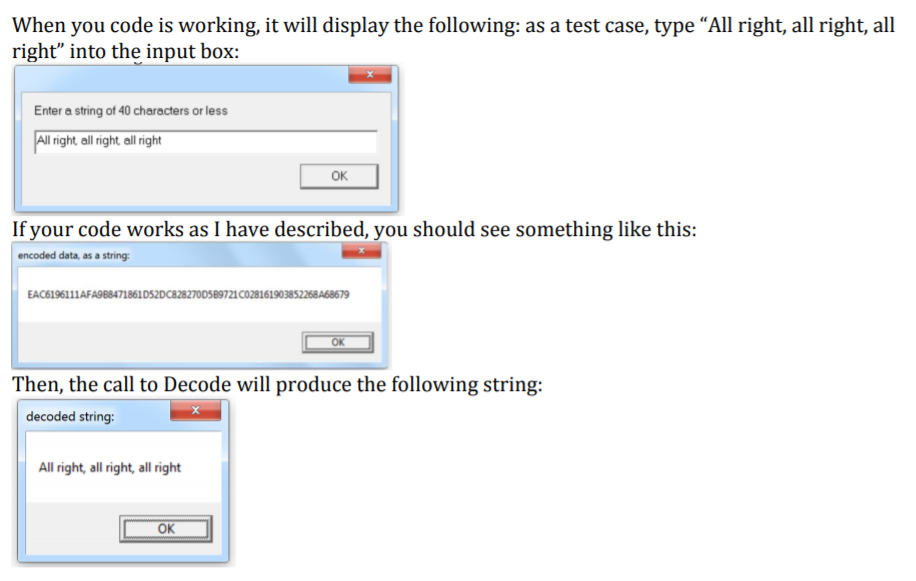
In this assignment, you will implement a simple cryptographic process using bitwise logical operations and shifting. Below, I have given you some of the code. The top-level routine asks the user for a string of characters up to 40 long. It then calls the Encode procedure to encode the character string data. Each ASCII character code in the string is first "masked" with an 8-bit mask value; this is done by using the XOR operation. The result of the XOR is then rotated to the LEFT by a key value of from 0 to 8 places; note that it's a rotate, so the bits that shift out the left side of the byte will wrap around and appear on the right side. Here's the twist: both the mask value and the key value are different for each character place. There are a pair of arrays, one of key values and one of mask values. For each successive character, I take the next mask value and apply it by an XOR, then I take the next key value and rotate the XOR result to the left by that many bits, and finally advance to the next place in the character string, the array of masks and the array of keys. IfI run out of keys and masks, I go back to the beginning of the array. So, here is the pseudocode for encoding a particular character string, with a list of masks and a list of keys which are both N long. Take the current character, stored as an ASCII code Get the current mask value (an 8-bit value) XOR the mask with the character code Get the current key value (0-7) Rotate the XOR result left "key value" places . . e . Store the result in the "encoded data" string . Skip to the next character in the input string . Skip to the next mask and key values; if I run past the end of the arrays (which areN long), go back to the beginningStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


