Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Here is the link for the starter file:https://docs.google.com/document/d/1r3AOaLUwPJ7ExZQ6dIRvkFrdLFXzp21uJIcM4O606Ng/edit?usp=sharing Yes, it's in a secret code. But, you know the secret. Each character in the message equals
Here is the link for the starter file:https://docs.google.com/document/d/1r3AOaLUwPJ7ExZQ6dIRvkFrdLFXzp21uJIcM4O606Ng/edit?usp=sharing
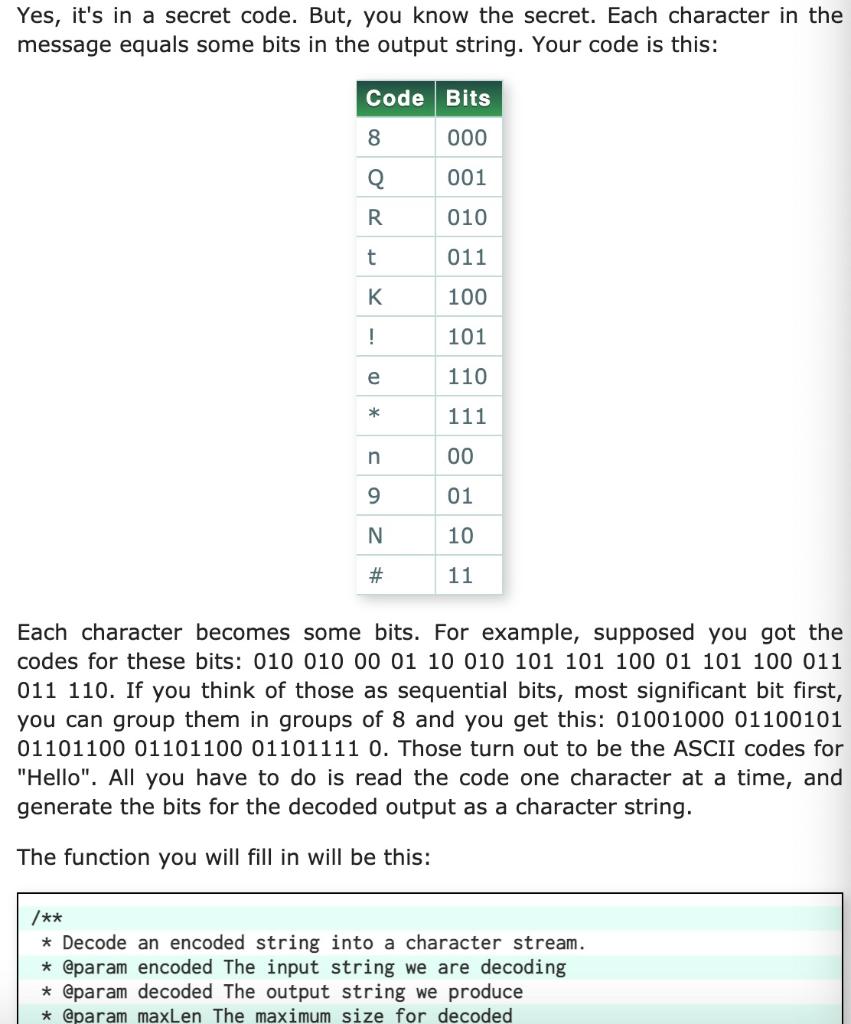
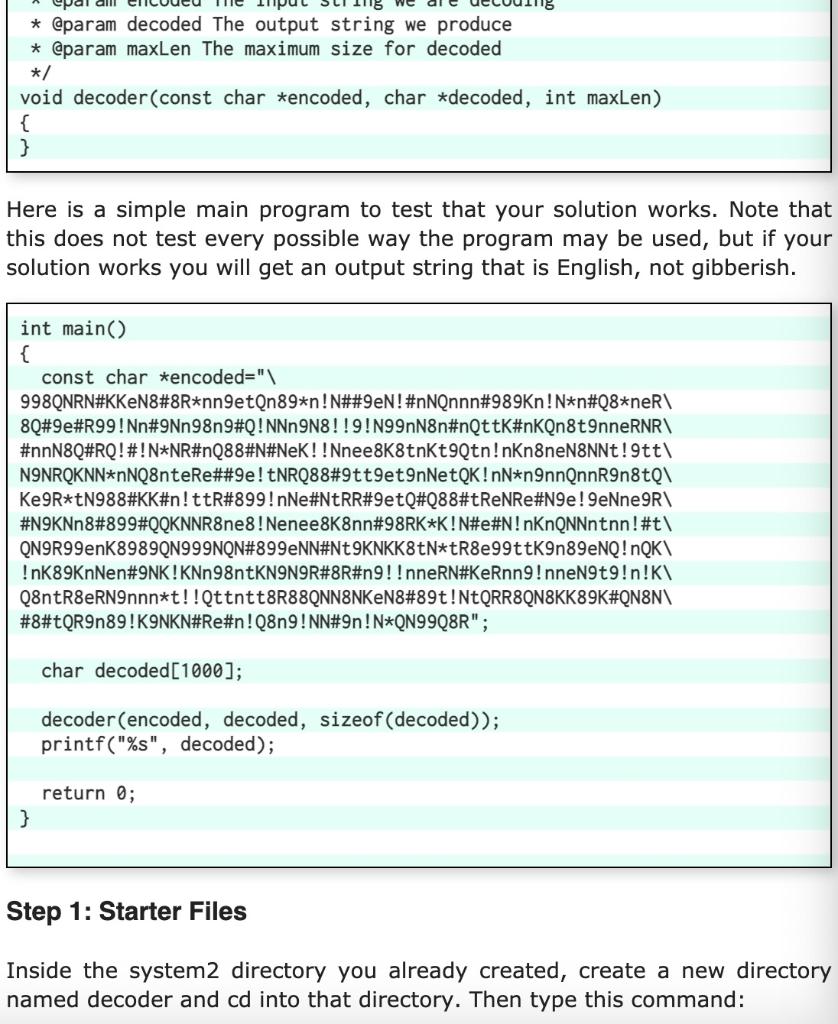
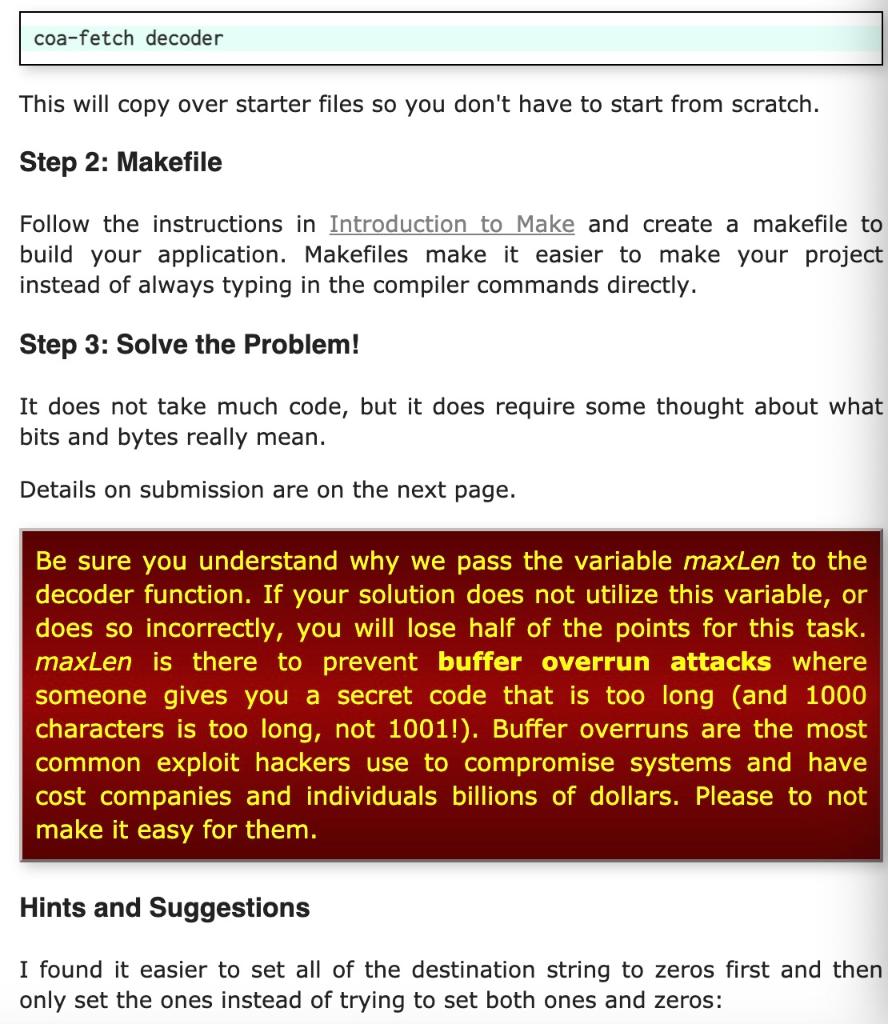
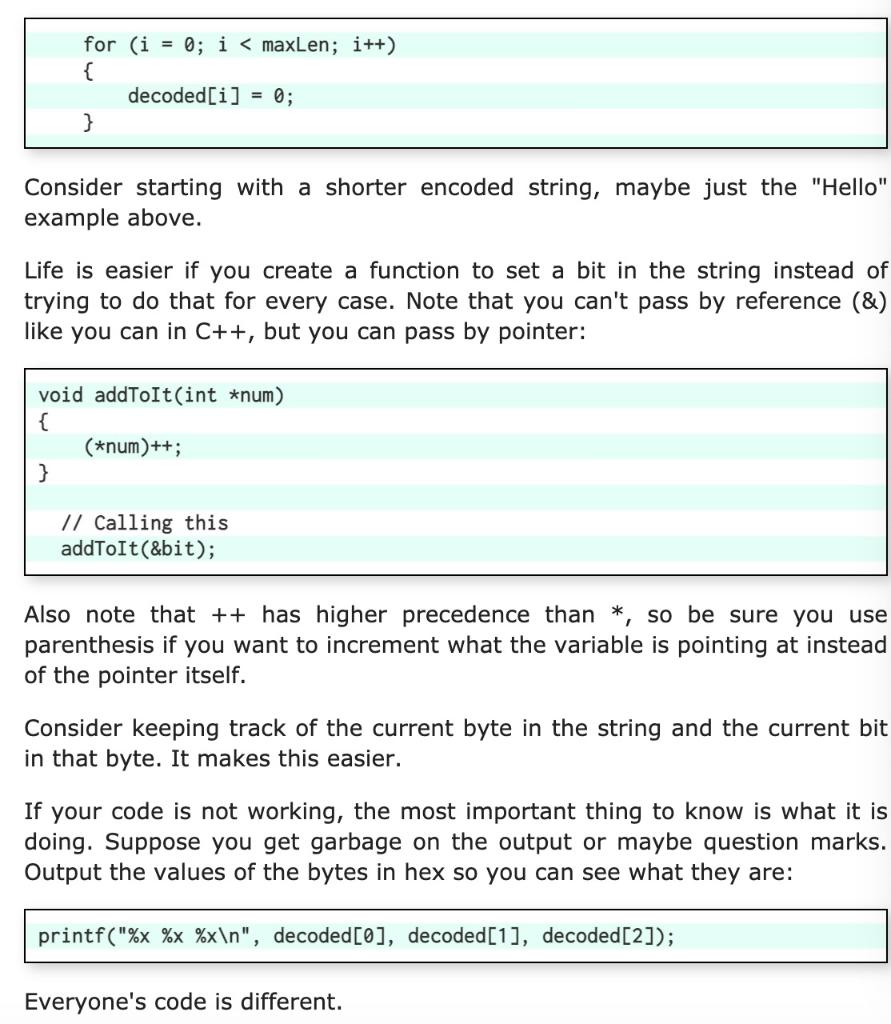
Yes, it's in a secret code. But, you know the secret. Each character in the message equals some bits in the output string. Your code is this: Code Bits 8 000 Q 001 R 010 t 011 K 100 ! 101 e 110 * 111 00 9 01 N 10 # 11 Each character becomes some bits. For example, supposed you got the codes for these bits: 010 010 00 01 10 010 101 101 100 01 101 100 011 011 110. If you think of those as sequential bits, most significant bit first, you can group them in groups of 8 and you get this: 01001000 01100101 01101100 01101100 01101111 0. Those turn out to be the ASCII codes for "Hello". All you have to do is read the code one character at a time, and generate the bits for the decoded output as a character string. The function you will fill in will be this: /** * Decode an encoded string into a character stream. * @param encoded The input string we are decoding * @param decoded The output string we produce * @param maxLen The maximum size for decoded * @param decoded The output string we produce * @param maxLen The maximum size for decoded */ void decoder(const char *encoded, char *decoded, int maxlen) { } Here is a simple main program to test that your solution works. Note that this does not test every possible way the program may be used, but if your solution works you will get an output string that is English, not gibberish. int main() { const char *encoded=" 998QNRN#KKENR*nnetQn89*n! N##9eN! #nNQnnn#989kn!N*n#Q8*ner\ 8Q#9e#R99! Nn#9Nn98n9#Q! NNn9N8!!9!N99nN8n#nQttK#nkQn8t9nneRNR\ #nnN8Q#RQ! #!N*NR#nQ88#N#NeK!!Nnee8K8tnkt9Qtn!nkn8neN8NNt!9tt\ N9NRQKNN*nNQ8nteRe##9e! ENRQ88#9tt9et9nNetQK!DN*n9nnQnnR9n8tQ\ Ke9R*tN988#KK#n!ttR#899! nNe#NtRR#9etQ#Q88#tReNRe#N9e9eNne 9R1 #N9KNn8#899#QQKNNR8ne8! Nenee8K8nn#98RK*K!N#e#N! nKnQNNntnn!#t\ QN9R99enK8989QN999NQN#899eNN#Nt9KNKK8tN*tR8e99ttK9n89eNQ! NQK\ !nk 89KnNen#9NK! KNn98ntKN9N9R#8R#n9!!nneRN#KeRnn9! nneN9t9!n!K\ Q8ntR8ERNInnn*t!!Qttntt8R88QNN8NKENYt!NtQRR8QN8KK89K#QN8NV #8#tQR9n89! KINKN#Re#n!Q8n9!NN#9n!N*QN99Q8R"; char decoded[1000]; decoder (encoded, decoded, sizeof(decoded)); printf("%s", decoded); return 0; } Step 1: Starter Files Inside the system2 directory you already created, create a new directory named decoder and cd into that directory. Then type this command: coa-fetch decoder This will copy over starter files so you don't have to start from scratch. Step 2: Makefile Follow the instructions in Introduction to Make and create a makefile to build your application. Makefiles make it easier to make your project instead of always typing in the compiler commands directly. Step 3: Solve the problem! It does not take much code, but it does require some thought about what bits and bytes really mean. Details on submission are on the next page. Be sure you understand why we pass the variable maxLen to the decoder function. If your solution does not utilize this variable, or does so incorrectly, you will lose half of the points for this task. maxLen is there to prevent buffer overrun attacks where someone gives you a secret code that is too long (and 1000 characters is too long, not 1001!). Buffer overruns are the most common exploit hackers use to compromise systems and have cost companies and individuals billions of dollars. Please to not make it easy for them. Hints and Suggestions I found it easier to set all of the destination string to zeros first and then only set the ones instead of trying to set both ones and zeros: for (i = 0; iStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


