Hi i need help with this in linux, i have to create a file as root in /home//Desktop but cant seem to figure how to do this. please read all of the instructions and DO NOT copy from anywhere else on the internet because ive ben looking for a while i will leave a like for correct answers ps the question i have is below where it says "Queston 29 Provide a screenshot of your commands" it starts from the paragraph about BOB
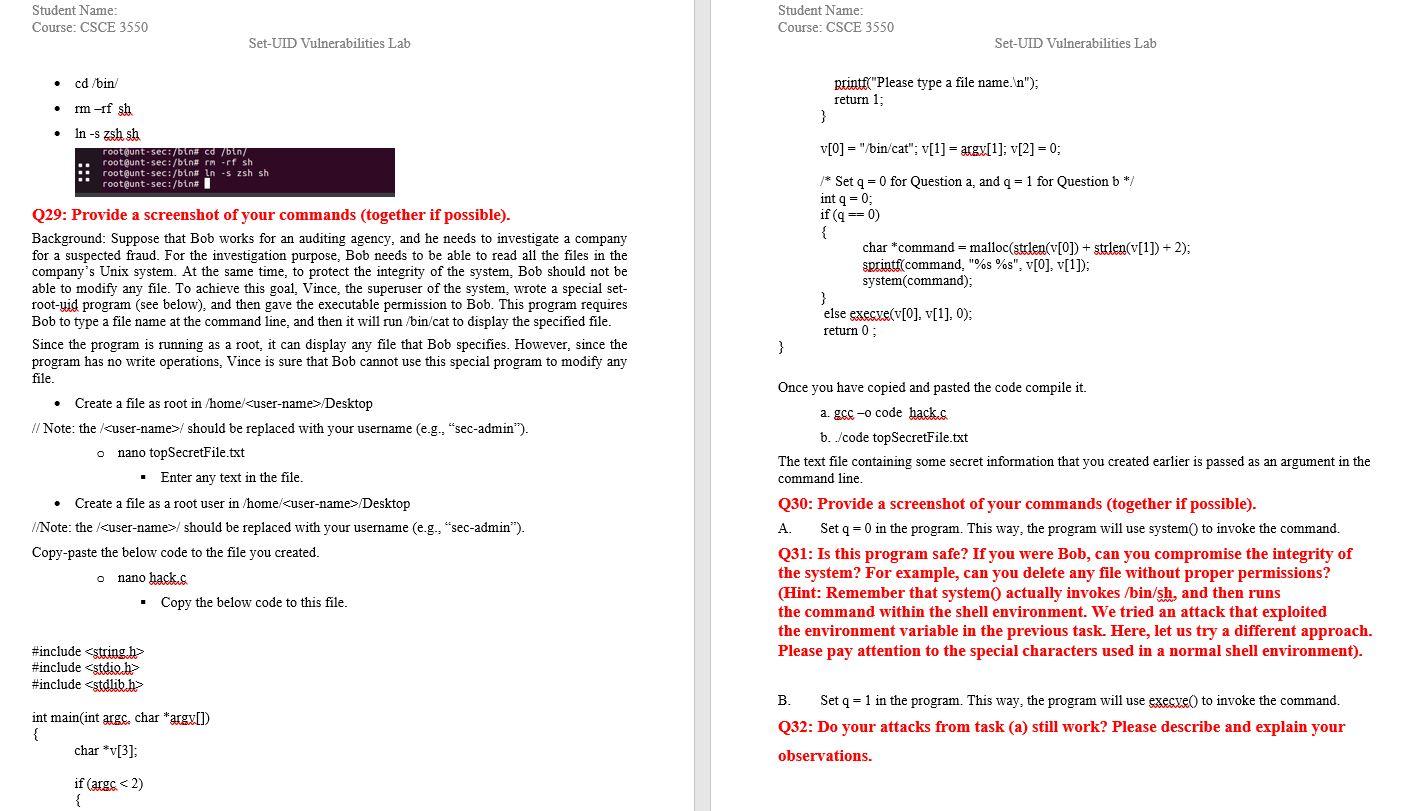
Here i will attach a screen shot of all my attempts to do this
Student Name: Student Name: Course: CSCE 3550 Course: CSCE 3550 Set-UID Vulnerabilities Lab Set-UID Vulnerabilities Lab - cd /bin printf("Please type a file name. n "); - rmrf sh \} - In-s zsh sh rooteunt-sec:/bin\# cd /bin/ sing v[0]= "/bin/cat"; v[1]=argu[1];v[2]=0; rootgunt-sec:/bthi rm - rf sh rooteunt-sec:/bint 1 Set q=0 for Question a, and q=1 for Question b/ int q=0 Q29: Provide a screenshot of your commands (together if possible). Background: Suppose that Bob works for an auditing agency, and he needs to investigate a company for a suspected fraud. For the investigation purpose, Bob needs to be able to read all the files in the company's Unix system. At the same time, to protect the integrity of the system, Bob should not be able to modify any file. To achieve this goal, Vince, the superuser of the system, wrote a special setroot-uid program (see below), and then gave the executable permission to Bob. This program requires Bob to type a file name at the command line, and then it will run /bin/cat to display the specified file. Since the program is running as a root, it can display any file that Bob specifies. However, since the program has no write operations, Vince is sure that Bob cannot use this special program to modify any file. Once you have copied and pasted the code compile it. - Create a file as root in /home/> Desktop a. gcc -0 code hackc // Note: the /> / should be replaced with your username (e.g., "sec-admin"). b. /code topSecretFile.txt - nano topSecretFile.txt The text file containing some secret information that you created earlier is passed as an argument in the - Enter any text in the file. command line. - Create a file as a root user in /home/ Desktop Q30: Provide a screenshot of your commands (together if possible). //Note: the / / should be replaced with your username (e.g., "sec-admin"). A. Set q=0 in the program. This way, the program will use system( ) to invoke the command. Copy-paste the below code to the file you created. Q31: Is this program safe? If you were Bob, can you compromise the integrity of the system? For example, can you delete any file without proper permissions? - Copy the below code to this file. (Hint: Remember that system0 actually invokes /bin/sh, and then runs the command within the shell environment. We tried an attack that exploited the environment variable in the previous task. Here, let us try a different approach. \#include Please pay attention to the special characters used in a normal shell environment). \#include h> \#include h B. Set q=1 in the program. This way, the program will use execye() to invoke the command. int main(int argc, char argu[] ) Q32: Do your attacks from task (a) still work? Please describe and explain your char *v[3]; observations. if (argc Desktop a. gcc -0 code hackc // Note: the /> / should be replaced with your username (e.g., "sec-admin"). b. /code topSecretFile.txt - nano topSecretFile.txt The text file containing some secret information that you created earlier is passed as an argument in the - Enter any text in the file. command line. - Create a file as a root user in /home/ Desktop Q30: Provide a screenshot of your commands (together if possible). //Note: the / / should be replaced with your username (e.g., "sec-admin"). A. Set q=0 in the program. This way, the program will use system( ) to invoke the command. Copy-paste the below code to the file you created. Q31: Is this program safe? If you were Bob, can you compromise the integrity of the system? For example, can you delete any file without proper permissions? - Copy the below code to this file. (Hint: Remember that system0 actually invokes /bin/sh, and then runs the command within the shell environment. We tried an attack that exploited the environment variable in the previous task. Here, let us try a different approach. \#include Please pay attention to the special characters used in a normal shell environment). \#include h> \#include h B. Set q=1 in the program. This way, the program will use execye() to invoke the command. int main(int argc, char argu[] ) Q32: Do your attacks from task (a) still work? Please describe and explain your char *v[3]; observations. if (argc








