Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Host A App Y App X TCP IP Network Access Protocol #1 Physical Global network address Network 1 Subnetwork attachment point address Port or
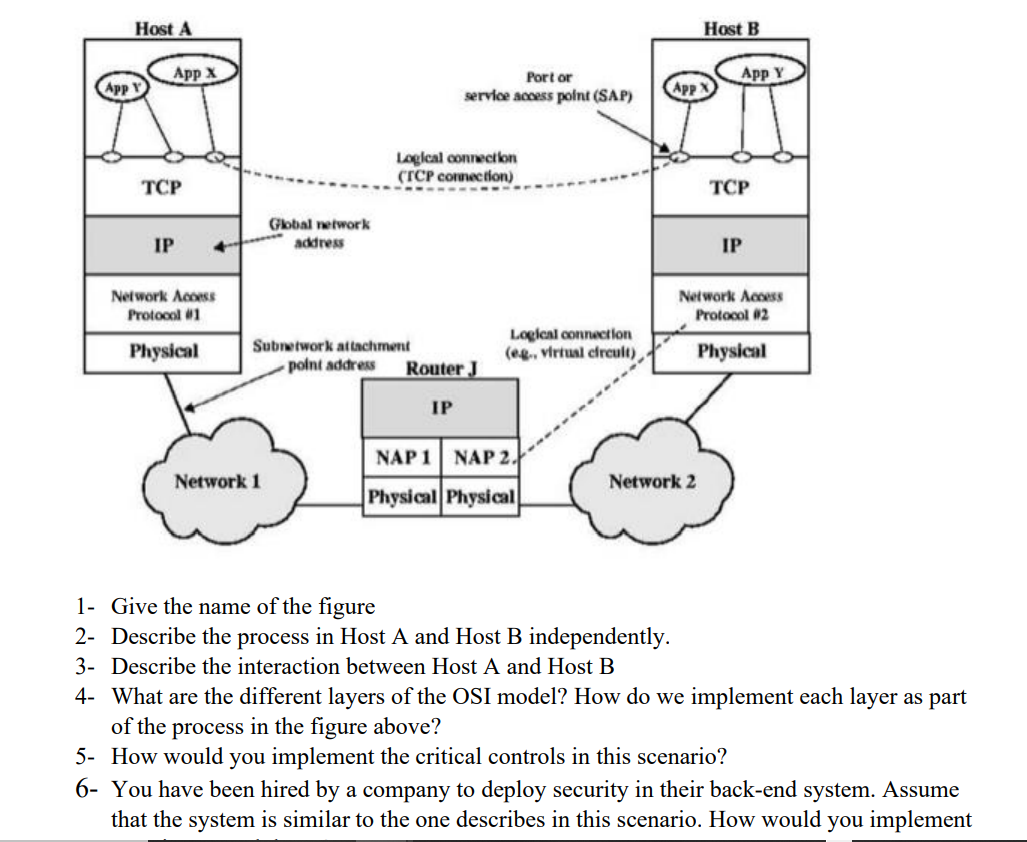
Host A App Y App X TCP IP Network Access Protocol #1 Physical Global network address Network 1 Subnetwork attachment point address Port or service access point (SAP) Logical connection (TCP connection) Router J IP Logical connection (eg., virtual circult), NAP 1 NAP 2. Physical Physical 1- Give the name of the figure 2- Describe the process in Host A and Host B independently. 3- Describe the interaction between Host A and Host B Host B App X Network 2 App Y TCP IP Network Access Protocol #2 Physical 4- What are the different layers of the OSI model? How do we implement each layer as part of the process in the figure above? 5- How would you implement the critical controls in this scenario? 6- You have been hired by a company to deploy security in their back-end system. Assume that the system is similar to the one describes in this scenario. How would you implement Consider how the cloud works "under the hood." From each customer's perspective, why does it appears as if they had a physical machine all by themselves? The cloud provider sells physical machines. The cloud provider sells virtual machines. The cloud provider sells most software. The cloud provider sells middleware. QUESTION 2 Why is your cloud app performance hard to predict? Your app may run many different types of machines. Your app may run on older machines. Your app may be affected by the load of other apps. Your app may crash.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


