Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I don't understand how the recursion works fully yet help me solve this code please. with C++ Learning Objectives - Use vector and string data
I don't understand how the recursion works fully yet help me solve this code please. with C++
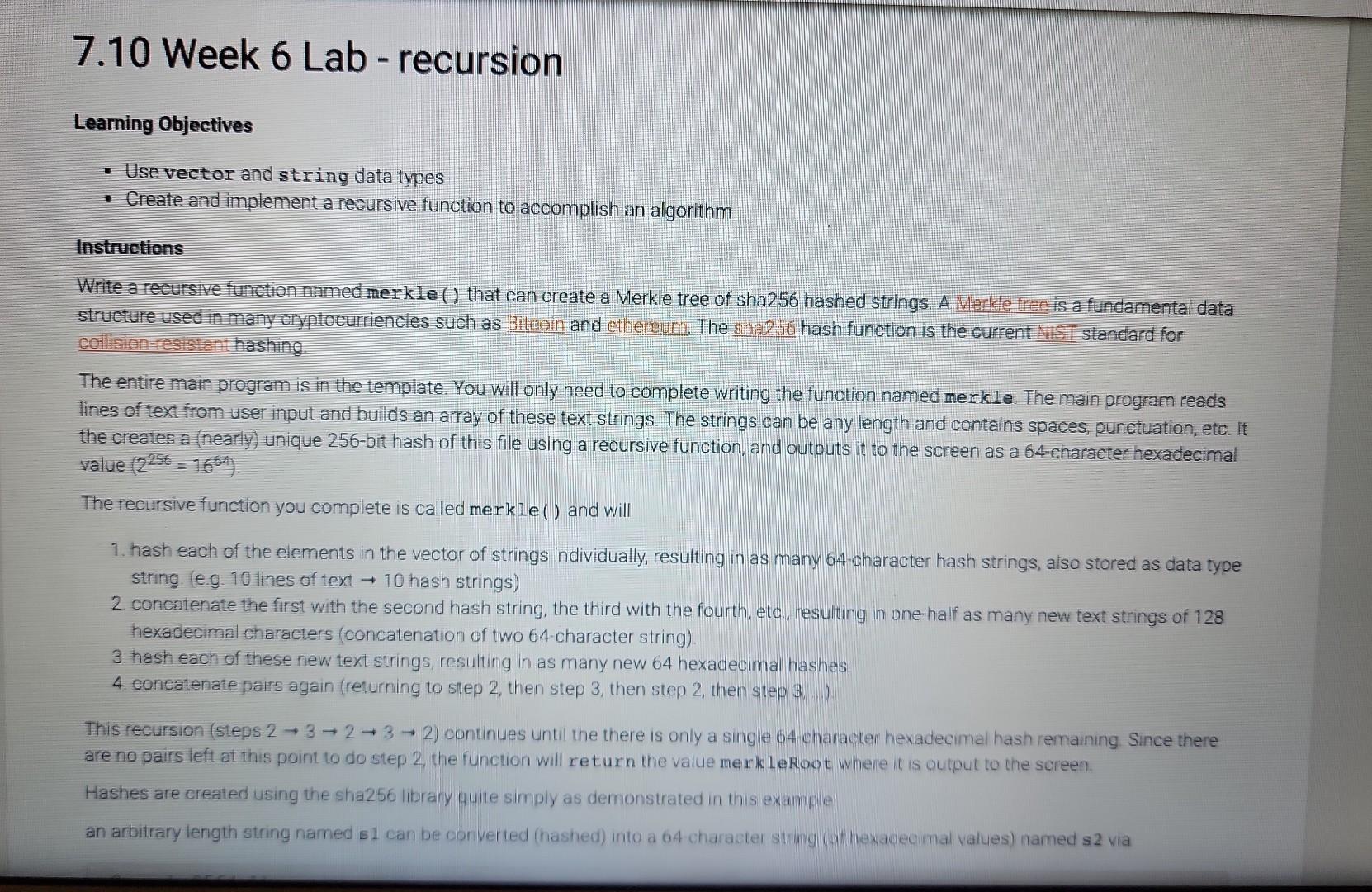
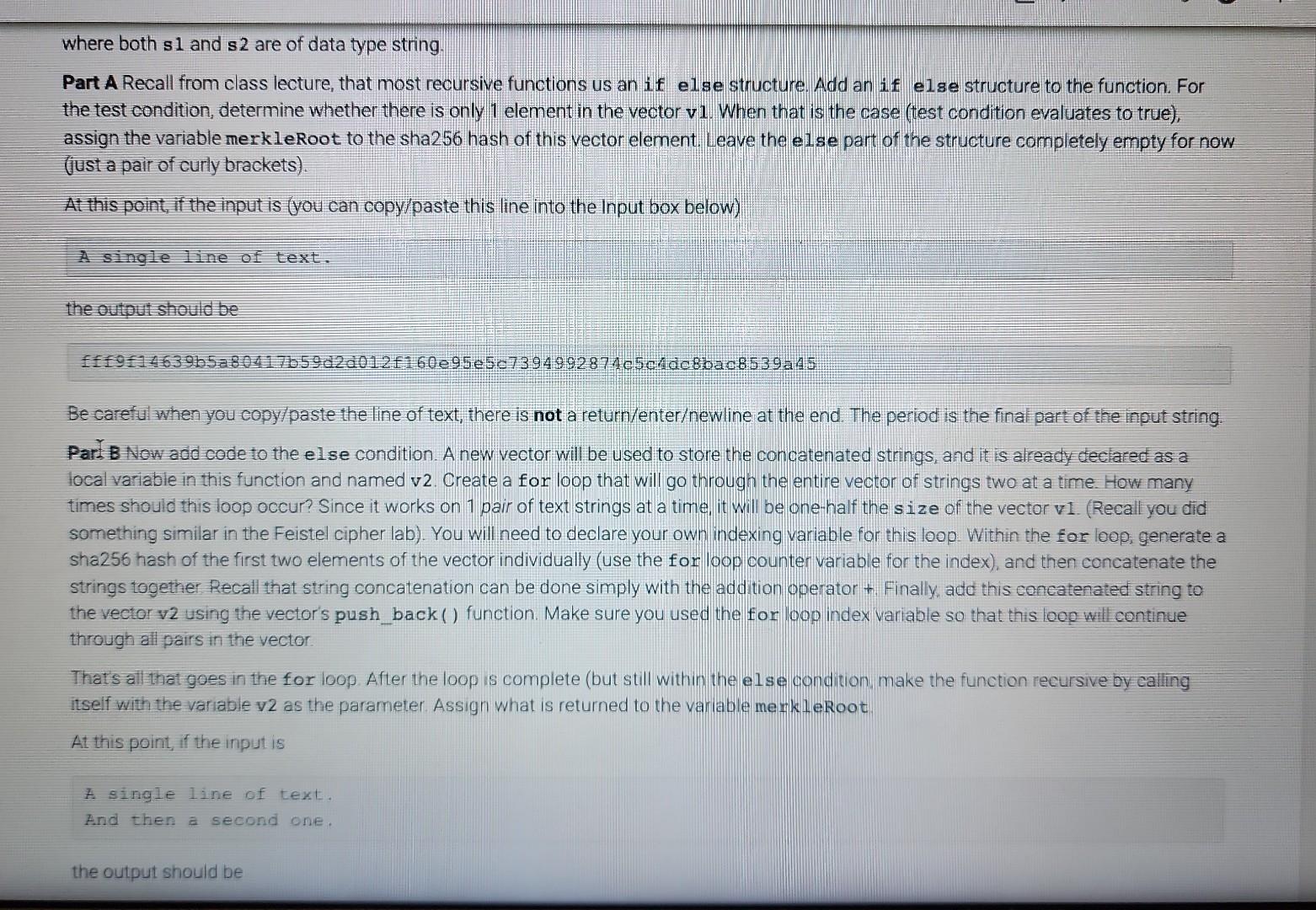
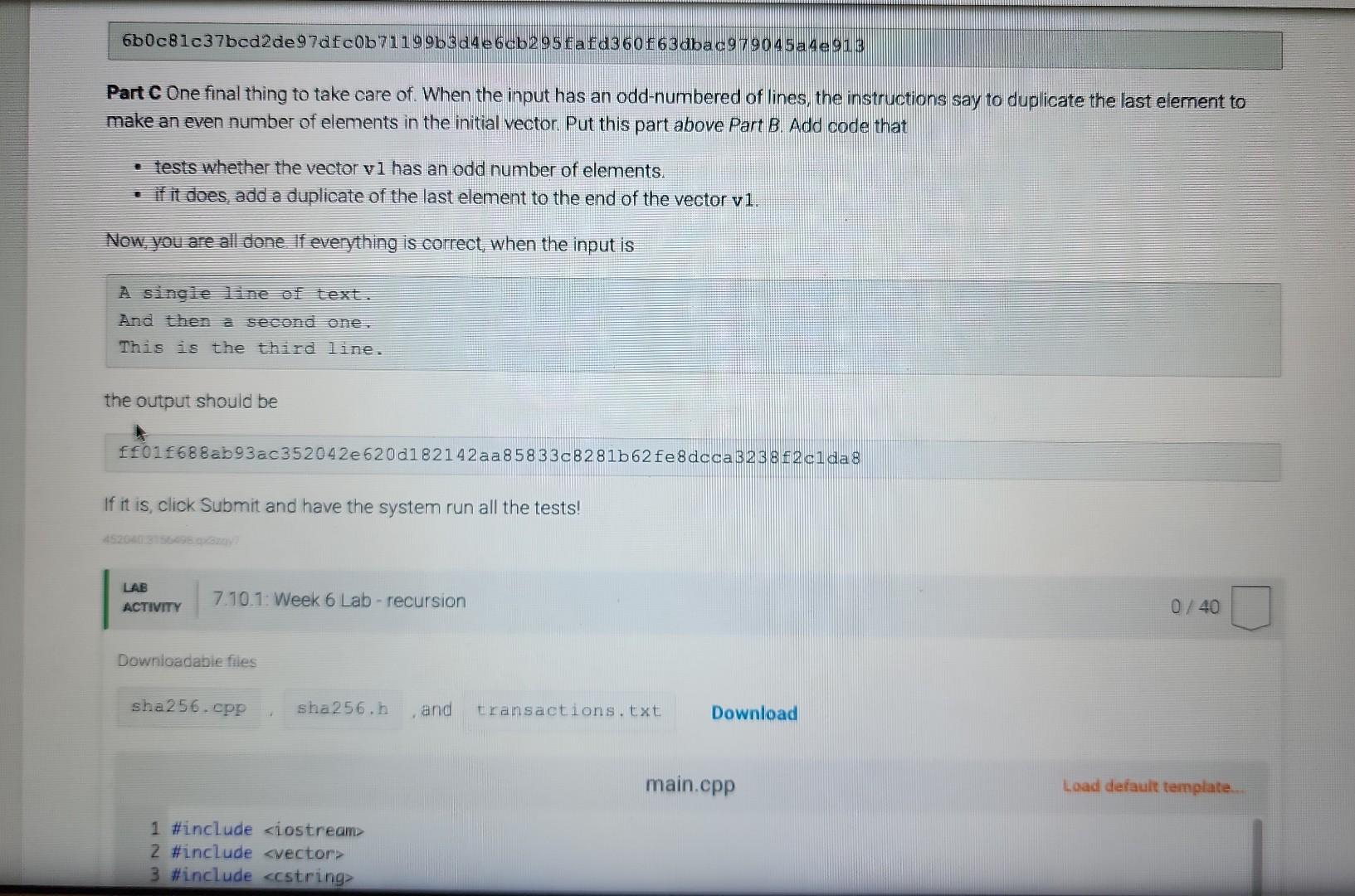
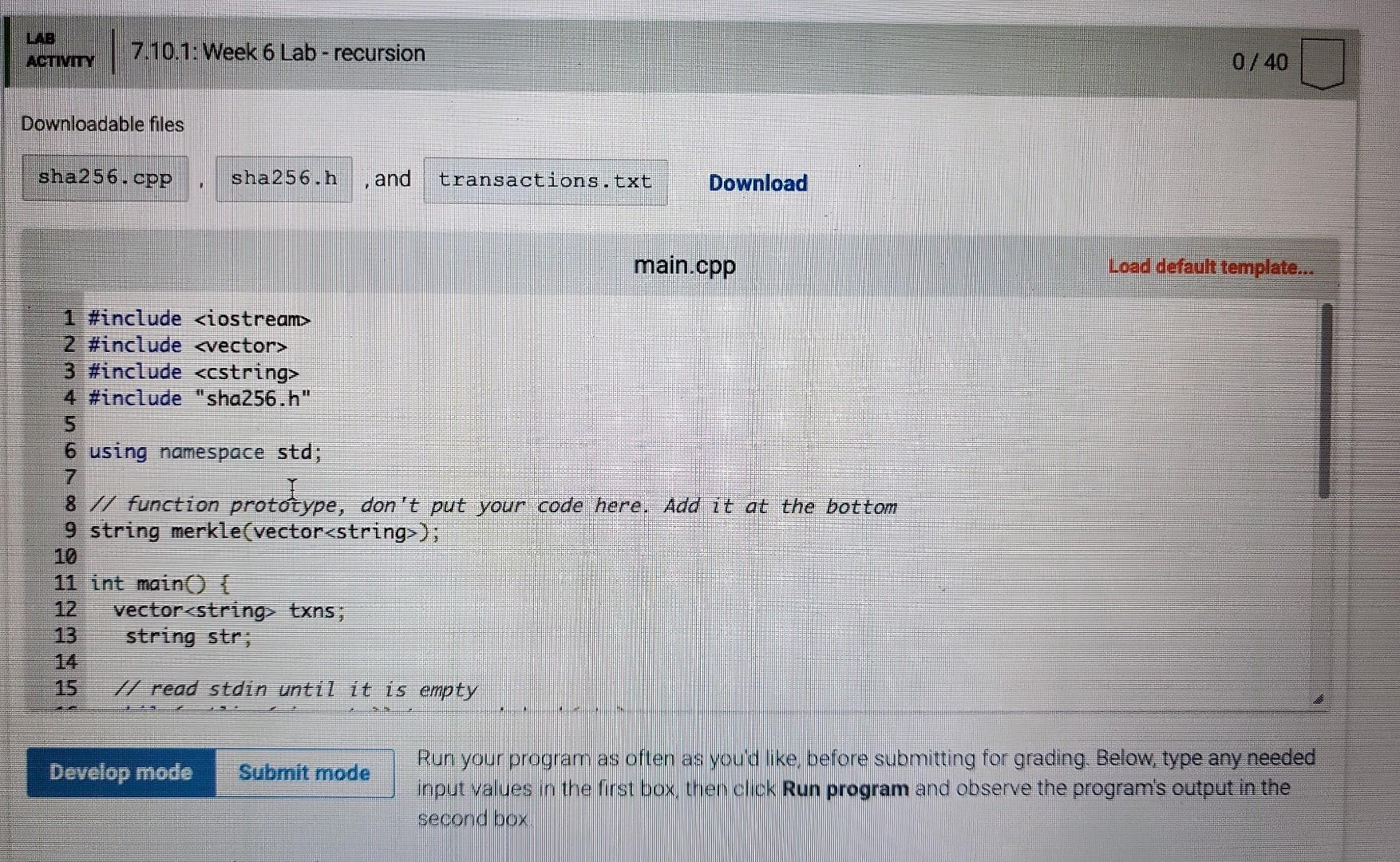
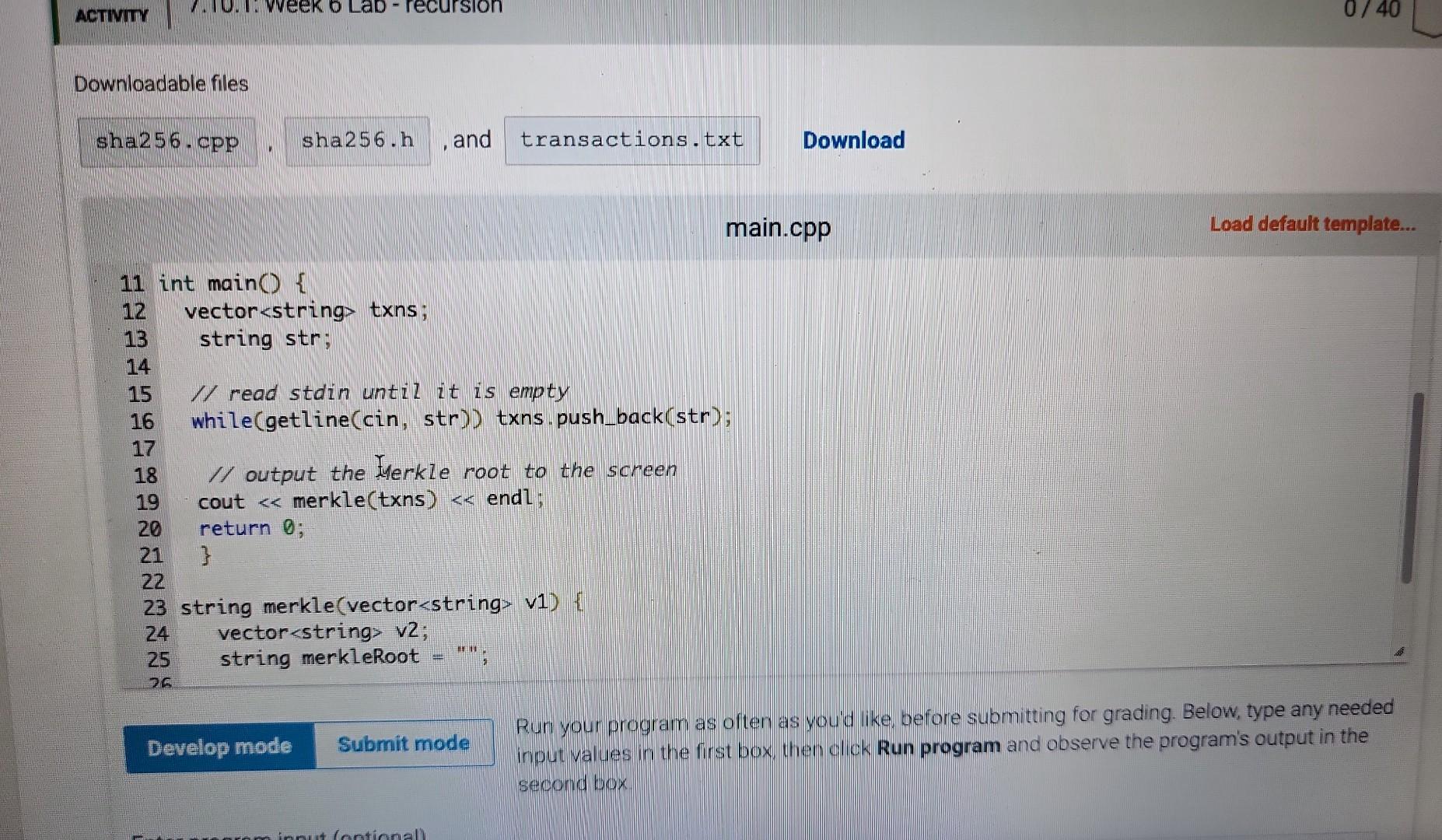
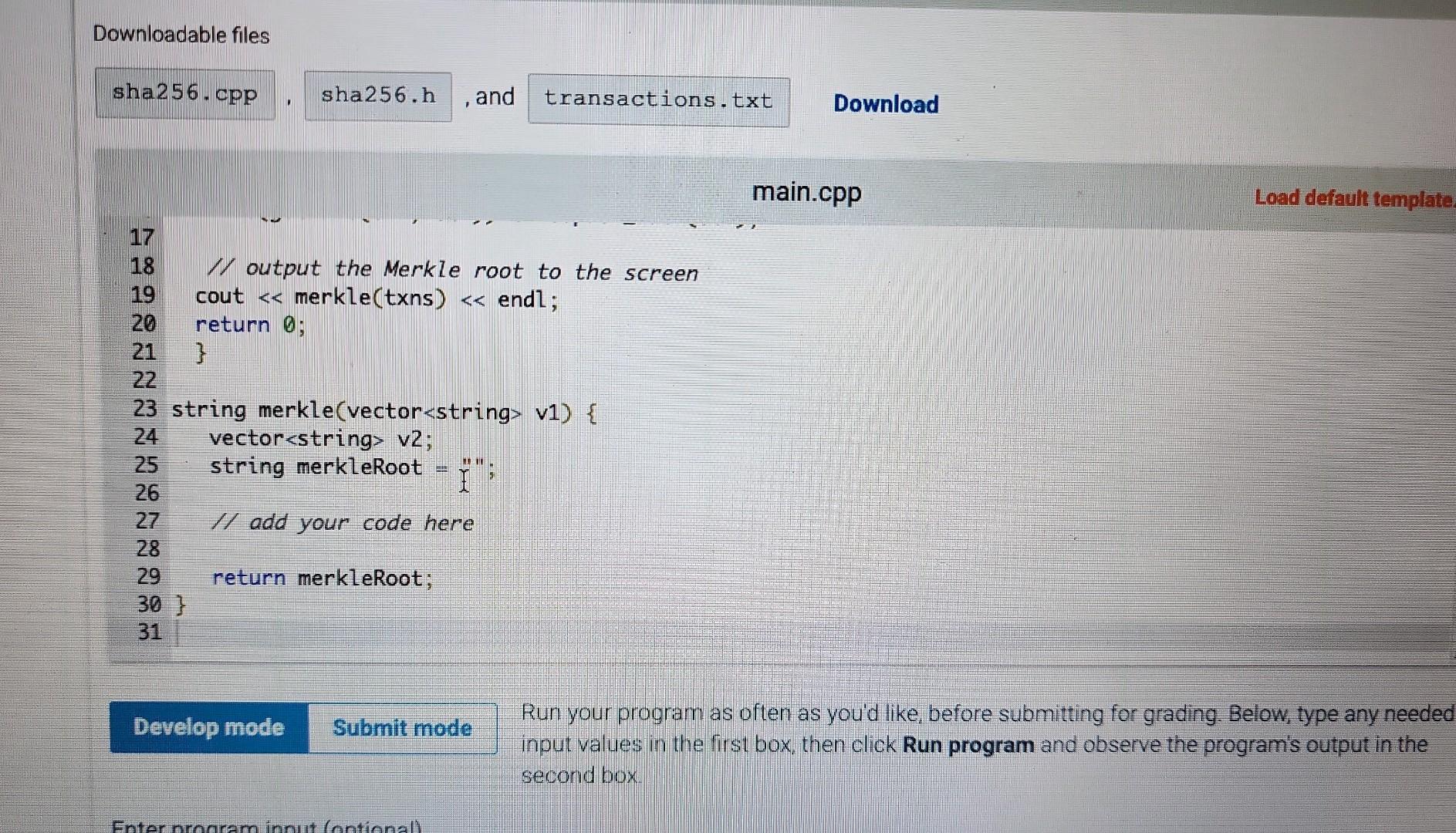
Learning Objectives - Use vector and string data types - Create and implement a recursive function to accomplish an algorithm Instructions Write a recursive function named merkle () that can create a Merkle tree of sha2 56 hashed strings. A Werk ce tree is a fundamental data Colision reststant hashing The entire main program is in the template. You will only need to complete writing the function named merkle The main program reads lines of text from user input and builds an array of these text strings. The strings can be any length and contains spaces, punctuation, etc. It the creates a (nearly) unique 256-bit hash of this file using a recursive function, and outputs it to the screen as a 64-character hexadecimal value (2256=1664) The recursive function you complete is called merkle () and will 1. hash each of the elements in the vector of strings individually, resulting in as many 64 -character hash strings, also stored as data type string. (e.g. 10 lines of text 10 hash strings) 2. concatenate the first with the second hash string, the third with the fourth, etc, resulting in one-half as many new text strings of 128 hexadecimal characters (concatenation of two 64 -character string). 3. hash each of these new text strings, resulting in as many new 64 hexadecimal hashes. 4. concatenate pairs again (returning to step 2, then step 3, then step 2, then step 3..). This recursion (steps 23232 ) continues until the there is only a single 64 character hexadecimal hash remaining Since there are no pairs left at this point to do step 2, the function will return the value merk leRoot where it is output to the screen. Hashes are created using the sha256 library quite simply as demonstrated in this example an arbitrary length string named s can be converted (hashed) into a 64 character string (at hexadecimal values) named s 2 via where both s1 and s2 are of data type string. Part A Recall from class lecture, that most recursive functions us an if else structure. Add an if else structure to the function. For the test condition, determine whether there is only 1 element in the vector v1. When that is the case (test condition evaluates to true), assign the variable merkleRoot to the sha256 hash of this vector element. Leave the else part of the structure completely empty for now (just a pair of curly brackets). At this point, if the input is (you can copy/paste this line into the Input box below) A single line of text. the output should be fff9f14639b5a80417b59d2d012f160e95e5c7394992874c5chdc8bac8539a45 Be careful when you copy/paste the line of text, there is not a return/enterewline at the end. The period is the final part of the input string. Parr B Now add code to the el se condition. A new vector will be used to store the concatenated strings, and it is already declared as a local variable in this function and named v2. Create a for loop that will go through the entire vector of strings two at a time. How many times should this loop occur? Since it works on 1 pair of text strings at a time, it will be one-half the size of the vector v1. (Recall you did something similar in the Feistel cipher lab). You will need to declare your own indexing variable for this loop. Within the for loop: generate a sha256 hash of the first two elements of the vector individually (use the for loop counter variable for the index), and then concatenate the strings together Recall that string concatenation can be done simply with the addition operator +. Finally, add this concatenated string to the vector v2 using the vector's push_back () function. Make sure you used the for loop index variable so that this loop will continue through all pairs in the vector. Thats all that goes in the for loop. After the loop is complete (but still within the else condition. make the function recursive by calling itself with the variable v2 as the parameter. Assign what is returned to the variable merkleRoot. At this point, if the input is A single line of text. Find then a second one. Part C One final thing to take care of. When the input has an odd-numbered of lines, the instructions say to duplicate the last element to make an even number of elements in the initial vector. Put this part above Part B. Add code that - tests whether the vector v1 has an odd number of elements. - if it does, add a duplicate of the last element to the end of the vector v1. Now, you are all done If everything is correct, when the input is A single line of text. And then a second one. This is the third line. the output should be ff01f688ab93ac352042e620d182142aa85833c8281b62fe8dcca3238f2c1da 8 If it is, click Submit and have the system run all the tests! \begin{tabular}{|l|l|l|} LAB & 7.tiviry & 7.10.1: Week 6 Lab - recursion \end{tabular} 0/40 Downioadabie files and 1 \#include 1 \#include 2 \#include 3 \#include 4 \#include "sha256.h" 5 6 using namespace std; 8ll function prototype, don't put your code here. Add it at the bottom 9 string merkle(vector string > ); 10 11 int main( ) 12 vectorstring txns; 13 string str; 14 If read stdin until it is empty Downloadable files sha256.CPP , sha256.h , and transactions.txt Download main.cpp Load default template.. Run your program as often as you'd like, before submitting for grading. Below, type any needed input values in the first box, then click Run program and observe the program's output in the second box Downloadable files , and 17 18 I/ output the Merkle root to the screen cout merkle (txns) endl; return \} string merkle(vector v1) \{ vectorv2 string merkleRoot =; If add your code here return merkleRoot; \}
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


