I have this question:
Asset valuation: Use the cost-based approach or the market-value based approach to calculate the relative value of the selected assets. You must justify any assumptions you make.
My asset must come from Liquid Assets in the Financial Department.
I am going with Accounts Receivable.
My question is would you use the cost-based approach or the market value-based approach to calculate the relative value of Accounts Receivable?
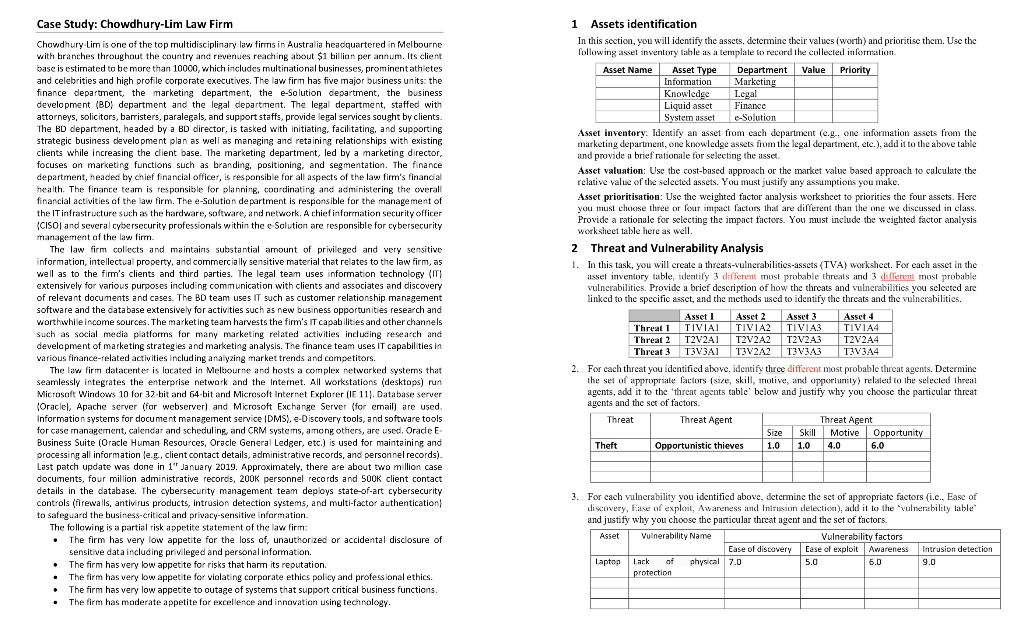 I am allowed to make an estimation but I'm not sure where to begin, but I am strictly looking for how to calculate the value. I have added the case study too for perusal.
I am allowed to make an estimation but I'm not sure where to begin, but I am strictly looking for how to calculate the value. I have added the case study too for perusal.
Case Study: Chowdhury-Lim Law Firm Chowdhury Lim is one of the top multidisciplinary law firms in Australia headquartered in Melbourne with branches throughout the country and revenues reaching about $1 billion per annum. Its client base is estimated to be more than 10000, which includes multinational businesses, prominent athletes and celebrities and high profile corporate executives. The law firm has five major business units: the finance department, the marketing department, the e-Solution department, the business development (BDI department and the legal department. The legal department staffed with attorneys, solicitors, barristers, paralegals, and support staffs, provide legal services sought by clients. The BD department, headed by a BD director, is tasked with initiating, facilitating, and supporting strategic business development plan as well as managing and retaining relationships with existing clients while increasing the client base. The marketing department, led by a marketing director, focuses on marketing functions such as branding, positioning, and segmentation. The finance department, headed by chief financial officer, is responsible for all aspects of the law firm's financial health. The finance team is responsible for planning, coordinating and administering the overall financial activities of the law firm. The e-Solution department is responsible for the management of the IT infrastructure such as the hardware, software, and network. A chief information Security officer (CISO and several cybersecurity professionals within the e Solution are responsible for cybersecurity management of the law firm. The law firm collects and maintains substantial amount of privileged and very sensitive information, intellectual property, and commercially sensitive material that relates to the law firm, as well as to the firm's clients and third parties. The legal team uses information technology (IT) extensively for various purposes including communication with clients and associates and discovery of relevant documents and cases. The BD team uses IT such as customer relationship management software and the database extensively for activities such as new business opportunities research and worthwhile income sources. The marketing team harvests the firm's IT capabilities and other channels such as social media platforms for many marketing related activities including research and development of marketing strategies and marketing analysis. The finance team uses IT capabilities in various finance-related activities including analyzing market trends and competitors. The law firm datacenter is located in Melbourne and hosts a complex networked systems that seamlessly integrates the enterprise network and the Internet. All workstations (desktops) run Microsoft Windows 10 for 32-bit and 64-bit and Microsoft Internet Explorer (E 11). Database server (Oraclel, Apache server (for webserver) and Microsoft Exchange Server (for email) are used. Information systems for document management service IDMS), e-Discovery tools, and software tools for case management, calendar and scheduling and CRM systems, among others, are used. Orade E Business Suite (Oracle Human Resources, Oracle General Ledger, etc.) is used for maintaining and processing all information leg.client contact details, administrative records, and personnel records) Last patch update was done in 1" January 2019. Approximately, there are about two million case documents, four million administrative records, 200K personnel records and SOOK client contact details in the database. The cybersecurity management team deploys state-of-art cybersecurity controls (firewalls, antivirus products, intrusion detection systems, and multi-factor authentication to safeguard the business-critical and privacy-sensitive information The following is a partial risk appetite statement of the law firm: The firm has very low appetite for the loss of unauthorized or accidental disclosure of Sensitive data including privileged and personal information The firm has very low appetite for risks that harm its reputation. The firm has very low appetite for violating corporate ethics policy and professional ethics. The firm has very low appetite to outage of systems that support critical business functions. The firm has moderate appetite for excellence and innovation using technology 1 Assets identification In this section, you will identify the assets, determine their values worth) and prioritise them. Use the following asset inventory table as a template to record the collected information Asset Name Asset Type Department Value Priority Information Marketing Knowledge Legal Liquid asset Finance System asset -Solution Asset inventory: Identify an asset from cach department (eg, one information assets from the marketing department, one knowledge assets from the legal department, etc.), add it to the above table and provide a brief rationale for selecting the asset Asset valuation: Use the cost-based approach or the market value based approach to calculate the relative value of the selected assets. You must justify any assumptions you make. Asset prioritisation: Use the weighted factor analysis worksheet to priorities the four assets. Here you must choose three or four impact factors that are different than the one we discussed in class. Provide a rationale for selecting the impact factors. You must include the weighted factor analysis worksheet table here as well. 2 Threat and Vulnerability Analysis 1. In this task, you will create a threats-vulnerabilities-assets (TVA) worksheet. For each asset in the itssel inventory table, identily 3 different most probable threats and 3 chifferent most probable vulnerabilities. Provide a brief description of how the threats and vulnerabilities you selected are linked to the specific asset, and the methods used to identify the threats and the vulnerabilities. Asset Asset? Asset 3 Asset 4 Threat! TIVIAI TIVIA2 TIVIA3 TIVIA4 Threat 2 T2V2A1 T2V2A2 T2V2A3 T2V2A4 Threat 3 T3V3A1 T3V2A2 T3V3A3 T3V3A4 2. For each threat you identified above, identify three different most probable threat agents. Determine the set of appropriate factors (size, skill, motive, and opportunity) related to the selected threat agents, add it to the threat agents table below and justify why you choose the particular threat agents and the set of factors Threat Threat Agent Threat Agent Size Skill Motive Opportunity Theft Opportunistic thieves 1.0 1.0 4.0 6.0 3. For cach vulnerability you identified above, determine the set of appropriate factors (i.c., Ease of discovery, Fase of exploit, Awareness and Intrusion detection), add it to the 'vulnerability table and justify why you choose the particular threat agent and the set of factors. Asset Vulnerability Name Vulnerability factors Ease of discovery Case of exploit Awareness Intrusion detection Laptop Lack of physical 70 5.0 5.0 protection Case Study: Chowdhury-Lim Law Firm Chowdhury Lim is one of the top multidisciplinary law firms in Australia headquartered in Melbourne with branches throughout the country and revenues reaching about $1 billion per annum. Its client base is estimated to be more than 10000, which includes multinational businesses, prominent athletes and celebrities and high profile corporate executives. The law firm has five major business units: the finance department, the marketing department, the e-Solution department, the business development (BDI department and the legal department. The legal department staffed with attorneys, solicitors, barristers, paralegals, and support staffs, provide legal services sought by clients. The BD department, headed by a BD director, is tasked with initiating, facilitating, and supporting strategic business development plan as well as managing and retaining relationships with existing clients while increasing the client base. The marketing department, led by a marketing director, focuses on marketing functions such as branding, positioning, and segmentation. The finance department, headed by chief financial officer, is responsible for all aspects of the law firm's financial health. The finance team is responsible for planning, coordinating and administering the overall financial activities of the law firm. The e-Solution department is responsible for the management of the IT infrastructure such as the hardware, software, and network. A chief information Security officer (CISO and several cybersecurity professionals within the e Solution are responsible for cybersecurity management of the law firm. The law firm collects and maintains substantial amount of privileged and very sensitive information, intellectual property, and commercially sensitive material that relates to the law firm, as well as to the firm's clients and third parties. The legal team uses information technology (IT) extensively for various purposes including communication with clients and associates and discovery of relevant documents and cases. The BD team uses IT such as customer relationship management software and the database extensively for activities such as new business opportunities research and worthwhile income sources. The marketing team harvests the firm's IT capabilities and other channels such as social media platforms for many marketing related activities including research and development of marketing strategies and marketing analysis. The finance team uses IT capabilities in various finance-related activities including analyzing market trends and competitors. The law firm datacenter is located in Melbourne and hosts a complex networked systems that seamlessly integrates the enterprise network and the Internet. All workstations (desktops) run Microsoft Windows 10 for 32-bit and 64-bit and Microsoft Internet Explorer (E 11). Database server (Oraclel, Apache server (for webserver) and Microsoft Exchange Server (for email) are used. Information systems for document management service IDMS), e-Discovery tools, and software tools for case management, calendar and scheduling and CRM systems, among others, are used. Orade E Business Suite (Oracle Human Resources, Oracle General Ledger, etc.) is used for maintaining and processing all information leg.client contact details, administrative records, and personnel records) Last patch update was done in 1" January 2019. Approximately, there are about two million case documents, four million administrative records, 200K personnel records and SOOK client contact details in the database. The cybersecurity management team deploys state-of-art cybersecurity controls (firewalls, antivirus products, intrusion detection systems, and multi-factor authentication to safeguard the business-critical and privacy-sensitive information The following is a partial risk appetite statement of the law firm: The firm has very low appetite for the loss of unauthorized or accidental disclosure of Sensitive data including privileged and personal information The firm has very low appetite for risks that harm its reputation. The firm has very low appetite for violating corporate ethics policy and professional ethics. The firm has very low appetite to outage of systems that support critical business functions. The firm has moderate appetite for excellence and innovation using technology 1 Assets identification In this section, you will identify the assets, determine their values worth) and prioritise them. Use the following asset inventory table as a template to record the collected information Asset Name Asset Type Department Value Priority Information Marketing Knowledge Legal Liquid asset Finance System asset -Solution Asset inventory: Identify an asset from cach department (eg, one information assets from the marketing department, one knowledge assets from the legal department, etc.), add it to the above table and provide a brief rationale for selecting the asset Asset valuation: Use the cost-based approach or the market value based approach to calculate the relative value of the selected assets. You must justify any assumptions you make. Asset prioritisation: Use the weighted factor analysis worksheet to priorities the four assets. Here you must choose three or four impact factors that are different than the one we discussed in class. Provide a rationale for selecting the impact factors. You must include the weighted factor analysis worksheet table here as well. 2 Threat and Vulnerability Analysis 1. In this task, you will create a threats-vulnerabilities-assets (TVA) worksheet. For each asset in the itssel inventory table, identily 3 different most probable threats and 3 chifferent most probable vulnerabilities. Provide a brief description of how the threats and vulnerabilities you selected are linked to the specific asset, and the methods used to identify the threats and the vulnerabilities. Asset Asset? Asset 3 Asset 4 Threat! TIVIAI TIVIA2 TIVIA3 TIVIA4 Threat 2 T2V2A1 T2V2A2 T2V2A3 T2V2A4 Threat 3 T3V3A1 T3V2A2 T3V3A3 T3V3A4 2. For each threat you identified above, identify three different most probable threat agents. Determine the set of appropriate factors (size, skill, motive, and opportunity) related to the selected threat agents, add it to the threat agents table below and justify why you choose the particular threat agents and the set of factors Threat Threat Agent Threat Agent Size Skill Motive Opportunity Theft Opportunistic thieves 1.0 1.0 4.0 6.0 3. For cach vulnerability you identified above, determine the set of appropriate factors (i.c., Ease of discovery, Fase of exploit, Awareness and Intrusion detection), add it to the 'vulnerability table and justify why you choose the particular threat agent and the set of factors. Asset Vulnerability Name Vulnerability factors Ease of discovery Case of exploit Awareness Intrusion detection Laptop Lack of physical 70 5.0 5.0 protection
 I am allowed to make an estimation but I'm not sure where to begin, but I am strictly looking for how to calculate the value. I have added the case study too for perusal.
I am allowed to make an estimation but I'm not sure where to begin, but I am strictly looking for how to calculate the value. I have added the case study too for perusal.





