i just uploaded some more files and also i uploaded grading rubric hopefully it works ans the HIM Department Privacy Policy breach Answer Sheet
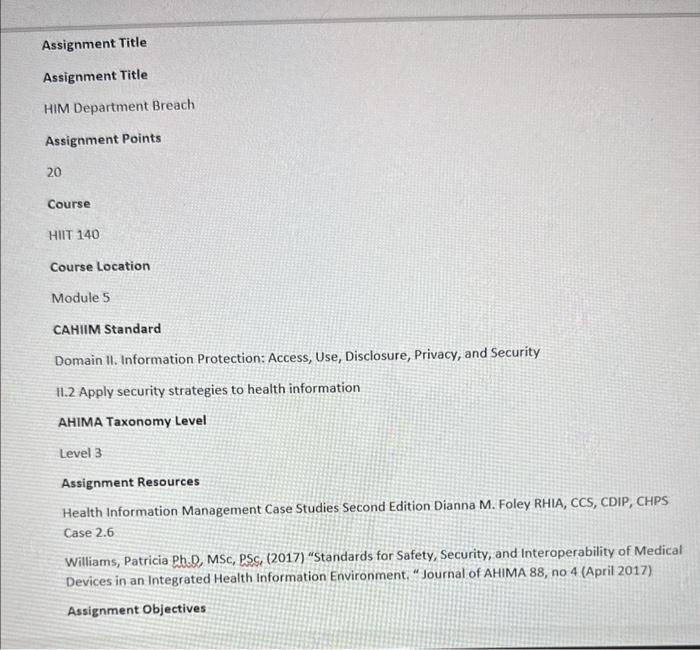
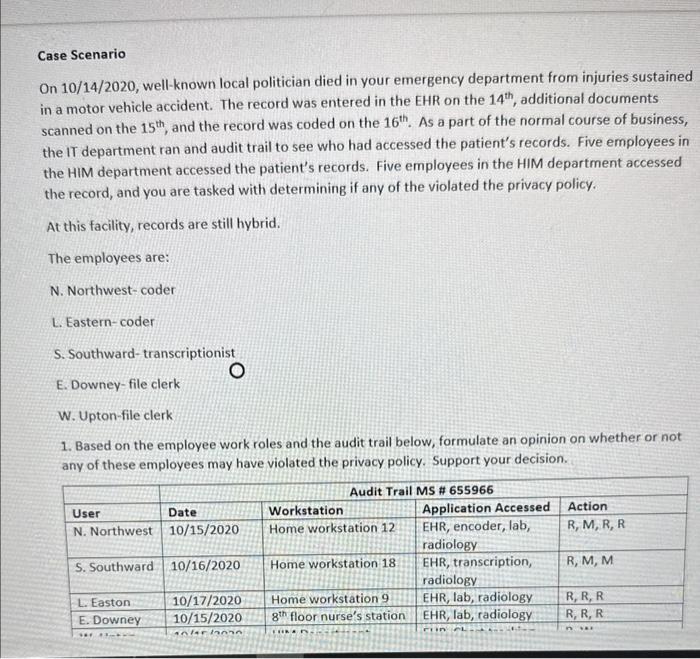
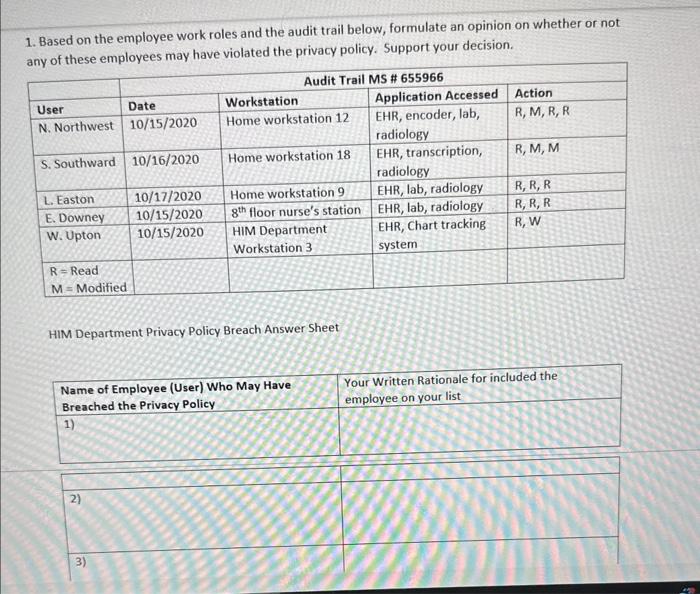
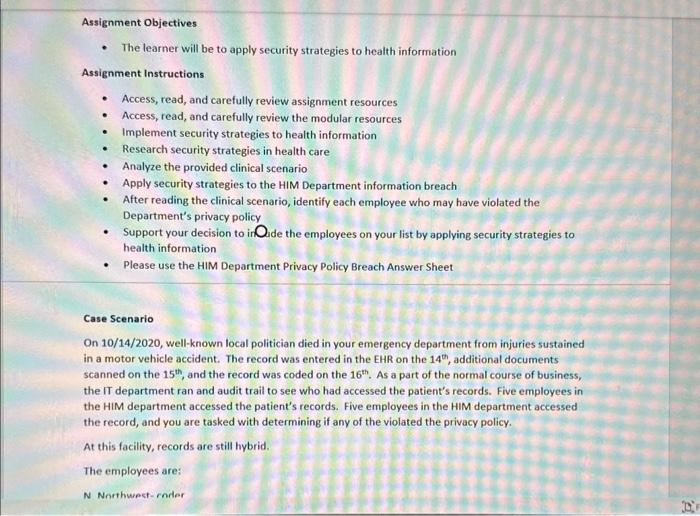
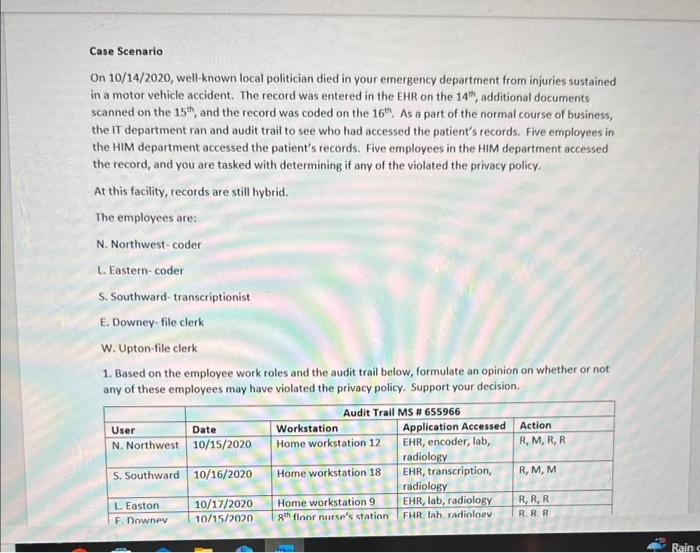
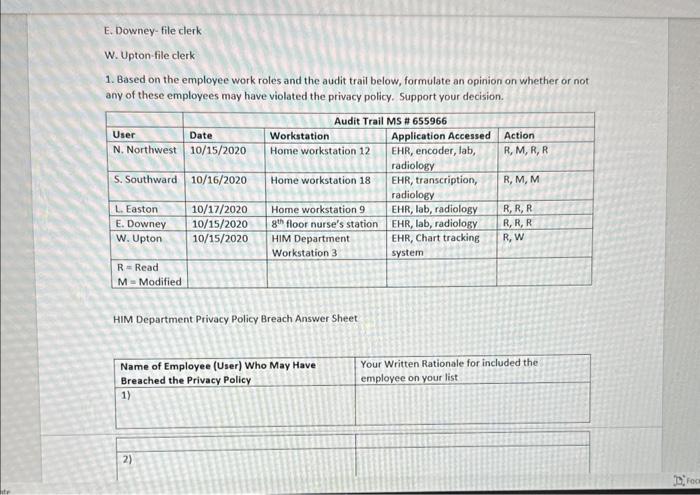
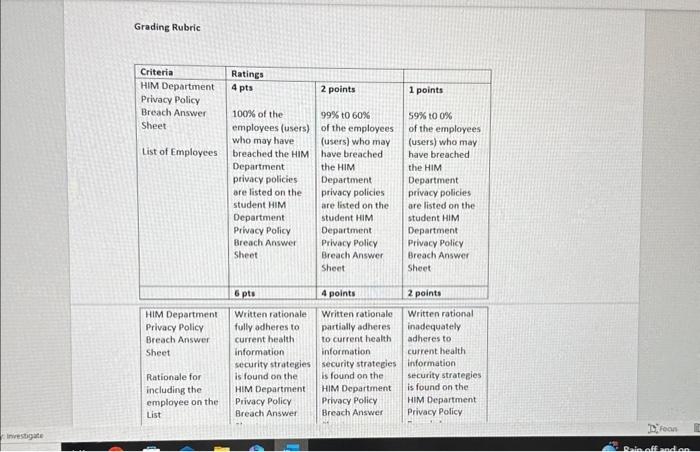
Case Scenario On 10/14/2020, well-known local politician died in your emergency department from injuries sustained in a motor vehicle accident. The record was entered in the EHR on the 14th, additional documents scanned on the 15th, and the record was coded on the 16th. As a part of the normal course of business, the IT department ran and audit trail to see who had accessed the patient's records. Five employees in the HIM department accessed the patient's records. Five employees in the HIM department accessed the record, and you are tasked with determining if any of the violated the privacy policy. At this facility, records are still hybrid. The employees are: N. Northwest-coder L. Eastern-coder S. Southward-transcriptionist E. Downey-file clerk W. Upton-file clerk 1. Based on the employee work roles and the audit trail below, formulate an opinion on whether or not any of these employees may have violated the privacy policy. Support your decision. 1. Based on the employee work roles and the audit trail below, formulate an opinion on whether or not an. nf these emblovees may have violated the privacy policy. Support your decision. HIM Department Privacy Policy Breach Answer Sheet \begin{tabular}{|l|l|} \hline NameofEmployee(User)WhoMayHaveBreachedthePrivacyPolicy & YourWrittenRationaleforincludedtheemployeeonyourlist \\ \hline 1) & \\ \hline \end{tabular} 2) 3) 4) 5) 6) Assignment Title Assignment Title HIM Department Breach Assignment Points 20 Course HIIT 140 Course Location Module 5 CAHIIM Standard Domain 11. Information Protection: Access, Use, Disclosure, Privacy, and Security 11.2 Apply security strategies to health information AHIMA Taxonomy Level Level 3 Assignment Resources Health Information Management Case Studies Second Edition Dianna M. Foley RHIA, CCS, CDIP, CHPS Case 2.6 Williams, Patricia Ph.D, MSc, PSc, (2017) "Standards for Safety, Security, and Interoperability of Medical Devices in an Integrated Health Information Environment, "Journal of AHIMA 88, no 4 (April 2017) Assignment Objectives - The learner will be to apply security strategies to health information Assignment Instructions - Access, read, and carefully review assignment resources - Access, read, and carefully review the modular resources - Implement security strategies to health information - Research security strategies in health care - Analyze the provided clinical scenario - Apply security strategies to the HIM Department information breach - After reading the clinical scenario, identify each employee who may have violated the Department's privacy policy - Support your decision to inQide the employees on your list by applying security strategies to health information - Please use the HIM Department Privacy Policy Breach Answer Sheet Case Scenario On 10/14/2020, well-known local politician died in your emergency department from injuries sustained in a motor vehicle accident. The record was entered in the EHR on the 14s, additional documents scanned on the 15th, and the record was coded on the 16th. As a part of the normal course of business, the IT department ran and audit trail to see who had accessed the patient's records. Five employees in the HIM department accessed the patient's records. Five employees in the HIM department accessed the record, and you are tasked with determining if any of the violated the privacy policy. At this facility, records are still hybrid. The employees are: N Nnethwest-mater Case Scenario On 10/14/2020, well-known local politician died in your emergency department from injuries sustained in a motor vehicle accident. The record was entered in the EHR on the 14th, additional documents scanned on the 15th, and the record was coded on the 16th. As a part of the normal course of business, the IT department ran and audit trail to see who had accessed the patient's records. Five employees in the HIM department accessed the patient's records. Five employees in the HIM department accessed the record, and you are tasked with determining if any of the violated the privacy policy. At this facility, records are still hybrid. The employees are: N. Northwest-coder L. Eastern-coder S. Southward-transcriptionist E. Downey-file clerk W. Upton-file clerk 1. Based on the employee work roles and the audit trail below, formulate an opinion on whether or not any of these employees may have violated the privacy policy. Support your decision. 1. Based on the employee work roles and the audit trail below, formulate an opinion on whether or not any of these employees may have violated the privacy policy. Support your decision. HIM Department Privacy Policy Breach Answer Sheet HIM Department Privacy Policy Breach Answer Sheet Grading Rubric