Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I need the whole code for this question in order to understand. Implement in any higher programming language ( preferably Python or Java ) the
I need the whole code for this question in order to understand.
Implement in any higher programming language preferably Python or
Java the following computer networks algorithms in step by step clear
presentation as tutorials, with all temporary and final results per step. All
algorithms reports should include evaluation of results, timing
comparisons and results, complexity estimations in different test cases
starting from simple topologiesconfigurations to larger scale
topologiesconfigurations a CRC Error Detection Algorithm with all details based on recent
literature review
b Internet Checksum Algorithm
Your evaluation program of these algorithms should check their capability to detect
burst errors in long messages.
Your messages will be random messages of
bytes. For at least messages for each of the above mentioned lengths you
should apply CRC error detection and Internet Checksum algorithms.
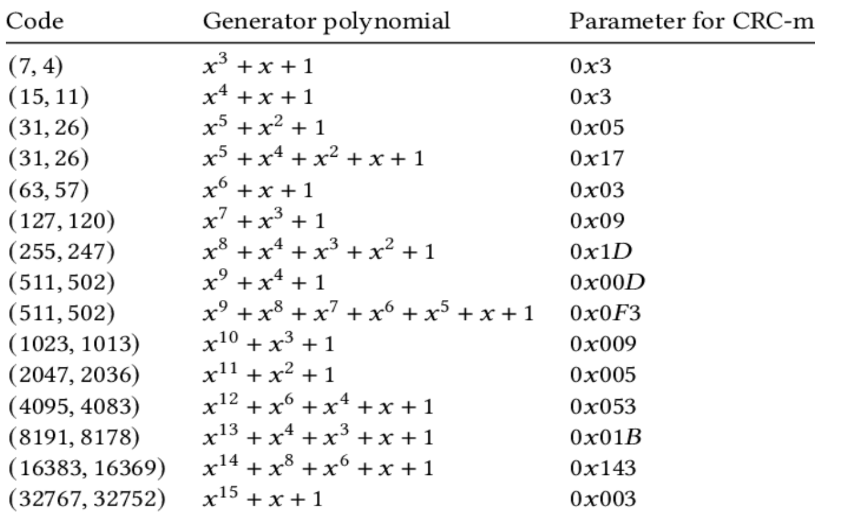
Regarding CRC error detection you should compare the capabilities for error
detection of the CRC generator polynomials. The following CRC polynomials could
be used. But you could extend this list creating your own ones too. The capabilities for error detection you should compare are for burst random
error patterns changing of the number of bits of each message and for
every polynomial including CRC bits We would like to outline in tables these
results so that to know each polynomial attempted what percentages of error
patterns can detect in the ranges regarding the
number of bits changes by the error patterns in the messages This should be done
for each generator polynomial for all lengths of messages categorized as above, that
is messages and bytes.
The same exactly evaluation should be done for internet checksum and bits
algorithms.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


