Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I need to match the above items with the following options. *Options: A. Access modes B. Object C. Granularity D. Least (limited) privilege E. Neutrality
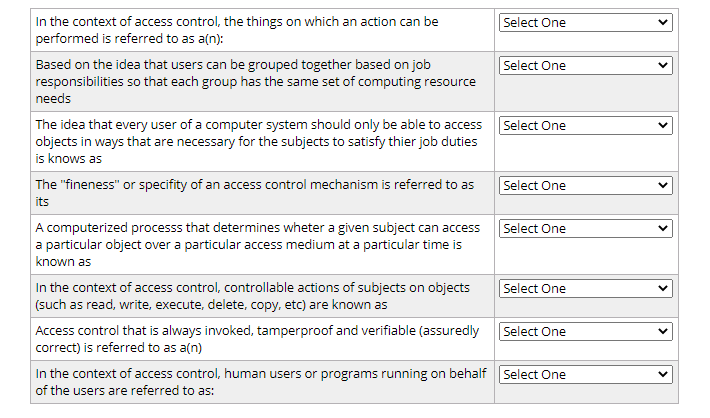
I need to match the above items with the following options.
*Options:
A. Access modes B. Object C. Granularity D. Least (limited) privilege E. Neutrality F. Access control G. Reference monitor H. Subjects I. Perfect forward security J. Role-based access control K. Security reference
In the context of access control the things on which an action can be Select One performed is referred to as a(n): Based on the idea that users can be grouped together based on job Select One responsibilities so that each group has the same set of computing resource needs The idea that every user of a computer system should only be able to access Select One objects in ways that are necessary for the subjects to satisfy thier job duties is knows as The "fineness" or specifity of an access control mechanism is referred to as Select One its A computerized process that determines wheter a given subject can access Select One a particular object over a particular access medium at a particular time is known as In the context of access control, controllable actions of subjects on objects Select One (such as read, write, execute, delete, copy, etc) are known as Access control that is always invoked, tamperproof and verifiable (assuredly Select One correct) is referred to as a(n) In the context of access control, human users or programs running on behalf Select One of the users are referred to as:Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


