Answered step by step
Verified Expert Solution
Question
1 Approved Answer
i want soulution with out code Submission guidelines: The assignment must be submitted by the deadline (earlier submissions are encouraged) in PDF format through Blackboard
i want soulution with out code 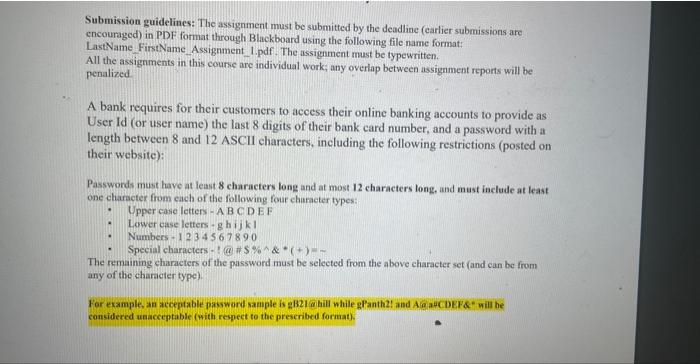
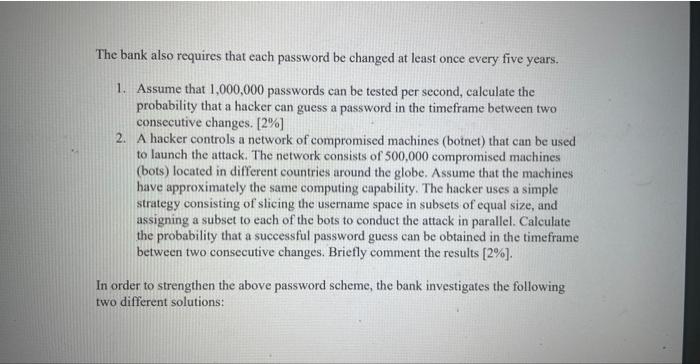
Submission guidelines: The assignment must be submitted by the deadline (earlier submissions are encouraged) in PDF format through Blackboard using the following file name format: LastName FirstName. Assignment_1.pdf. The assignment must be typewritten. All the assignments in this course are individual work; any overlap between assignment reports will be penalized. A bank requires for their customers to access their online banking accounts to provide as User Id (or user name) the last 8 digits of their bank card number, and a password with a length between 8 and 12 ASCII characters, including the following restrictions (posted on their website): Passwords must have at least 8 characters long and at most 12 characters long, and must include at least one character from each of the following four chancter types: - Upper case letters - A B C D EF - Lower case letters g h i kkl - Numbers 1234567890 - Special characters 1(a)$&(+)= The remaining characters of the password must be selected from the above character set (and can be from any of the character type). For example, an acceptable password sample is aB21 ahill while gPanth2! and AGg aHCDEF\&" will be considered unacceptable (xith respect to the preseribed format). The bank also requires that each password be changed at least once every five years. 1. Assume that 1,000,000 passwords can be tested per second, calculate the probability that a hacker can guess a password in the timeframe between two consecutive changes. [2\%] 2. A hacker controls a network of compromised machines (botnet) that can be used to launch the attack. The network consists of 500,000 compromised machines (bots) located in different countries around the globe. Assume that the machines have approximately the same computing capability. The hacker uses a simple strategy consisting of slicing the username space in subsets of equal size, and assigning a subset to each of the bots to conduct the attack in parallel. Calculate the probability that a successful password guess can be obtained in the timeframe between two consecutive changes. Briefly comment the results [2%]. In order to strengthen the above password scheme, the bank investigates the following two different solutions 

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


