Answered step by step
Verified Expert Solution
Question
1 Approved Answer
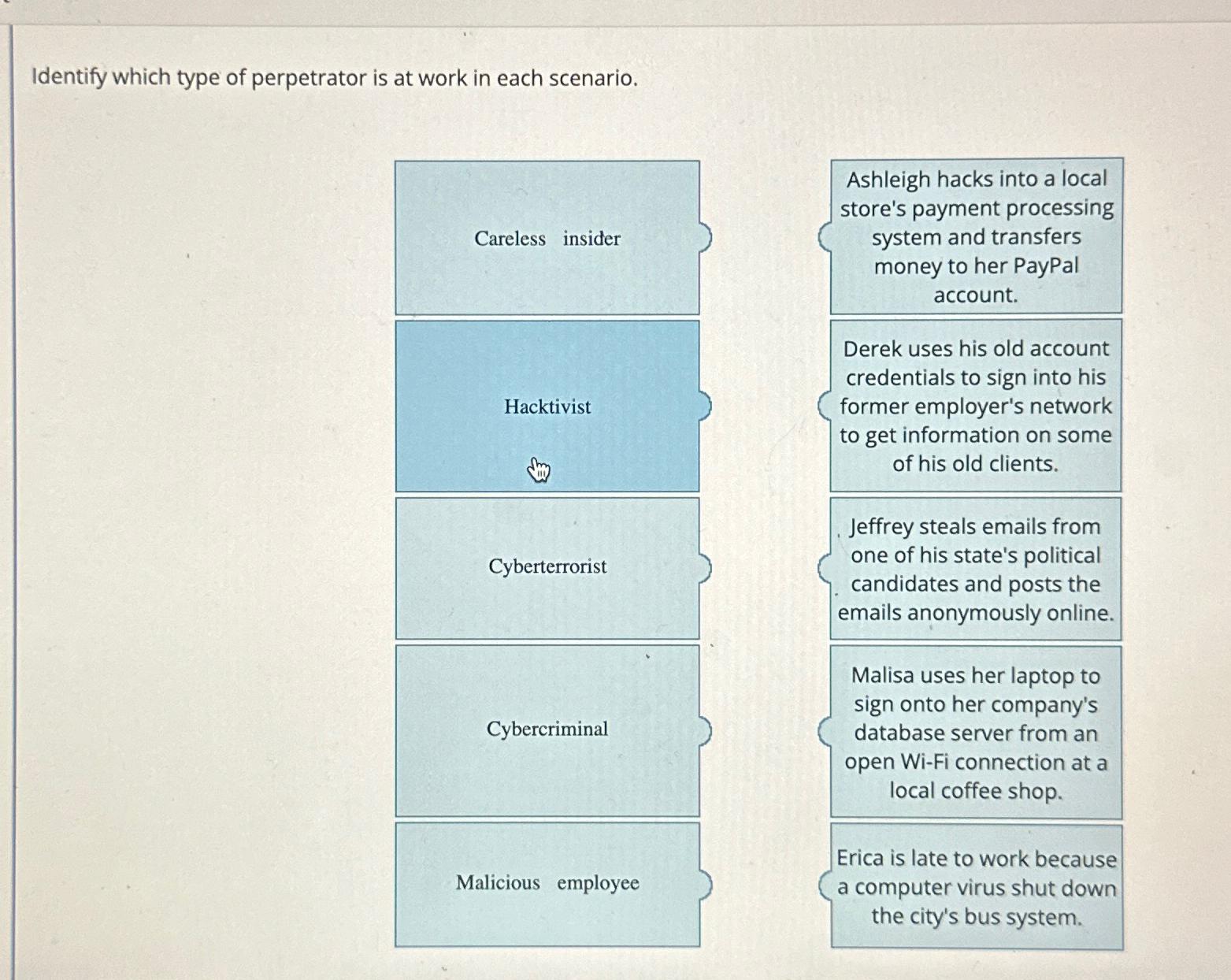
Identify which type of perpetrator is at work in each scenario. table [ [ Careless insider, table [ [ Ashleigh hacks into a
Identify which type of perpetrator is at work in each scenario.
tableCareless insider,tableAshleigh hacks into a localstores payment processingsystem and transfersmoney to her PayPalaccountHacktivisttableDerek uses his old accountcredentials to sign into hisformer employer's networkto get information on someof his old clients.CyberterroristtableJeffrey steals emails fromone of his state's politicalcandidates and posts theemails anonymously online.CybercriminaltableMalisa uses her laptop tosign onto her company'sdatabase server from anopen WiFi connection at alocal coffee shop.Ealicious employee,a computer virus shut down,the city's bus system.,a late to work because,
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


