Question
I'm having issues how to even work this problem out. All the information that has been attached also has pics that are needed. I'm stuck
I'm having issues how to even work this problem out. All the information that has been attached also has pics that are needed. I'm stuck with not knowing any of this information
Problem 1.
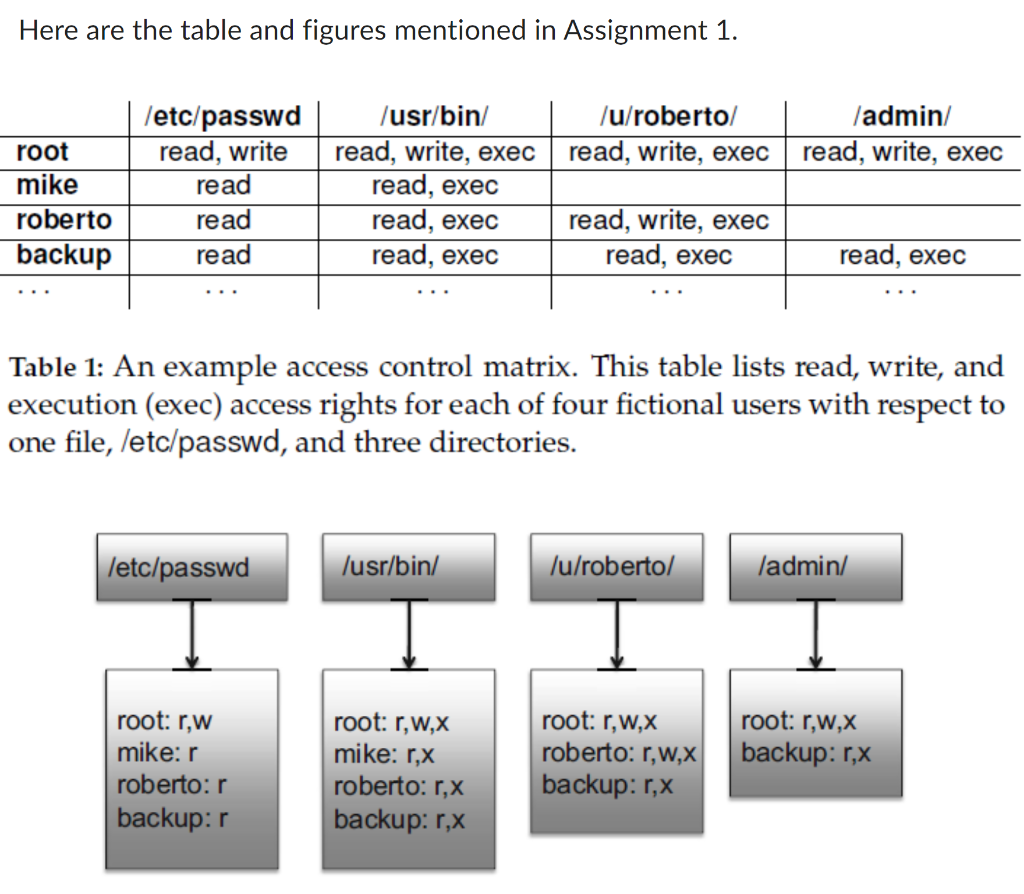
Access Control Assumption: Privileges: read ("R"), write ("W"), execute ("X") Resources: - Document files: syllabus.doc, ch1.ppt - Image files: trees.jpg, jkim.png, csci563.gif - Binary files: prog1.exe, chrome.exe, wireshark.exe Access permissions (for users A, B, and C): - A has privilege to read all image files. - C has privilege to read and write all document files. - A and B have privilege to read "syllabus.doc" - A and C have privilege to read and execute "prog1.exe", "chrome.exe". - B and C have privilege to read csci563.gif. a. Construct the corresponding access control matrix.
To answer, use the format in Table 1.1 in the textbook. b. Construct the corresponding access control list.
To answer, use the format in Figure 1.5 in the textbook. c. Construct the corresponding capabilities list. To answer, use the format in Figure 1.6 in the textbook.
Problem 2. Vernam Cipher
Suppose the following table for encoding and decoding.
| Letter | A | E | Y | M | O | R | H | L |
| Binary | 000 | 001 | 010 | 011 | 100 | 101 | 110 | 111 |
Assume a message M is 'MORAL' and the key is 'HELLO'. What is the ciphertext C? Show your work.
Now assume a ciphertext C is 'HYMYR' and the key is 'HELLO'. What is the plaintext P? Show your work.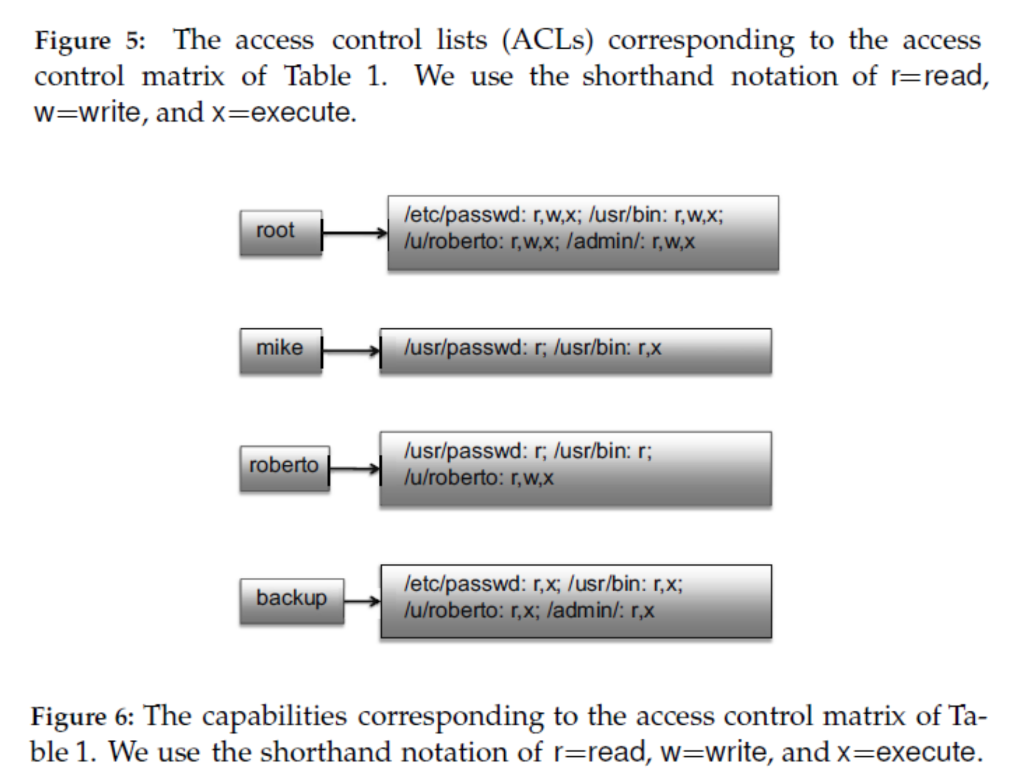
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


