

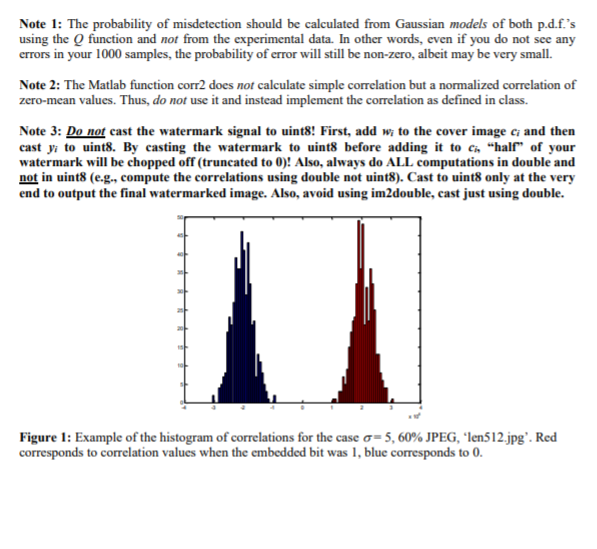
Implement robust spread-spectrum watermarking and test its performance. The purpose of this assignment is to get some experience with spread-spectrum watermarks and see for yourself how robust the watermarks are to various image processing operations (attack channels). Input: Xa grayscale image (matrix of uint8) Bitit to be embedded (0 or 1) Sigma-standard deviation of the watermark signal wi ~ M0,02) Key watermark key used to initialize the PRNG (randn) Watermarked uint8 image Y Output: X Y = imread(.myimage.jpg); Bit-I; Sigma = 5; Key-6574: SSEmb(X, Bit, Sigma, Key); Input: Ywatermarked (and attacked/processed) image (what we denote ltildety!) Sigma-standard deviation of the watermark signal w-M0.c.) Key watermark key used to initialize the PRNG (randn) Bi extracted bit (0 or 1) Output:Bit Use the alternative uninformed detector (see 'robust watermarking.pdf on Blackboard and/or your class notes), which is implemented as a correlation normalized by n, the signal length (the number of pixels). Here, , is the estimate of the cover image obtained from the attacked image using the Wiener filter, -wiener2) Write another m-function SSTest.m that will embed one bit into the same image using l keys. Each time, subject the watermarked image to a series of attacks and count how many times the bit was extracted correctly. You can embed either a random bit or 500 "1"s and 500 "O"s 1000 different The attacks must contain the following (but you are welcome to try other attacks- we will discuss the results later in the class): JPEG compression (quality 90, 60, and 5) implement as imwrite(Y, 'watermarked.jpg', 'jpg', quality", 90), then read the compressed image using -im read(.watermarked.jpg.); Histogram equalization implement as Y-imadjust(Y): Gamma correction with = 0.1 and 5 * implement as Y = imadjust(Y, [], [], - Denoising with a Wiener filter with a 3x3 window and Matlab-default noise variance implement as Y-wiener2(Y); -Median filtering with a 3x3 window implement as Y medfilt2(Y, [3 3]); -Resampling by a factor of 2 - downsample using imresize.m, then upsample back before extracting the bit * implement as Y = mresize(imresize(Y, 1 /2), 2); Run the experiments for the test images 'len256.bmp" and len512jpg available from Blackboard. Report the number of correct watermark bit detections in a table. Produce two separate tables for both len256.bmp' and 'len512.jpg Attack JPG 9 JPG 60 JPG 5 -list. to 16 size Additionally, produce the following histogram of correlations for all 1000 attempts for five cases, each case consisting of a particular choice of test image, and distortion. An example for the case -5, 60% quality JPEG, 'len512.jpg, is in Figure I below. In blue is depicted the histogram of correlations when the embedded bit is 0, the red histogram corresponds to the embedded bits 1. In this case, there is obviously no misdetection in all 1000 trials because no red appears below zero and no blue appears above zero. The choice of the five cases is up to you. Try to select the cases so that you demonstrate something interesting. Comment on it. For all five cases, assume that the distribution of the test statistic po.p is Gaussian and compute its parameters (the mean and the variance) as their sample mean where os and Pus are the ith correlations when embedding a 0 or 1, No and Ni are the number of times you embedded a 0 or 1, and their sample variance: Then, compute the probability of misdetection i.e., bit 0 is detected as1 or bit 1 is detected as 0) where Qr)is the O function. To be completely clear, I am asking for a table with five rows, each row corresponding to one selected case, and in cach row will be the values ofA-Pn . . and Pr(Error). If the error probability ends up zero, estimate its value using the asymptotic expression for Qur) we derived in the class (remember, the error probability must be always positive). Note 1: The probability of misdetection should be calculated from Gaussian models of both p.d.f.'s using the Q function and not from the experimental data. In other words, even if you do not see any errors in your 1000 samples, the probability of errwlstill be non-zero, albeit may be very small. Note 2: The Matlab function corr2 does not calculate simple correlation but a normalized correlation of zero-mean values. Thus, do not use it and instead implement the correlation as defined in class. Note 3: Do not cast the watermark signal to uint8! First, add wi to the cover image ci and then cast y to uint8. By casting the watermark to uint8 before adding it to c "half of your watermark will be chopped off (truncated to 0)! Also, always do ALL computations in double and not in uint8 (e.g., compute the correlations using double not uint8). Cast to uint8 only at the very end to output the final watermarked image. Also, avoid using im2double, cast just using double. Figure 1: Example of the histogram of correlations for the case . 5, 60% JPEG, len512.jpg. Red corresponds to correlation values when the embedded bit was 1, blue corresponds to 0 Implement robust spread-spectrum watermarking and test its performance. The purpose of this assignment is to get some experience with spread-spectrum watermarks and see for yourself how robust the watermarks are to various image processing operations (attack channels). Input: Xa grayscale image (matrix of uint8) Bitit to be embedded (0 or 1) Sigma-standard deviation of the watermark signal wi ~ M0,02) Key watermark key used to initialize the PRNG (randn) Watermarked uint8 image Y Output: X Y = imread(.myimage.jpg); Bit-I; Sigma = 5; Key-6574: SSEmb(X, Bit, Sigma, Key); Input: Ywatermarked (and attacked/processed) image (what we denote ltildety!) Sigma-standard deviation of the watermark signal w-M0.c.) Key watermark key used to initialize the PRNG (randn) Bi extracted bit (0 or 1) Output:Bit Use the alternative uninformed detector (see 'robust watermarking.pdf on Blackboard and/or your class notes), which is implemented as a correlation normalized by n, the signal length (the number of pixels). Here, , is the estimate of the cover image obtained from the attacked image using the Wiener filter, -wiener2) Write another m-function SSTest.m that will embed one bit into the same image using l keys. Each time, subject the watermarked image to a series of attacks and count how many times the bit was extracted correctly. You can embed either a random bit or 500 "1"s and 500 "O"s 1000 different The attacks must contain the following (but you are welcome to try other attacks- we will discuss the results later in the class): JPEG compression (quality 90, 60, and 5) implement as imwrite(Y, 'watermarked.jpg', 'jpg', quality", 90), then read the compressed image using -im read(.watermarked.jpg.); Histogram equalization implement as Y-imadjust(Y): Gamma correction with = 0.1 and 5 * implement as Y = imadjust(Y, [], [], - Denoising with a Wiener filter with a 3x3 window and Matlab-default noise variance implement as Y-wiener2(Y); -Median filtering with a 3x3 window implement as Y medfilt2(Y, [3 3]); -Resampling by a factor of 2 - downsample using imresize.m, then upsample back before extracting the bit * implement as Y = mresize(imresize(Y, 1 /2), 2); Run the experiments for the test images 'len256.bmp" and len512jpg available from Blackboard. Report the number of correct watermark bit detections in a table. Produce two separate tables for both len256.bmp' and 'len512.jpg Attack JPG 9 JPG 60 JPG 5 -list. to 16 size Additionally, produce the following histogram of correlations for all 1000 attempts for five cases, each case consisting of a particular choice of test image, and distortion. An example for the case -5, 60% quality JPEG, 'len512.jpg, is in Figure I below. In blue is depicted the histogram of correlations when the embedded bit is 0, the red histogram corresponds to the embedded bits 1. In this case, there is obviously no misdetection in all 1000 trials because no red appears below zero and no blue appears above zero. The choice of the five cases is up to you. Try to select the cases so that you demonstrate something interesting. Comment on it. For all five cases, assume that the distribution of the test statistic po.p is Gaussian and compute its parameters (the mean and the variance) as their sample mean where os and Pus are the ith correlations when embedding a 0 or 1, No and Ni are the number of times you embedded a 0 or 1, and their sample variance: Then, compute the probability of misdetection i.e., bit 0 is detected as1 or bit 1 is detected as 0) where Qr)is the O function. To be completely clear, I am asking for a table with five rows, each row corresponding to one selected case, and in cach row will be the values ofA-Pn . . and Pr(Error). If the error probability ends up zero, estimate its value using the asymptotic expression for Qur) we derived in the class (remember, the error probability must be always positive). Note 1: The probability of misdetection should be calculated from Gaussian models of both p.d.f.'s using the Q function and not from the experimental data. In other words, even if you do not see any errors in your 1000 samples, the probability of errwlstill be non-zero, albeit may be very small. Note 2: The Matlab function corr2 does not calculate simple correlation but a normalized correlation of zero-mean values. Thus, do not use it and instead implement the correlation as defined in class. Note 3: Do not cast the watermark signal to uint8! First, add wi to the cover image ci and then cast y to uint8. By casting the watermark to uint8 before adding it to c "half of your watermark will be chopped off (truncated to 0)! Also, always do ALL computations in double and not in uint8 (e.g., compute the correlations using double not uint8). Cast to uint8 only at the very end to output the final watermarked image. Also, avoid using im2double, cast just using double. Figure 1: Example of the histogram of correlations for the case . 5, 60% JPEG, len512.jpg. Red corresponds to correlation values when the embedded bit was 1, blue corresponds to 0









