Question
In the four years since the sixth edition of this book was published, the field has seen contin- ued innovations and improvements. In this new
In the four years since the sixth edition of this book was published, the field has seen contin- ued innovations and improvements. In this new edition, I try to capture these changes while maintaining a broad and comprehensive coverage of the entire field. To begin this process of revision, the sixth edition of this book was extensively reviewed by a number of professors who teach the subject and by professionals working in the field. The result is that, in many places, the narrative has been clarified and tightened, and illustrations have been improved. Beyond these refinements to improve pedagogy and user-friendliness, there have been substantive changes throughout the book. Roughly the same chapter organization has been retained, but much of the material has been revised and new material has been added. The most noteworthy changes are as follows: ? Fundamental security design principles: Chapter 1 includes a new section discussing the security design principles listed as fundamental by the National Centers of Academic Excellence in Information Assurance/Cyber Defense, which is jointly sponsored by the U.S. National Security Agency and the U.S. Department of Homeland Security. ? Attack surfaces and attack trees: Chapter 1 includes a new section describing these two concepts, which are useful in evaluating and classifying security threats. ? Number theory coverage: The material on number theory has been consolidated into asingle chapter, Chapter 2. This makes for a convenient reference. The relevant portions of Chapter 2 can be assigned as needed. ? Finite fields: The chapter on finite fields has been revised and expanded with addi- tional text and new figures to enhance understanding. ? Format-preserving encryption: This relatively new mode of encryption is enjoying increasing commercial success. A new section in Chapter 7 covers this method. ? Conditioning and health testing for true random number generators: Chapter 8 now provides coverage of these important topics. ? User authentication model: Chapter 15 includes a new description of a general model for user authentication, which helps to unify the discussion of the various approaches to user authentication. ? Cloud security: The material on cloud security in Chapter 16 has been updated and expanded to reflect its importance and recent developments. ? Transport Layer Security (TLS): The treatment of TLS in Chapter 17 has been updated, reorganized to improve clarity, and now includes a discussion of the new TLS version1.3. ? Email Security: Chapter 19 has been completely rewritten to provide a comprehensive and up-to-date discussion of email security. It includes: ? New: discussion of email threats and a comprehensive approach to email security. ?
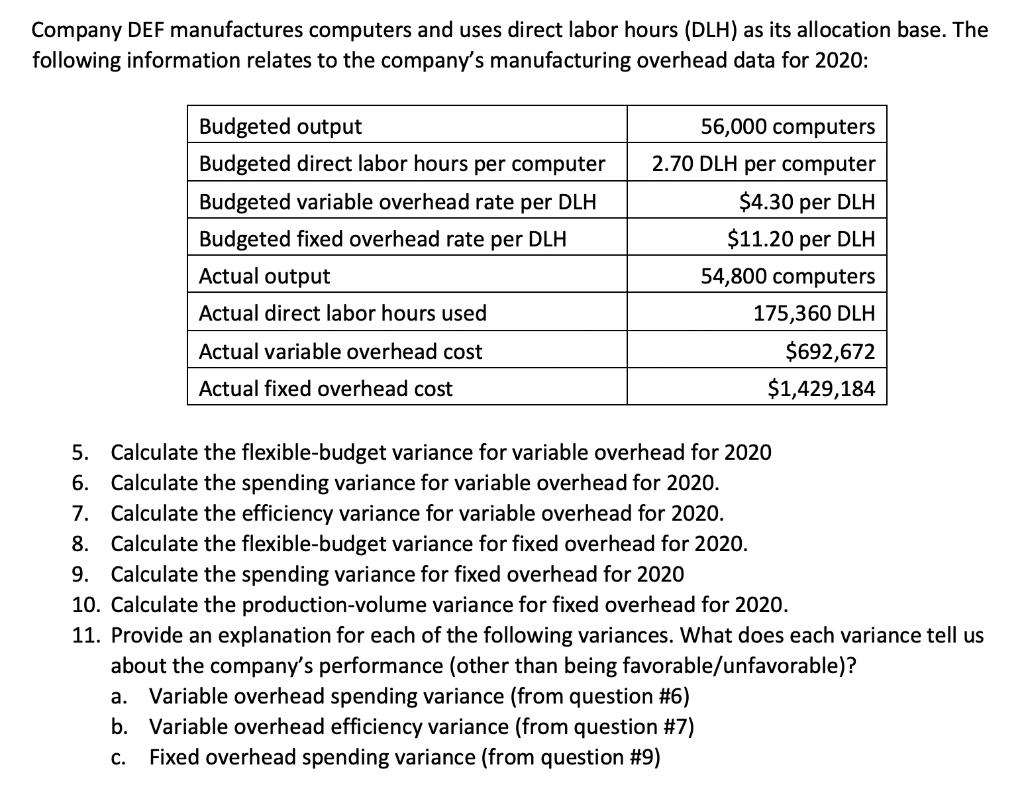
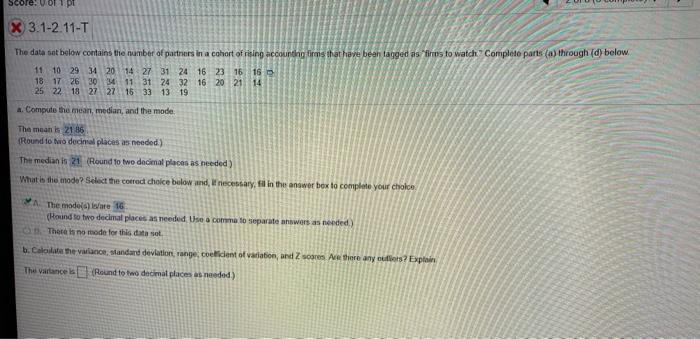
Company DEF manufactures computers and uses direct labor hours (DLH) as its allocation base. The following information relates to the company's manufacturing overhead data for 2020: Budgeted output Budgeted direct labor hours per computer Budgeted variable overhead rate per DLH Budgeted fixed overhead rate per DLH Actual output Actual direct labor hours used Actual variable overhead cost Actual fixed overhead cost 56,000 computers 2.70 DLH per computer $4.30 per DLH $11.20 per DLH 54,800 computers 175,360 DLH $692,672 $1,429,184 5. 6. Calculate the flexible-budget variance for variable overhead for 2020 Calculate the spending variance for variable overhead for 2020. Calculate the efficiency variance for variable overhead for 2020. 7. 8. Calculate the flexible-budget variance for fixed overhead for 2020. 9. Calculate the spending variance for fixed overhead for 2020 10. Calculate the production-volume variance for fixed overhead for 2020. 11. Provide an explanation for each of the following variances. What does each variance tell us about the company's performance (other than being favorable/unfavorable)? a. Variable overhead spending variance (from question #6) b. Variable overhead efficiency variance (from question #7) C. Fixed overhead spending variance (from question #9)
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


