In the image below, a variant of the CFB mode is proposed which encrypts individual bytes. Draw a block diagram for this mode when using AES as block cipher. Indicate the width (in bit) of each line in your diagram.
***Image***
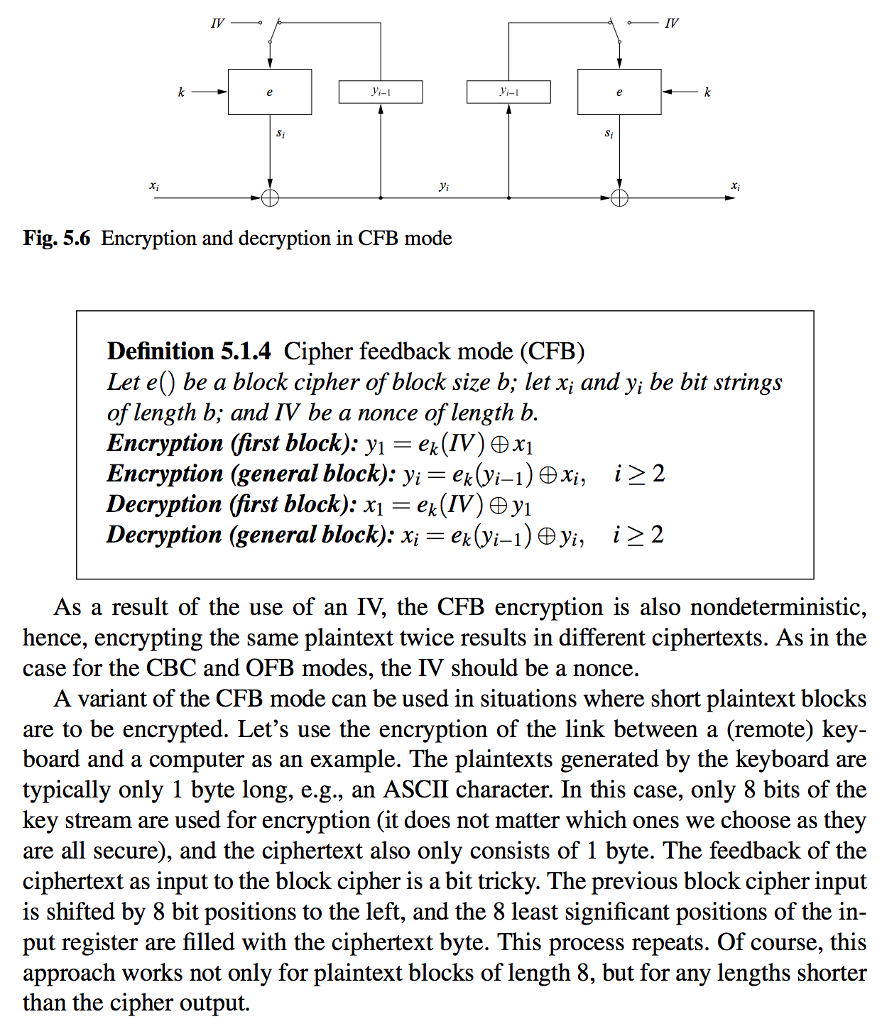
f-1 yi xi Fig. 5.6 Encryption and decryption in CFB mode Definition 5.1.4 Cipher feedback mode (CFB) Let e be a block cipher of block size b; let Xi and yi be bit strings of length b; and IV be a nonce of length b Encryption first block): y,-ex(IVxy Encryption (general block): yi -ekVi- xi, i 2 2 Decryption first block): x,-ex(1Vjey Decryption (general block): x,-ex(yi-1)yi, 1 22 As a result of the use of an IV, the CFB encryption is also nondeterministic, hence, encrypting the same plaintext twice results in different ciphertexts. As in the case for the CBC and OFB modes, the IV should be a nonce A variant of the CFB mode can be used in situations where short plaintext blocks are to be encrypted. Let's use the encryption of the link between a (remote) key- board and a computer as an example. The plaintexts generated by the keyboard are typically only 1 byte long, e.g., an ASCII character. In this case, only 8 bits of the key stream are used for encryption (it does not matter which ones we choose as they are all secure), and the ciphertext also only consists of 1 byte. The feedback of the ciphertext as input to the block cipher is a bit tricky. The previous block cipher input is shifted by 8 bit positions to the left, and the 8 least significant positions of the in put register are filled with the ciphertext byte. This process repeats. Of course, this approach works not only for plaintext blocks of length 8, but for any lengths shorter than the cipher output. f-1 yi xi Fig. 5.6 Encryption and decryption in CFB mode Definition 5.1.4 Cipher feedback mode (CFB) Let e be a block cipher of block size b; let Xi and yi be bit strings of length b; and IV be a nonce of length b Encryption first block): y,-ex(IVxy Encryption (general block): yi -ekVi- xi, i 2 2 Decryption first block): x,-ex(1Vjey Decryption (general block): x,-ex(yi-1)yi, 1 22 As a result of the use of an IV, the CFB encryption is also nondeterministic, hence, encrypting the same plaintext twice results in different ciphertexts. As in the case for the CBC and OFB modes, the IV should be a nonce A variant of the CFB mode can be used in situations where short plaintext blocks are to be encrypted. Let's use the encryption of the link between a (remote) key- board and a computer as an example. The plaintexts generated by the keyboard are typically only 1 byte long, e.g., an ASCII character. In this case, only 8 bits of the key stream are used for encryption (it does not matter which ones we choose as they are all secure), and the ciphertext also only consists of 1 byte. The feedback of the ciphertext as input to the block cipher is a bit tricky. The previous block cipher input is shifted by 8 bit positions to the left, and the 8 least significant positions of the in put register are filled with the ciphertext byte. This process repeats. Of course, this approach works not only for plaintext blocks of length 8, but for any lengths shorter than the cipher output







