







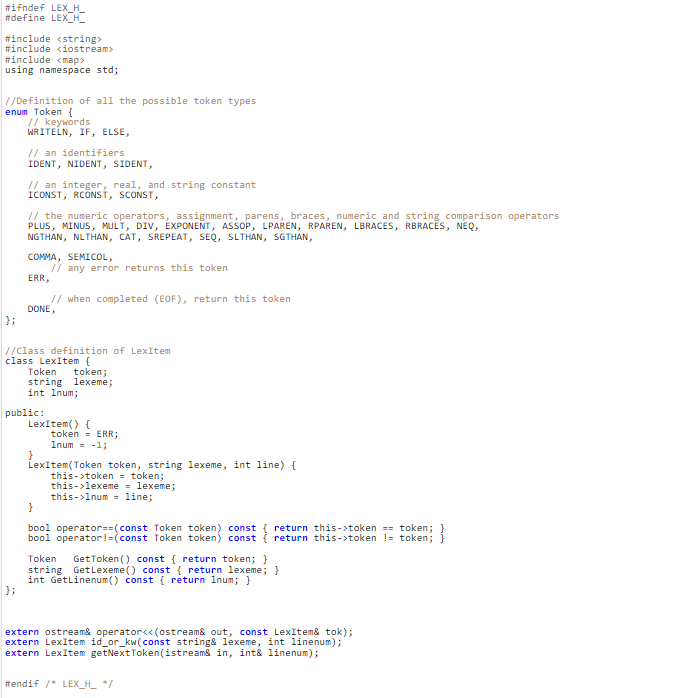

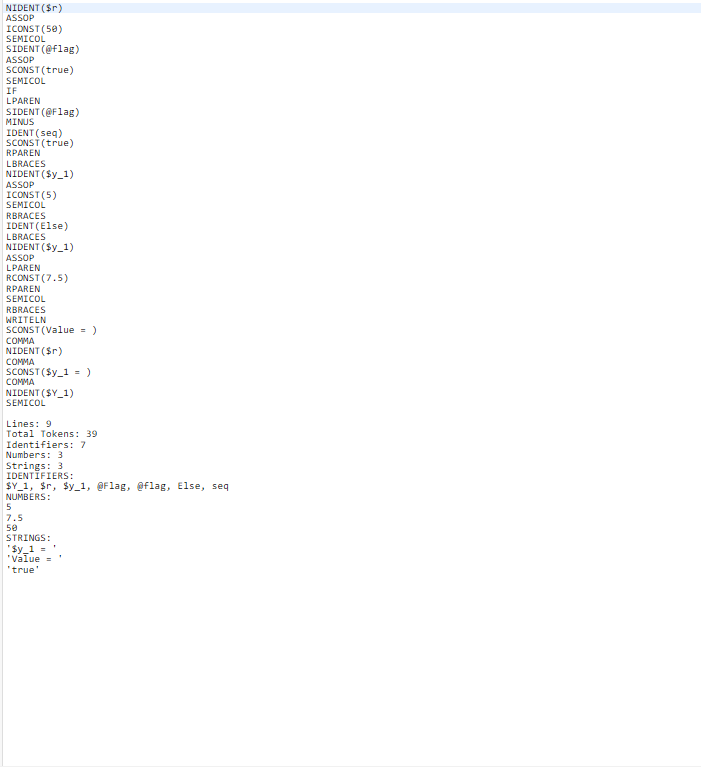
In this programming assignment, you will be building a lexical analyzer for small programming language, called Simple Perl-Like (SPL), and a program to test it. This assignment will be followed by two other assignments to build a parser and an interpreter to the SPL language. Although, we are not concerned about the syntax definitions of the language in this assignment, we intend to introduce it ahead of Programming Assignment 2 in order to determine the language terminals: reserved words, constants, identifier(s), and operators. The syntax definitions of the SPL language are given below using EBNF notations. However, the details of the meanings (i.e. semantics) of the language constructs will be given later on. 1. Prog ::= StmtList 2. StmtList ::= Stmt ;{ Stmt; } 3. Stmt : := Assignstme | writeLnstmt | Ifstmt 4. WriteLnstmt : = WRITELN (ExprList) 5. IfStmt ::= IF (Expr) ' { 'StmtList ' } ' [ELSE ' { 'StmtList ' } ' ] 6. Assignstmt ::=Var=Expr 7. Var ::= NIDENT SIDENT 8. ExprList ::=Expr{, Expr } 9. Expr : := RelExpr [(eq==)RelExpr] 10. RelExpr ::= AddExpr [(1tgt ) AddExpr ] 11. AddExpr : : MultExpr {(+11.)MultExpr} 12. Multexpr : := ExponExpr {(/) ExponExpr } 13. Exponexpr : := UnaryExpr { UnaryExpr } 14. UnaryExpr ::=[(1+)] PrimaryExpr 15. Primaryexpr ::= IDENT | SIDENT | NIDENT | ICONST | RCONST | SCONST | ( Expr) Based on the language definitions, the lexical rules of the language and the assigned tokens to the terminals are as follows: 1. The language has general identifiers, referred to by IDENT terminal, which are defined as a word that starts by a letter or an underscore ' , , and followed by zero or more letters, digits, or underscores ", characters. Note that all identifiers are case sensitive. It is defined as: IDENT := [Letter ]{(Letter Digit )} Letter := [azAz] Digit :=[09] 2. The language variables are either numeric scalar variables or string scalar variables. Numeric variables start by a "\$" and followed by an IDENT. While a string variable starts by "@" and followed by an IDENT. Their definitions are as follows: NIDENT :=$ IDENT SIDENT :=@ IDENT 3. Integer constant is referred to by ICONST terminal, which is defined as one or more digits. It is defined as: ICONST :=[09]+ 4. Real constant is a fixed-point real number referred to by RCONST terminal, which is defined as one or more digits followed by a decimal point (dot) and zero or more digits. It is defined as: RCONST :=([09]+)\([09]) For example, real number constants such as 12.0 , and 0.2 , 2. are accepted as real constants, but .2 , and 2.45 .2 are not. Note that ".2" is recognized as a dot (CAT operator) followed by the integer constant 2. 5. String literals is referred to by SCONST terminal, which is defined as a sequence of characters delimited by single quotes, that should all appear on the same line. For example, 'Hello to CS 280.' is a string literal. While, "Hello to CS 280." Or 'Hello to CS 280." are not. 6. The reserved words of the language are: writeln, if, else. These reserved words have the following tokens, respectively: WRITELN, IF, ELSE. 7. The operators of the language are: +,,,/,,=,(),,{},,==,>,

















