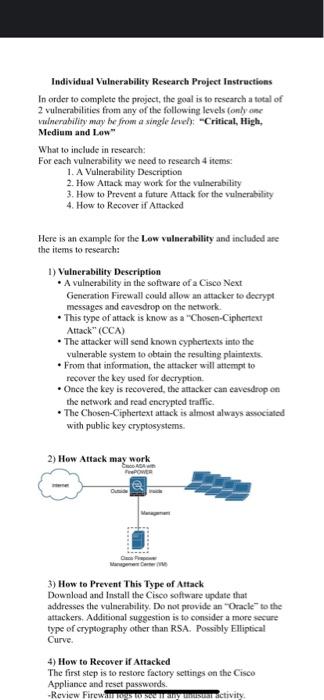
Individual Vulnerability Research Preject Instructions In order to complete the project, the goal is to research a total of 2 vulnerabilities from any of the following levels (anly aes vilnerability may be from a single leweh): "Critical, High, Mediun and L.ow" What to include in research: For each vulnersbility we need to rescarch 4 items: 1. A Vulnerability Description 2. How Attack may work for the vulnerability 3. How to Prevent a future Attack for the vulnerabilaty 4. How to Recover if Attacked Here is an example for the Low vulaerability and included are the items to research: 1) Vulnerability Description - A vulnerability in the software of a Cisco Next. Generation Firewall could allew an attacker to decrypt messages and eavesdrop on the network. - This type of attack is know as a "Chosen-Ciphencut Attack" (CCA) - The attacker will send known cyphertexts into the vulnerable system to obtain the resulting plaintexts. * From that information, the attacker will atterupt to recover the key used for decryption. - Once the key is recovered, the antacker can eavesdrop on the network and read encrypted traflic. - The Chosen-Ciphertext attack is almost always associated with pablic key cryptosystem5. 3) How to Prevent This Type of Attack Download and Install the Cisco software update that addresses the vulaerability. Do not peovide an 'Oracle' to the attackers. Additional suggestion is to consider a more secure type of cryptography other than RSA. Possibly Elliptical Curve. 4) How to Recover if Attacked The first step is to restore factory settings an the Cisco Appliance and reset passwords. - A vulnerability in the software of a Cisco Next Generation Firewall could allow an attacker to decrypt messages and eavesdrop oet the network. - This type of attack is know as a "Chosen-Cipherteat Attack" (CCA) - The attacker will send known cyphertexts into the vulnerable system to obtain the resulting plaintexts. - From that information, the attacker will attempt to recover the key used for decryption. - Once the key is recovered, the altacker can eaveidrop on the network and read encrypted traffic. - The Chosen-Ciphertext attack is almost always associated with pablic key eryptosystems. 3) How to Prevent This Type of Attack Download and Install the Cisco software update that addresses the vulnerability. Do not peovide an "Oracle" to the attackers. Additional suggestion is to consider a more secure type of cryptography other than RSA. Possibly Elliptical Curve. 4) How to Recover if Attacked The first step is to restore factory settings on the Cisco Appliance and reset passwords. - Revicw Firewall logs to sec if any undsual activity. -If there is any unusual activity, review all network system logs for signs of farther penctration. - Update all software patches and run Anti-Virus scan of the entire system. Note: To get started, recommend to rescarch I vulnerability at a time, below is an ctample of a low vulnerability. Below are several research databases for Vulnerabilities: a. heps lizwwicvedctailscoms b. hatias ficve mitre org? c. hetpseliwwwudnenabilitysenter com thome d. hugs.lind.niss,gov? Shaun Manzano - Cyber Securi... Z AZT Times: |Mon-Wed. 6am-8am 8 6p... 60 Shaun Manzano - Cyber Security Instructor/Program Chair 4.18PM recommend writing up in a power point so that the information is already in the correct form, attached is an example, with the exception, only two vulnerability types are required Cyber Security Final Proje... 734 KB PowerPoint Presentation Final Project Presentation Pite Conpers sounds good, please let me know as you have questions, keep up the great work You're up to date + Message Shaun Manzano - Cyber Secur... for what to search for include: Linux, Windows 10, OpenSSH, SFTP Service. mplete the vulnerablity report example for each of the threat levels. Week 1 10 poin Directions Week 1 Hands-On Please answer each of the following questions in 34 sentences to demonstrate your weekty progress: - Which fiog / wuinerability report are you currently working on? - Which flags/vulnerabilizy have you fin shed so far? - What were the most difficult issue you had to resolve? - What were the process you used to solve that issue, or do you still need help