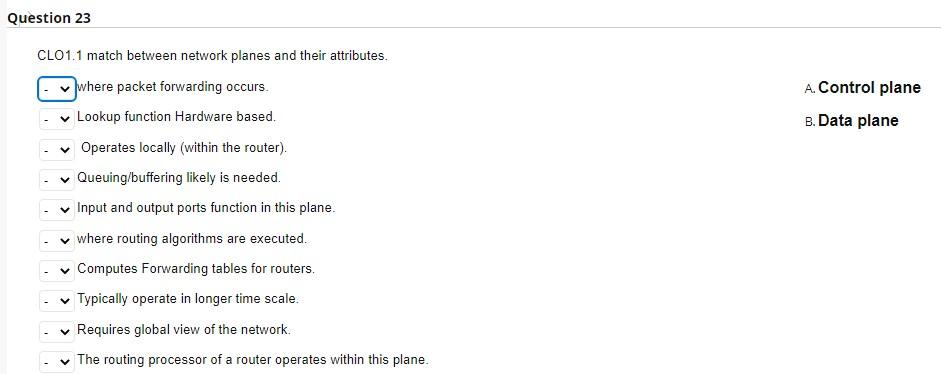
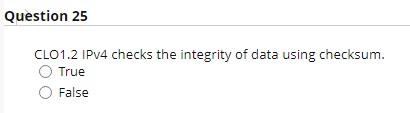
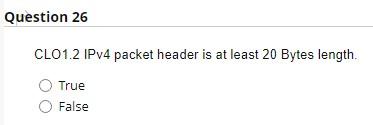
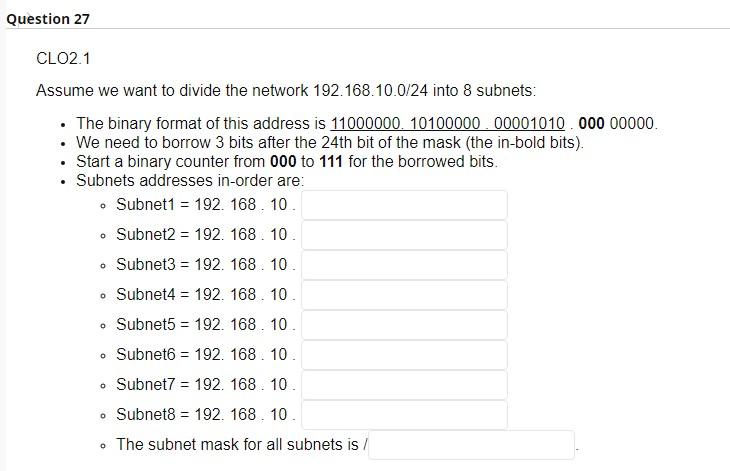
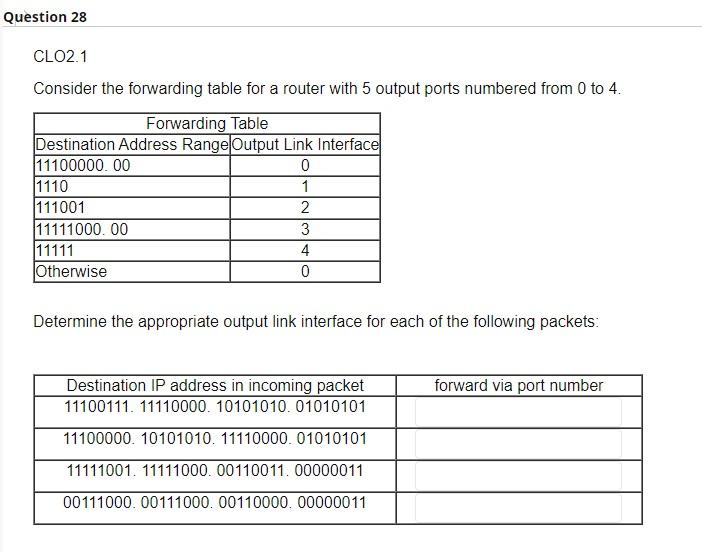
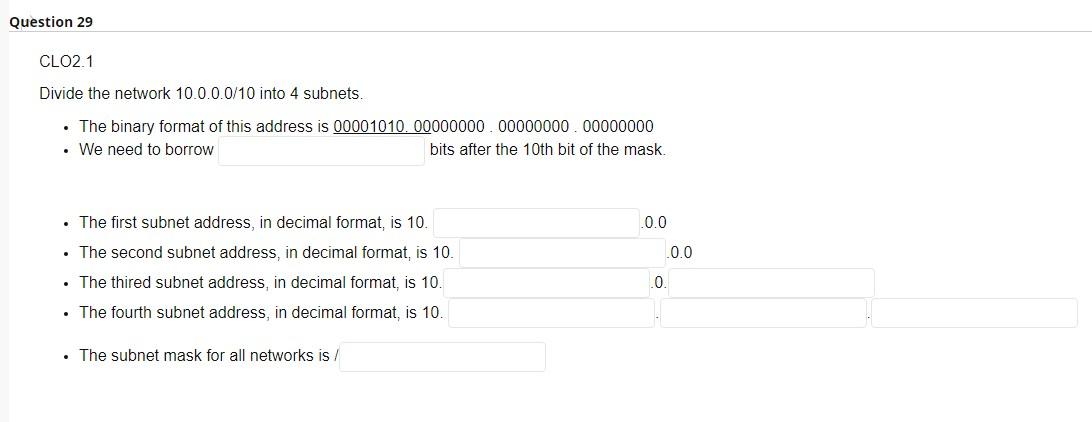
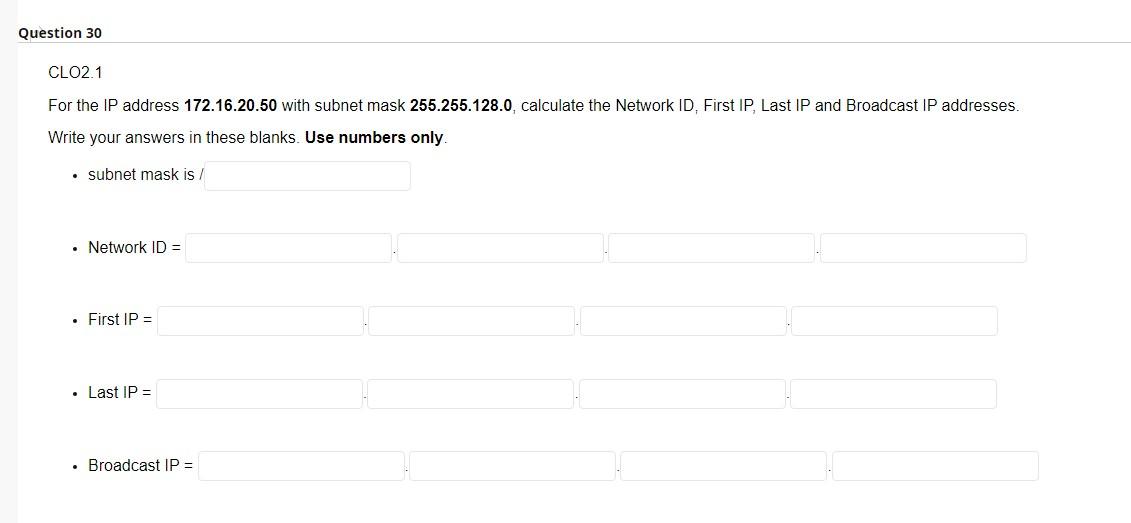
Internet service model only provides best-effort service. True False Network layer provides logical communication between hosts. True False Transport layer provides logical communication between application processes running on different hosts. True False Typically, transport layer segment will be first encapsulated in a link layer frame such as Ethernet. True False CLO1.2 TCP delivers segemetn to destination socket based on destination port number only. True False TCP has a smaller header size compared to UDP. True False TCP offers reliable and on-order delivery of data True False The first special segment used in the TCP 3-way handshake is SYN. True False The special segment used to colse a TCP connection is SYN ACK. True False UDP checks segment integrity at the reciever using checksum. True False UDP delivers segemt to receiver socket based on destination port number only. True False UDP is connectionless. True False UDP is generally preferred by applications concerned about timing. True False UDP provides congestion and flow control True False UDP uses ACK and NACK mechanisms to ensure error-free delivery of segments. True False CLO1.2 While UDP does not provide secure transport, TCP guarantees security of payload messages. True False ACK and NACK are used to detect bit errors in transmitted segment. True False By sending back , receiver explicitly tells sender that packet received is OK ACK SYN Duplicate NACK CLO3.1 In ender sends one packet and then waits for feedback from the reciever about the status of the packet. RTT Timeout Stop-ans-wait Flow control CLO3.1 In congestion control, sender reduces its speed so that the receiver can handle all incoming data from that connection without buffer overflow. True False Pipelining improves the security of segments by sending them back-to-back. True False CLO3.1 Which of these protocols uses cumulative ACK? Selective Repeat Stop-and-wait Go-back-N Pipelining CLO1.1 match between network planes and their attributes. where packet forwarding occurs. A. Control plane Lookup function Hardware based. B. Data plane Operates locally (within the router). Queuing/buffering likely is needed. Input and output ports function in this plane. where routing algorithms are executed. Computes Forwarding tables for routers. Typically operate in longer time scale. Requires global view of the network. The routing processor of a router operates within this plane. CLO1.2 IPv4 addresses are 4 bytes long whereas IPv6 addresses are 6 bytes long. True False CLO1.2 IPv4 checks the integrity of data using checksum. True False CL01.2 IPv4 packet header is at least 20 Bytes length. True False CLO2.1 Assume we want to divide the network 192.168.10.0/24 into 8 subnets: - The binary format of this address is 11000000.10100000.00001010.00000000. - We need to borrow 3 bits after the 24 th bit of the mask (the in-bold bits). - Start a binary counter from 000 to 111 for the borrowed bits. - Subnets addresses in-order are: - Subnet1 =192.168.10. - Subnet2 =192.16810. - Subnet3 = 192. 168. 10 . - Subnet4 = 192. 168.10. - Subnet5 =192. 168.10. - Subnet6 =192.168.10. - Subnet7 =192.168.10. - Subnet8 =192. 168.10. Consider the forwarding table for a router with 5 output ports numbered from 0 to 4 . Determine the appropriate output link interface for each of the following packets: CLO2.1 Divide the network 10.0.0.0/10 into 4 subnets. - The binary format of this address is 00001010.00000000.00000000.00000000 - We need to borrow bits after the 10th bit of the mask. - The first subnet address, in decimal format, is 10.0.0 - The second subnet address, in decimal format, is 10 0.0 - The thired subnet address, in decimal format, is 10 - The fourth subnet address, in decimal format, is 10. - The subnet mask for all networks is / Write your answers in these blanks. Use numbers only. - subnet mask is/ - Network ID = - First IP= - Last IP= - Broadcast IP=




































