Answered step by step
Verified Expert Solution
Question
1 Approved Answer
IP range is 10.100.105.0/24 Please i need those answers. thank you root@kali : ~# nmap -Pn 16. 100 . 105 . 1. Starting Nmap 7.70
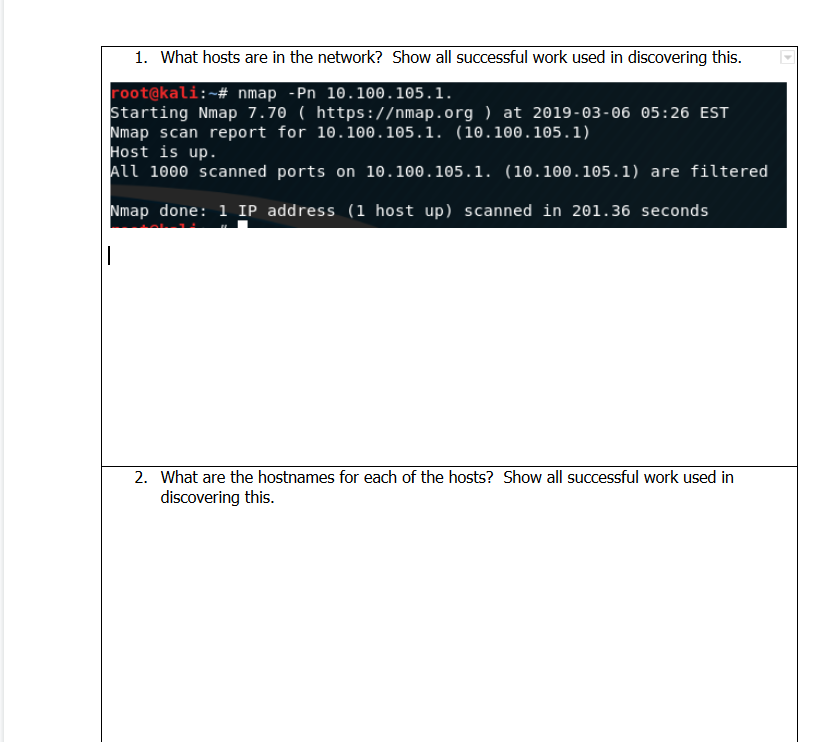


IP range is 10.100.105.0/24
Please i need those answers. thank you
root@kali : ~# nmap -Pn 16. 100 . 105 . 1. Starting Nmap 7.70 ( https:/map.org at 2019-03-06 05:26 EST Nmap scan report for 10.100.105.1. (10.100.105.1) Host is up. All 1000 scanned ports on 10.100.105.1. (10.100.105.1) are filtered Nmap done: 1 IP address (1 host up) scanned in 201.36 seconds 2. What are the hostnames for each of the hosts? Show all successful work used in 3. What services are running on the main webserver? Show all successful work used in discovering this 4. Which hosts are running HTTP, and on what ports? What type and version of webservers are running on each port? Show all successful work used in discovering this. 5. What user accounts are on the second XP system? Show all successful work used in discovering this. What is the MAC address of the second XP system? Show all successful work used in discovering this. 6. 7. What critical vulnerabilities are on the FTP server? Show all successful work used in discovering this. 8. Using one or more tools to perform traceroute scans, draw a map of the Cyberwildcats network by targeting the following networks: 10.20.30.0/24, 10.20.31.0/24, 172.25.20.0/24, 10.100.101.0/24, 10.100.102.0/24, 10.100.103.0/24, 10.100.104.0/24, 10.100.105.0/24, 10.150.100.0/24, 10.200.100.0/24, 172.16.101.0/24, 172.16.102.0/24, 172.16.103.0/24, 172.16.104.0/24, 172.16.105.0/24 ONLY use traceroute functionality to build this map. Discovery scans may be used to identify endpoints in the network, but those should be only host discovery scans. DO NOT scan for open ports. The map should not include more than one endpoint per Show the graphical map and all successful work used in discovering this. root@kali : ~# nmap -Pn 16. 100 . 105 . 1. Starting Nmap 7.70 ( https:/map.org at 2019-03-06 05:26 EST Nmap scan report for 10.100.105.1. (10.100.105.1) Host is up. All 1000 scanned ports on 10.100.105.1. (10.100.105.1) are filtered Nmap done: 1 IP address (1 host up) scanned in 201.36 seconds 2. What are the hostnames for each of the hosts? Show all successful work used in 3. What services are running on the main webserver? Show all successful work used in discovering this 4. Which hosts are running HTTP, and on what ports? What type and version of webservers are running on each port? Show all successful work used in discovering this. 5. What user accounts are on the second XP system? Show all successful work used in discovering this. What is the MAC address of the second XP system? Show all successful work used in discovering this. 6. 7. What critical vulnerabilities are on the FTP server? Show all successful work used in discovering this. 8. Using one or more tools to perform traceroute scans, draw a map of the Cyberwildcats network by targeting the following networks: 10.20.30.0/24, 10.20.31.0/24, 172.25.20.0/24, 10.100.101.0/24, 10.100.102.0/24, 10.100.103.0/24, 10.100.104.0/24, 10.100.105.0/24, 10.150.100.0/24, 10.200.100.0/24, 172.16.101.0/24, 172.16.102.0/24, 172.16.103.0/24, 172.16.104.0/24, 172.16.105.0/24 ONLY use traceroute functionality to build this map. Discovery scans may be used to identify endpoints in the network, but those should be only host discovery scans. DO NOT scan for open ports. The map should not include more than one endpoint per Show the graphical map and all successful work used in discovering thisStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


