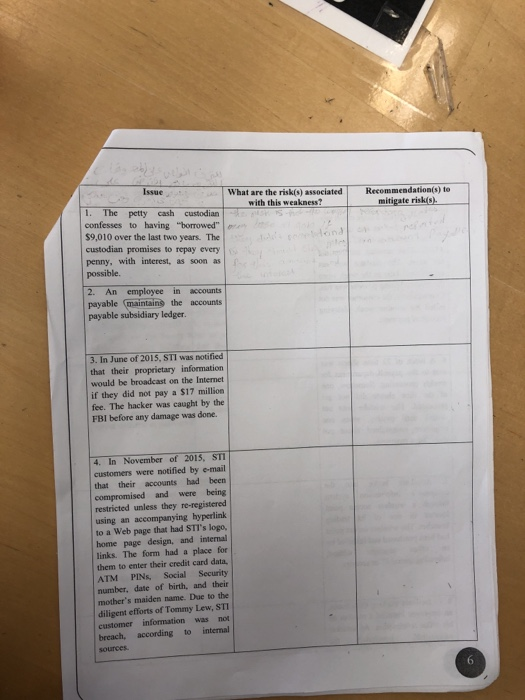
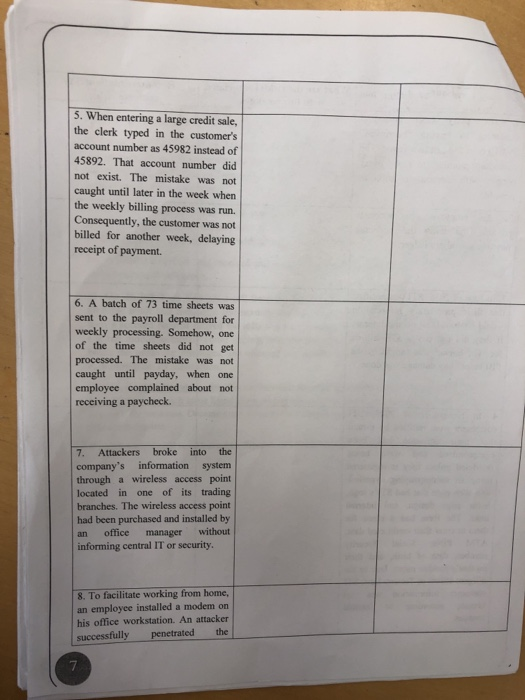
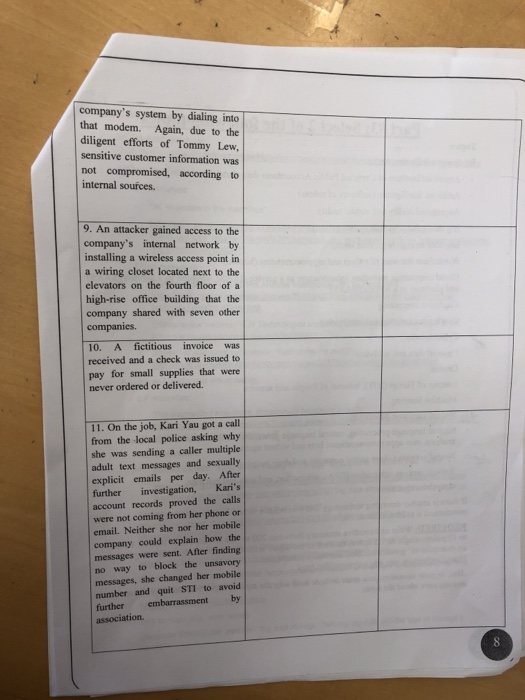
Issue What are the risk(s) associated Recommendation(s) to mitigate risk(s). with this weakness? 1. The petty cash confesses to having "borrowed" custodian $9,010 over the last two years. The custodian promises to repay every penny, with interest, as soon as possible. An employee in pavable (maintains the accounts payable subsidiary ledger. 2 accounts 3. In June of 2015, STI was notified that their proprietary information would be broadcast on the Internet. if they did not pay a $17 million fee. The hacker was caught by the FBI before any damage was done. 4. In November of 2015, STI customers were notified by e-mail had been that their accounts compromised restricted unless they re-registered using an accompanying hyperlink to a Web page that had STI's logo, and were being home page design, and internal links. The form had a place for them to enter their credit card data Social Security PINS ATM number, date of birth, and their mother's maiden name. Due to the diligent efforts of Tommy Lew, STI information according not was customer internal te breach, sources 5. When entering a large credit sale, the clerk typed in the customer's account number as 45982 instead of 45892. That account number did not exist. The mistake was not caught until later in the week when the weekly billing process was run. Consequently, the customer was not billed for another week, delaying receipt of payment. 6. A batch of 73 time sheets was sent to the payroll department for weekly processing. Somehow, one of the time sheets did not get processed. The mistake was not caught until payday, when one employee complained about not receiving a paycheck. broke Attackers into the 7. company's through a wireless access point located in one of its trading branches. The wireless access point information system had been purchased and installed by manager informing central IT or security. without office an 8. To facilitate working from home. an employee installed a modem on his office workstation. An attacker penetrated the successfully company's system by dialing into that modem. Again, due to the diligent efforts of Tommy Lew sensitive customer information was not compromised, according to internal sources. 9. An attacker gained to the company's internal network by installing a wireless access point in a wiring closet located next to the elevators on the fourth floor of a high-rise office building that the company shared with seven other companies. A fictitious invoice 10. was received and a check was issued to pay for small supplies that were never ordered or delivered. 11. On the job, Kari Yau got a call from the local police asking why she was sending a caller multiple adult text messages and sexually explicit emails per day. After further Kari's investigation, account records proved the calls were not coming from her phone or email. Neither she nor her mobile company could explain how the messages were sent. After finding no way to block the unsavory messages, she changed her mobile number and quit STI to avoid embarrassment by further association