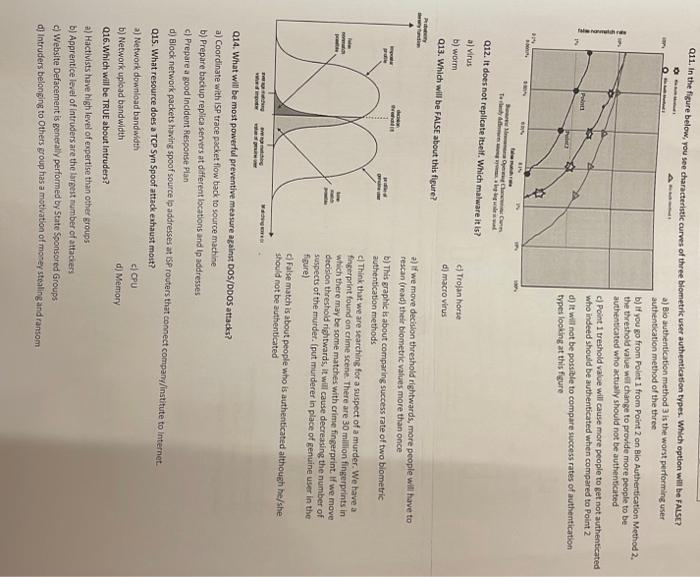
J If you go from Point 1 from Point 2 on Blo Authertication Method 2 . le threshold value wir change to provide more people to be ithenticated who actually should not be authenticated Point 1 treshold valve will cause more people to get not authenticated ho indeed should be authenticated when compared to Point 2 ift will not be possizle to compare success rates of authentication pes locking at this figure Q12. It does not replicate itself. Which malware it is? a) virus b) worm c) Trojan harte Q13. Which will be FAISE about this figure? d) macrovirus 2) if we move decision threshold rightwards, more people will have to rescan (read) their biometric values more than once b) This graphic is about comparing success rate of two blometric authentication methods c) Think that we are searching for a suspect of a murder. We have a fingerpilint found on crime scene. There are 30 million fingerprints in which there may be some matches with crime fingerarint. If we move decision threshold rightwards, it will cause decreasing the number of suspects of the murder. (put murderer in place of genuine user in the fisarel. c) False match is about people who is authenticated although he/she should not be authenticated Q14. What will be most powerful preventive measure against Dos/DbOS attacks? a) Coordinate with 15p trace packet flow back to source machine b) Prepare backup replica servers at daferent locations and Ip addresses c) Prepare a good incident fiesponse Pian d) Block network packets hawing spoof source lp addresses att bp routers that connect company/institute to internet. Q15. What resource does a TCP SYn Spoof attack exhaust most? a) Network download bandwidth ciopy b) Network upload bandwidth Q16. Which will be TRUE about Intruders? d) Memory a) Hactivists have high level of expertise than other groups b) Apprentice level of intruders are the Isreest number of attackess c) Website Defacement is generally performed by State Sponscred Groups d) Intruders belonging to Others group has a motivation of mo-ey stealing and ransom