 Java Problem
Java Problem
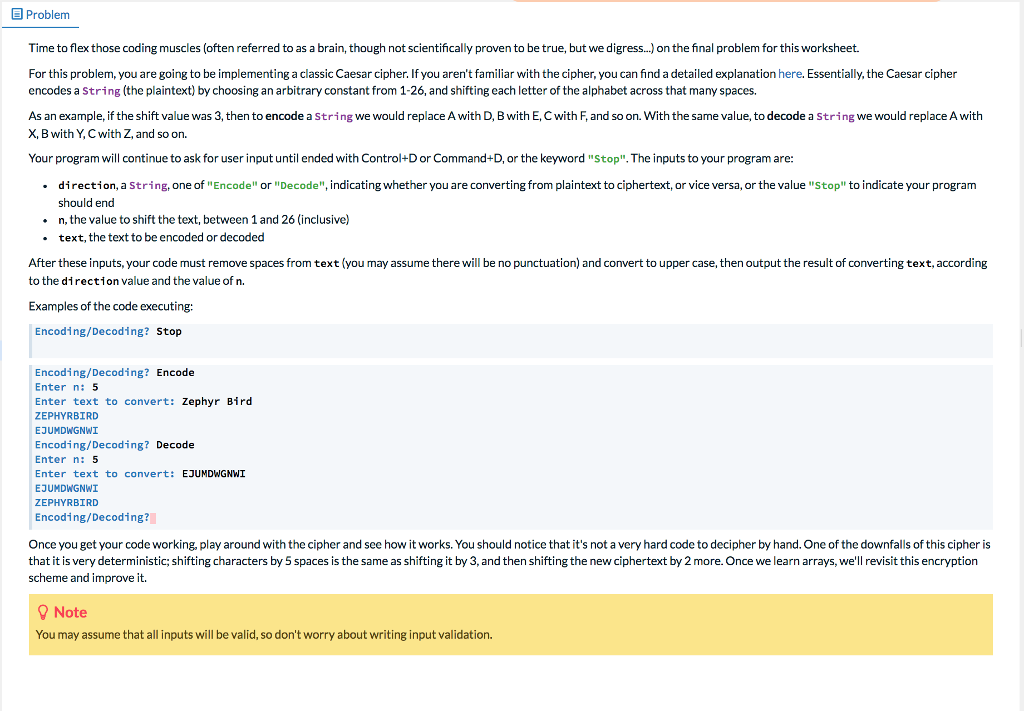
E Problem Time to flex those coding muscles (often referred to as a brain, though not scientifically proven to be true, but we digress...) on the final problem for this worksheet. For this problem, you are going to be implementing a classic Caesar cipher. If you aren't familiar with the cipher, you can find a detailed explanation here. Essentially, the Caesar cipher encodes a String (the plaintext) by choosing an arbitrary constant from 1-26, and shifting each letter of the alphabet across that many spaces. As an example, if the shift value was 3, then to encode a String we would replace A with D, B with E, C with F, and so on. With the same value, to decode a String we would replace A with X, B with Y, C with Z, and so on. Your program will continue to ask for user input until ended with Control+D or Command+D, or the keyword "Stop". The inputs to your program are: direction, a String, one of "Encode" or "Decode", indicating whether you are converting from plaintext to ciphertext, or vice versa, or the value "Stop" to indicate your program should end n, the value to shift the text, between 1 and 26 (inclusive) text, the text to be encoded or decoded . . . After these inputs, your code must remove spaces from text (you may assume there will be no punctuation) and convert to upper case, then output the result of converting text, according to the direction value and the value of n. Examples of the code executing: Encoding/Decoding? Stop Encoding/Decoding? Encode Enter n: 5 Enter text to convert: Zephyr Bird ZEPHYRBIRD EJUMDWGNWI Encoding/Decoding? Decode Enter n: 5 Enter text to convert: EJUMDWGNWI EJUMDWGNWI ZEPHYRBIRD Encoding/Decoding? Once you get your code working, play around with the cipher and see how it works. You should notice that it's not a very hard code to decipher by hand. One of the downfalls of this cipher is that it is very deterministic; shifting characters by 5 spaces is the same as shifting it by 3, and then shifting the new ciphertext by 2 more. Once we learn arrays, we'll revisit this encryption scheme and improve it. Note You may assume that all inputs will be valid, so don't worry about writing input validation
 Java Problem
Java Problem





