Question: [Lab 5.1] Certificate generation This lab shows an example of generating a certificate and have it signed by a CA. In this instance we
![[Lab 5.1] Certificate generation This lab shows an example of generating a](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/02/65cab0db7e4be_36365cab0db4db9b.jpg)
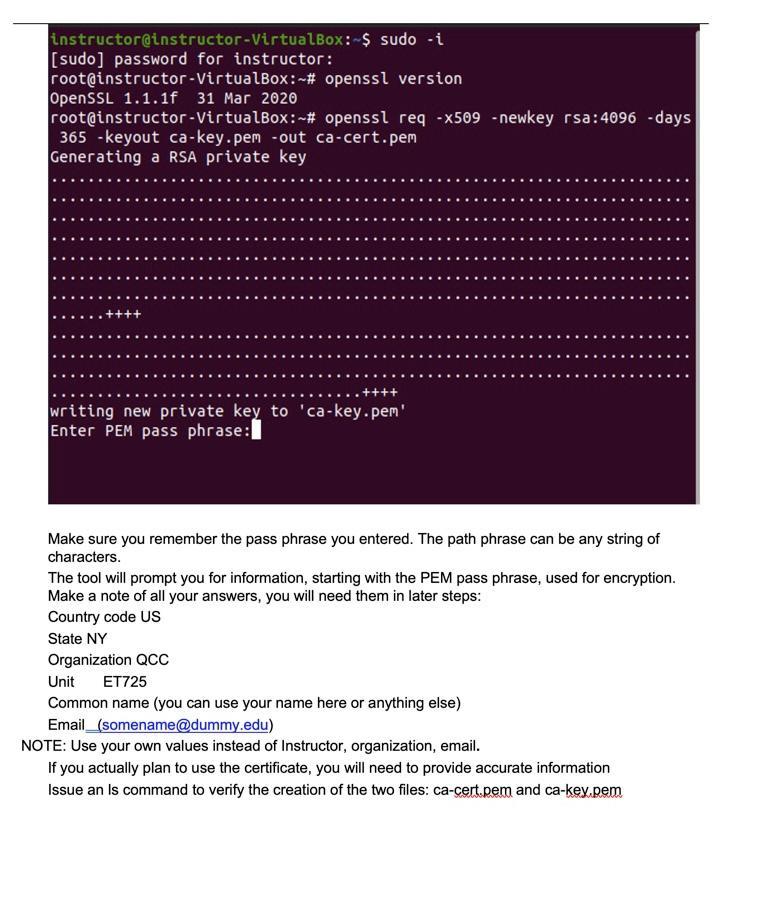
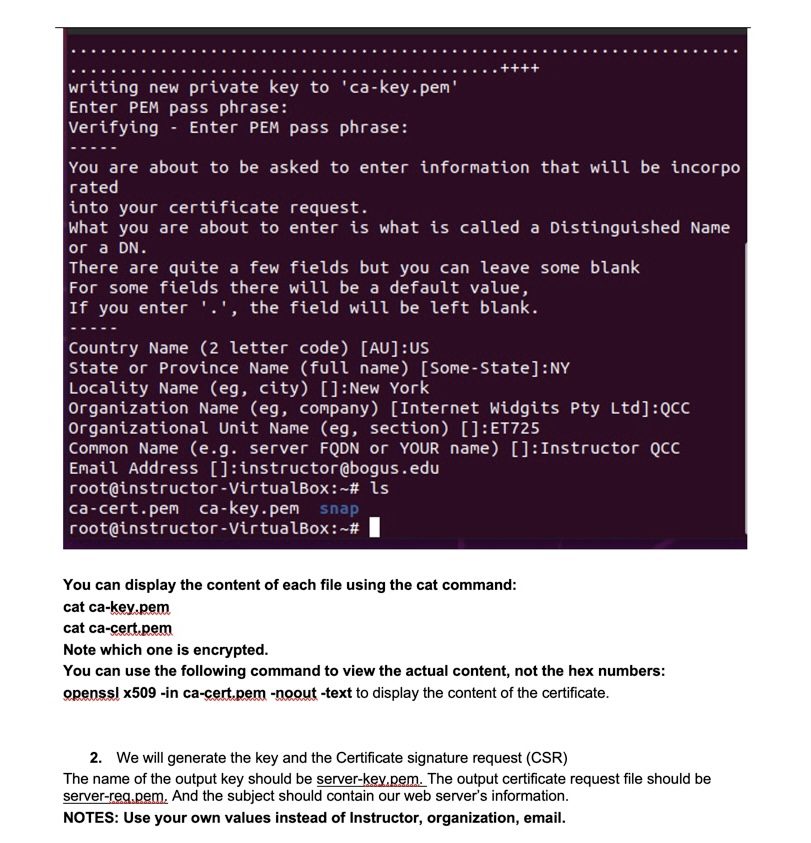
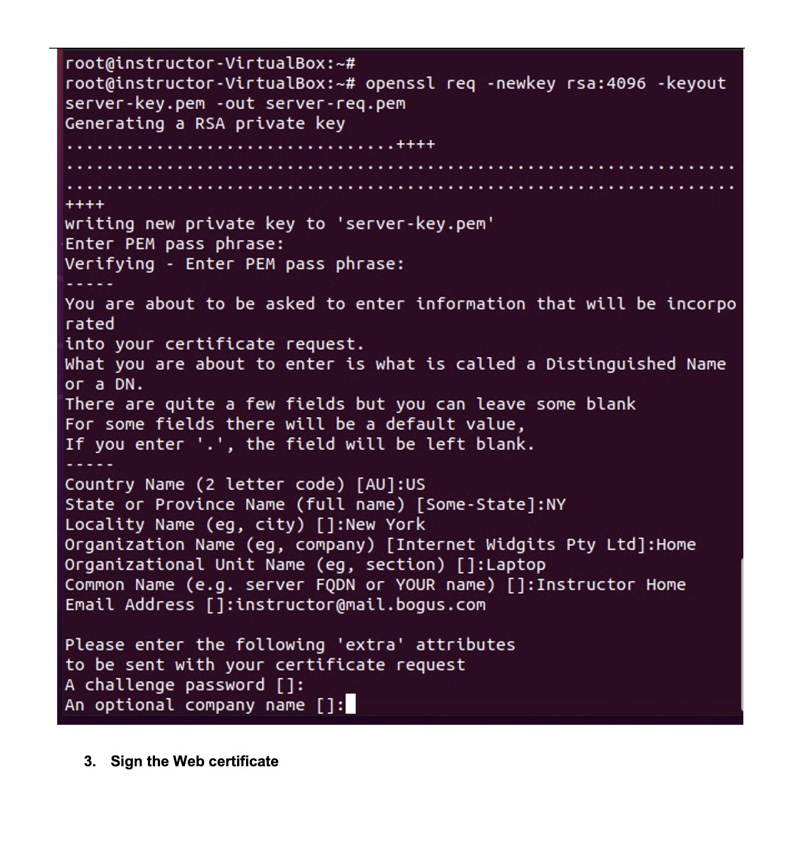
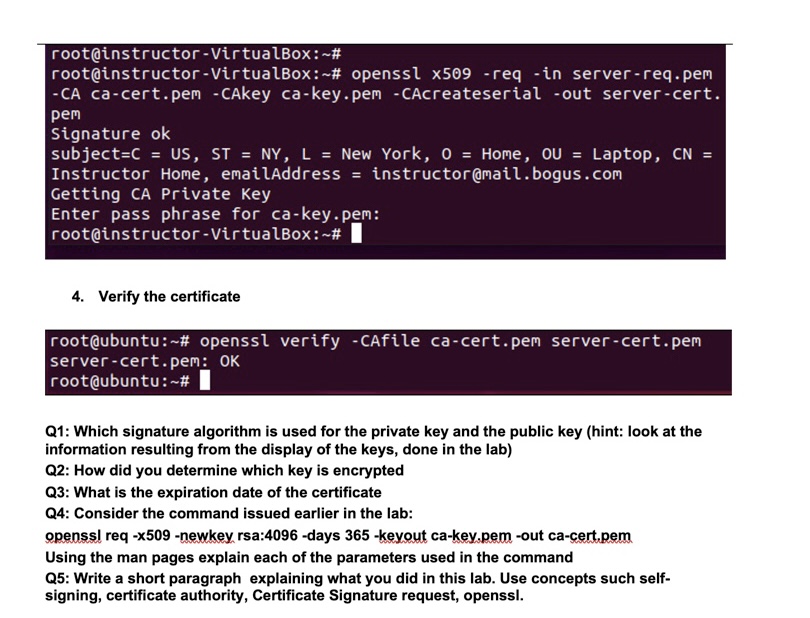
[Lab 5.1] Certificate generation This lab shows an example of generating a certificate and have it signed by a CA. In this instance we will not submit it to a commercial CA, we will play the role of the CA as well. The lab has 4 main steps: 1. Generate CA private key and certificate 2. Generate Web server's private key and Certificate Signature Request (CSR) 3. Sign the Web server's certificate request 4. Verify the certificate Lab helpful information: If openssl is not installed, the system will diplay the command to install it. You will need to install openssl if not already installed For information about openssl command: General information: man openssl or more openssl. Command specific help is provided for each subcommand, for example, for the openssl req command: man openssl-req or more openssl-req 1. Generate a private key. We will use the openssl utility. Information about it can be obtained from the man page for openssl, Use the command man openss! to display. You can find a copy of the man page in the Lab folder. issue the commands: sudo -i. This command will allow you to issue root level commands without repeatedly enter the sudo command and being prompted for a password each time. openssl version, to verify that openssl is installed and note the version number. openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem Explanation of qualifiers: -x509 to request a self signed certificate -newkey rsa:4096 Creates a new RSA private key of 4096 bits -days 365 How many days the certificate is valid -keyout ca-key.pem to create a private key named ca-key.pem -out ca-cert.pem to redirect the output into a file named ca-cert.pem instructor@instructor-VirtualBox:~$ [sudo] password for instructor: root@instructor-VirtualBox:~# OpenSSL 1.1.1f 31 Mar 2020 root@instructor-VirtualBox:~# 365 -keyout ca-key.pem -out ca-cert.pem Generating a RSA private key sudo -i openssl version openssl req -x509 -newkey rsa: 4096 -days writing new private key to 'ca-key.pem' Enter PEM pass phrase: Make sure you remember the pass phrase you entered. The path phrase can be any string of characters. The tool will prompt you for information, starting with the PEM pass phrase, used for encryption. Make a note of all your answers, you will need them in later steps: Country code US State NY Organization QCC Unit ET725 Common name (you can use your name here or anything else) Email (somename@dummy.edu) NOTE: Use your own values instead of Instructor, organization, email. If you actually plan to use the certificate, you will need to provide accurate information Issue an Is command to verify the creation of the two files: ca-cert.pem and ca-key.pem writing new private key to 'ca-key.pem' Enter PEM pass phrase: Verifying Enter PEM pass phrase: You are about to be asked to enter information that will be incorpo rated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]: NY Locality Name (eg, city) []: New York Organization Name (eg, company) [Internet Widgits Pty Ltd]:QCC Organizational Unit Name (eg, section) []:ET725 Common Name (e.g. server FQDN or YOUR name) []: Instructor QCC Email Address []:instructor@bogus.edu root@instructor - VirtualBox:~# ls ca-cert.pem ca-key.pem snap root@instructor-VirtualBox:~# You can display the content of each file using the cat command: cat ca-key.pem cat ca-cert.pem Note which one is encrypted. You can use the following command to view the actual content, not the hex numbers: openssl x509 -in ca-cert.pem -noout -text to display the content of the certificate. 2. We will generate the key and the Certificate signature request (CSR) The name of the output key should be server-key.pem. The output certificate request file should be server-req.pem, And the subject should contain our web server's information. NOTES: Use your own values instead of Instructor, organization, email. root@instructor-VirtualBox:~# root@instructor - VirtualBox:~# openssl req -newkey rsa: 4096 -keyout server-key.pem -out server-req.pem Generating a RSA private key ++++ writing new private key to 'server-key.pem' Enter PEM pass phrase: Verifying - Enter PEM pass phrase: You are about to be asked to enter information that will be incorpo rated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]: NY Locality Name (eg, city) []: New York Organization Name (eg, company) [Internet Widgits Pty Ltd]: Home Organizational Unit Name (eg, section) []: Laptop Common Name (e.g. server FQDN or YOUR name) []: Instructor Home Email Address []:instructor@mail.bogus.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: 3. Sign the Web certificate root@instructor root@instructor - VirtualBox:~# - VirtualBox:~# openssl x509 -req -in server-req.pem -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert. pem Signature ok subject=C = US, ST = NY, L = New York, 0 = Home, OU = Laptop, CN = Instructor Home, emailAddress = instructor@mail.bogus.com Getting CA Private Key Enter pass phrase for ca-key.pem: root@instructor -VirtualBox:~# 4. Verify the certificate root@ubuntu:~# openssl verify -CAfile ca-cert.pem server-cert.pem server-cert.pem: OK root@ubuntu:~# Q1: Which signature algorithm is used for the private key and the public key (hint: look at the information resulting from the display of the keys, done in the lab) Q2: How did you determine which key is encrypted Q3: What is the expiration date of the certificate Q4: Consider the command issued earlier in the lab: openssl req -x509 -newkey rsa:4096 -days 365 -keyout ca-key.pem -out ca-cert.pem Using the man pages explain each of the parameters used in the command Q5: Write a short paragraph explaining what you did in this lab. Use concepts such self- signing, certificate authority, Certificate Signature request, openssl.
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


