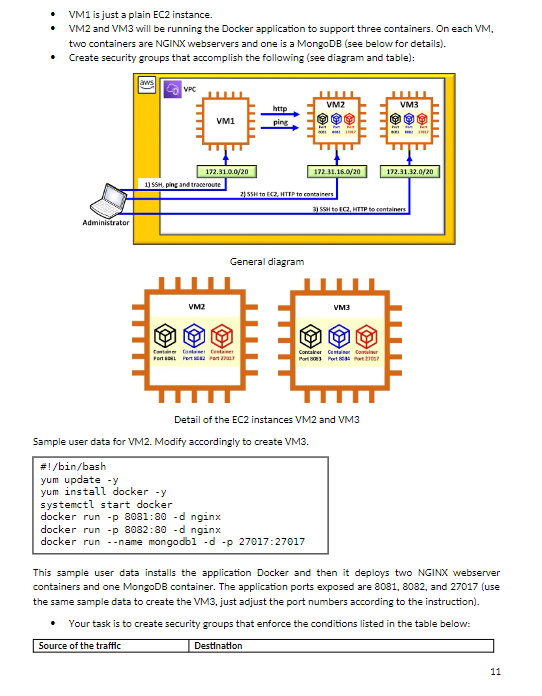
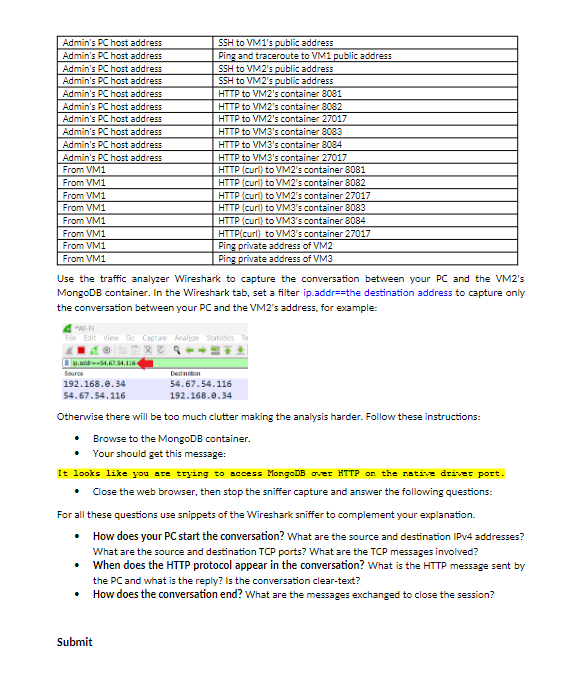
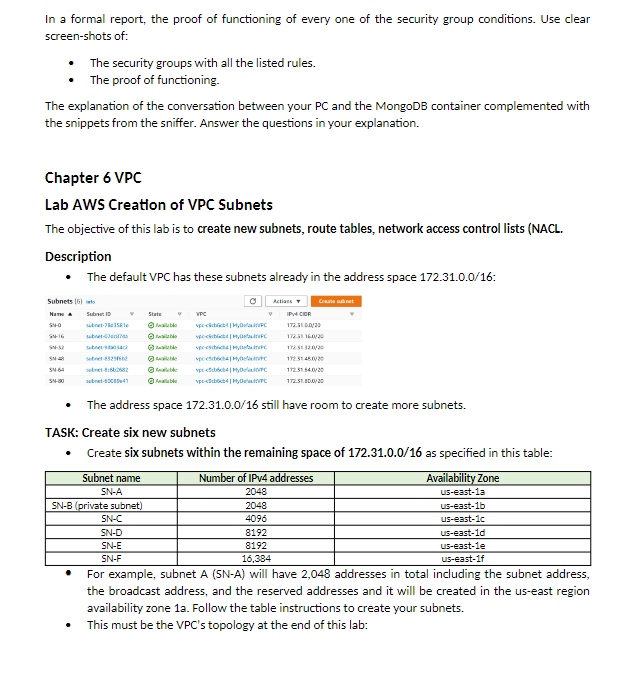
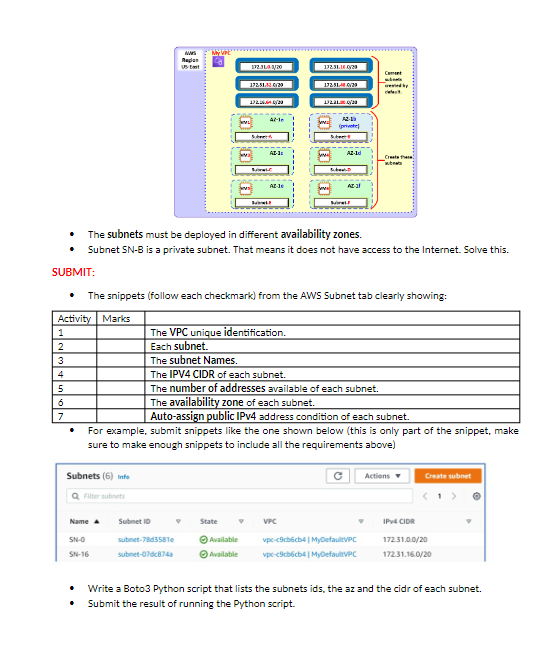
Lab Access Control with Security Groups and TCP analysis - Deploy three EC2 instances. - VM1 is just a plain EC2 instance. - VM2 and VM3 will be running the Docker application to support three containers. On each VM. two containers are NGINX webservers and one is a MongoDB (see below for details). - Create security groups that accomplish the following (see diagram and table): General diagram Detail of the EC2 instances VM2 and VM3 Sample user data for VM2. Modify accordingly to create VM3. \#!/bin/bash yum update -y yum install docker -y systemctl start docker docker run -p 8081:80-d nginx docker run -p 8082:80 - nginx docker run --name mongodbl -d -p 27017:27017 This sample user data installs the application Docker and then it deploys two NGINX webserver containers and one MongoDB container. The application ports exposed are 8081,8082 , and 27017 (use the same sample data to create the VM3, just adjust the port numbers according to the instruction). - Your task is to create security groups that enforce the conditions listed in the table below: Use the traffic analyzer Wireshark to capture the conversation between your PC and the VM2's MongoDB container. In the Wireshark tab, set a filter ip.addr==the destination address to capture only the conversation between your PC and the VM2's address, for example: Otherwise there will be too much clutter making the analysis harder. Follow these instructions: - Browse to the MongoDB container. - Your should get this message: It looks like you are trying to sccess MongoDB over HTTP on the native driver port. - Close the web browser, then stop the sniffer capture and answer the following questions: For all these questions use snippets of the Wireshark sniffer to complement your explanation. - How does your PC start the conversation? What are the source and destination IPv4 addresses? What are the source and destination TCP ports? What are the TCP messages involved? - When does the HTTP protocol appear in the conversation? What is the HTTP message sent by the PC and what is the reply? Is the conversation clear-text? - How does the conversation end? What are the messages exchanged to close the session? In a formal report, the proof of functioning of every one of the security group conditions. Use clear screen-shots of: - The security groups with all the listed rules. - The proof of functioning. The explanation of the conversation between your PC and the MongoDB container complemented with the snippets from the sniffer. Answer the questions in your explanation. Chapter 6VPC Lab AWS Creation of VPC Subnets The objective of this lab is to create new subnets, route tables, network access control lists (NACL. Description - The default VPC has these subnets already in the address space 172.31.0.0/16: - The address space 172.31.0.0/16 still have room to create more subnets. TASK: Create six new subnets - Create six subnets within the remaining space of 172.31.0.0/16 as specified in this table: - For example, subnet A (5N-A) will have 2,048 addresses in total including the subnet address, the broadcast address, and the reserved addresses and it will be created in the us-east region availability zone 1a. Follow the table instructions to create your subnets. - This must be the VPC's topology at the end of this lab: - The subnets must be deployed in different availability zones. - Subnet SN-B is a private subnet. That means it does not have access to the Internet. Solve this. SUBMIT: - The snippets (follow each checkmark) from the AWS Subnet tab clearly showing: sure to make enough snippets to include all the requirements above) - Write a Boto3 Python script that lists the subnets ids, the az and the cidr of each subnet. - Submit the result of running the Python script











