Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Linux (and Unix) permit files to have holes in them. A hole can be created by seeking beyond the end of the file and
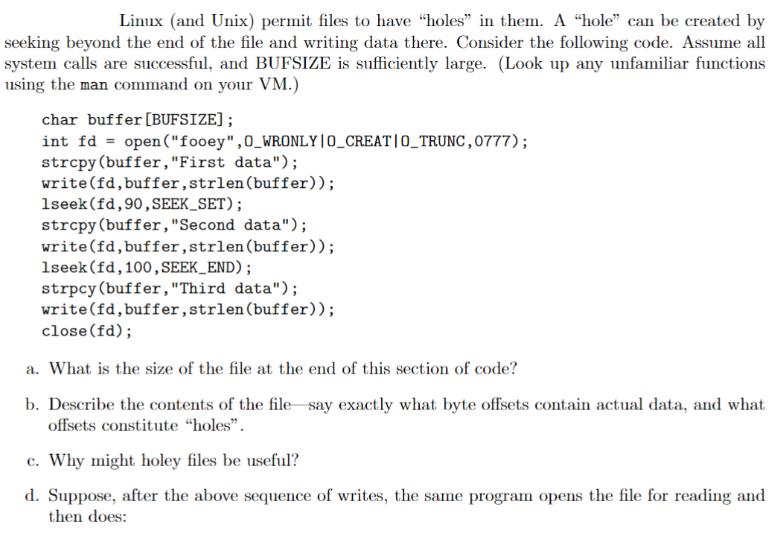

Linux (and Unix) permit files to have "holes" in them. A "hole" can be created by seeking beyond the end of the file and writing data there. Consider the following code. Assume all system calls are successful, and BUFSIZE is sufficiently large. (Look up any unfamiliar functions using the man command on your VM.) char buffer [BUFSIZE]; int fd = open("fooey",0_WRONLY | O_CREAT|O_TRUNC,0777); strcpy (buffer, "First data"); write(fd, buffer, strlen(buffer)); 1seek (fd, 90, SEEK_SET); strcpy (buffer, "Second data"); write(fd, buffer, strlen(buffer)); 1seek (fd, 100, SEEK_END); strpcy (buffer, "Third data"); write(fd, buffer, strlen(buffer)); close(fd); a. What is the size of the file at the end of this section of code? b. Describe the contents of the file say exactly what byte offsets contain actual data, and what offsets constitute "holes". c. Why might holey files be useful? d. Suppose, after the above sequence of writes, the same program opens the file for reading and then does: lseek (rfd, 130, SEEK_SET) ; read (rfd, buffer, 40); What will the read return, and what (if anything) will be placed in buffer?
Step by Step Solution
★★★★★
3.47 Rating (150 Votes )
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


