
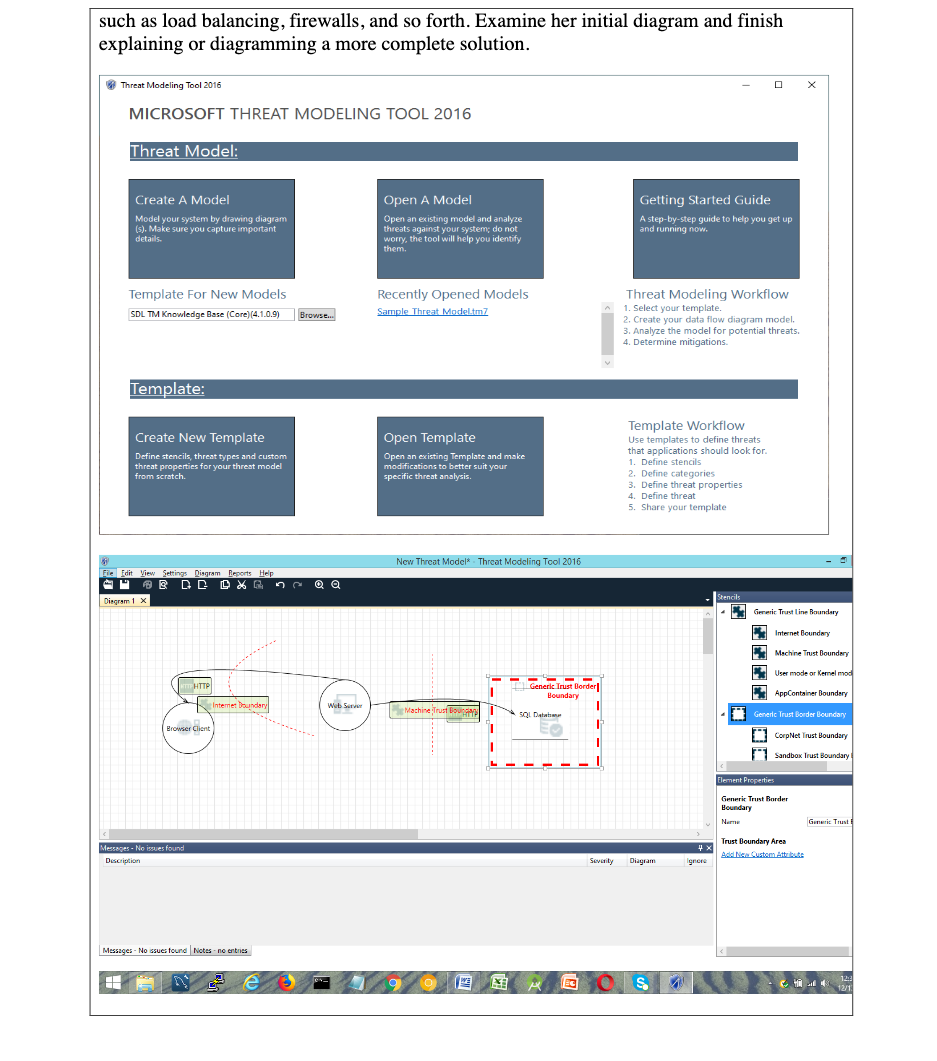
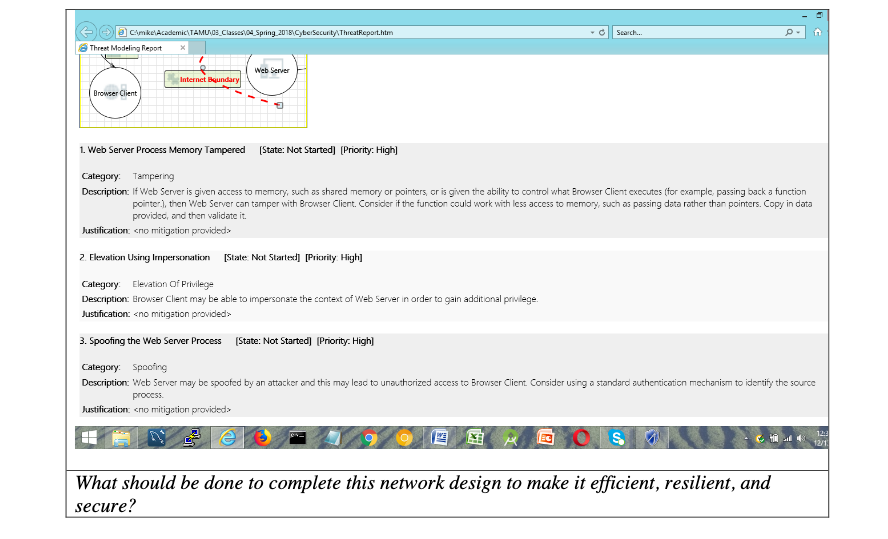
Mini-Case Activity: What Should Be Done? The following scenario involves a modeling activity. Explain what you would do to remediate these vulnerabilities in the network design. Episode: Lori used the Microsoft network modeling tool to design a zone with a webserver. Take a look at the diagram and a few of the errors generated, and explain what you would do to improve this network architecture. Interpret: Lori has modeled a webserver that is exposed to the Internet, and is just behind the trust boundary. It needs some things to improve the network architecture. The Microsoft modeling tool has provided some cybersecurity hints, but there are other considerations, such as load balancing, firewalls, and so forth. Examine her initial diagram and finish explaining or diagramming a more complete solution. Threat Modeling Tool 2016 MICROSOFT THREAT MODELING TOOL 2016 Threat Model: Create A Model Model your system by drawing diagram (s). Make sure you capture important details. Open A Model Open an existing model and analyze threats against your system do not worry, the tool will help you identify them. Getting Started Guide A step-by-step guide to help you get up and running now. Template For New Models SDL TM Knowledge Base (Core)(4.1.0.9) Recently Opened Models Sample Threat Modeltm7 Browse... Threat Modeling Workflow 1. Select your template. 2. Create your data flow diagram model. 3. Analyze the model for potential threats. 4. Determine mitigations Template: Create New Template Define stencils, threat types and custom threat properties for your threat model from scratch. Open Template Open an existing Template and make modifications to better suit your specific threat analysis. Template Workflow Use templates to define threats that applications should look for 1. Define stencils 2. Define categories 3. Define threat properties 4. Define threat 5. Share your template New Threat Model* Threat Modeling Tool 2016 File Edit View Settings Diagram Reports Help BD D D G Dingram 1 x Stencils Generic Trust Line Boundary Internet Boundary Machine Trust Boundary User mode or Kernel mod HTTP App Container Boundary Intemet boundary Generic Trust Dorder Boundary I SQL Data Web Surv Machine Trust Bourg Generic Trust Border Boundary Browser Client 1 1 CorpNet Trust Boundary 1 11 Sandbox Trust Boundary L Element Properties Generic Trust Border Boundary Name Generic Trust Messages - No issues found Description Trust Boundary Area Add New CustomAttribute Severity Diagram nor Messages - No ssues found Notes no entries HE 12:2 e S 12/1 Search... Cymke Academic TAMU_03_Classes 104 Spring 2015) bersecurity Threateport.htm Threat Modeling Report Web Server Internet sundary Browser Client 1. Web Server Process Memory Tampered [State: Not Started) (Priority: High) Category: Tampering Description: If Web Server is given access to memory, such as shared memory or pointers, or is given the ability to control what Browser Client executes (for example, passing back a function pointer.), then Wet Server can tamper with Browser Client. Consider it the function could work with less access to memory, such as passing data rather than pointers. Copy in data providec, and then validate it Justification: cno mitigation provided 2 Elevation Using Impersonation [State. Not Started] [Priority High] Category Elevation of Privilege Description: Browser Client may be able to impersonate the context of web server in order to gain additional privilege. Justification:









