Answered step by step
Verified Expert Solution
Question
1 Approved Answer
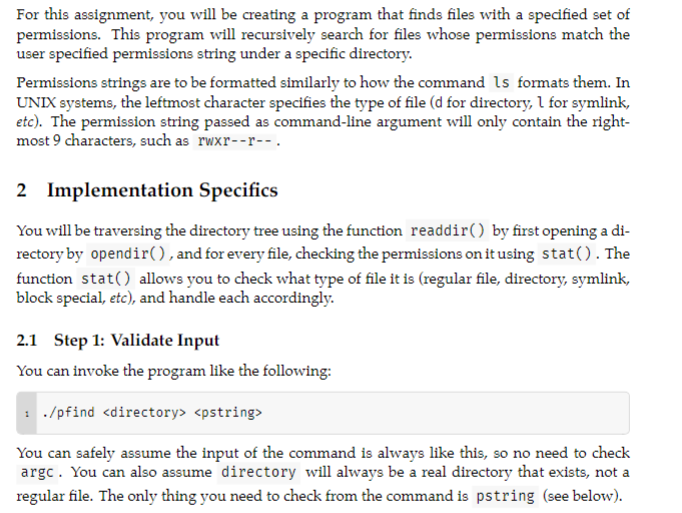
Must be done in C. For this assignment, you will be creating a program that finds files with a specified set of permissions. This program
Must be done in C.
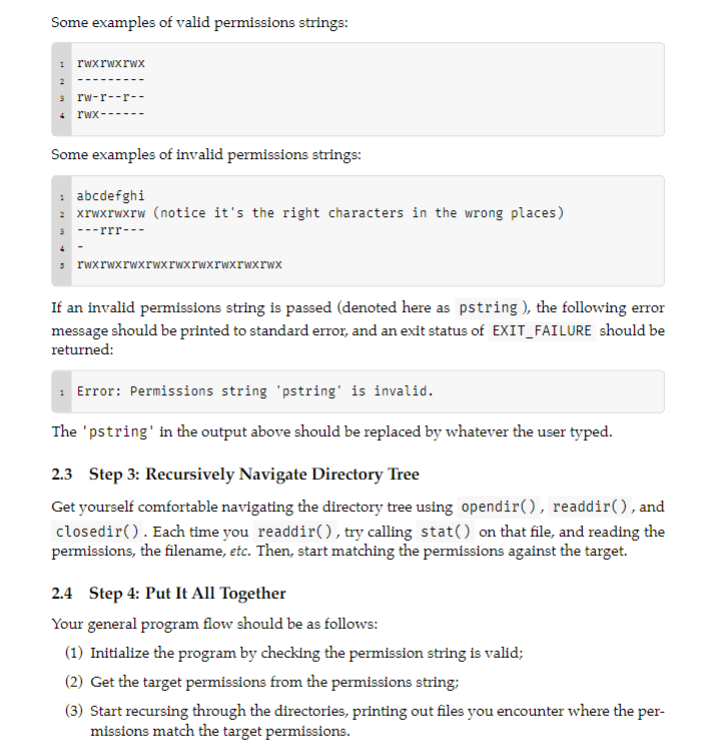
For this assignment, you will be creating a program that finds files with a specified set of permissions. This program will recursively search for files whose permissions match the user specified permissions string under a specific directory. Permissions strings are to be formatted similarly to how the command ls formats them. In UNIX systems, the leftmost character specifies the type of file ( d for directory, l for symlink, etc). The permission string passed as command-line argument will only contain the rightmost 9 characters, such as rwrr. 2 Implementation Specifics You will be traversing the directory tree using the function readdir( ) by first opening a directory by opendir ( ), and for every file, checking the permissions on it using stat ( ). The function stat() allows you to check what type of file it is (regular file, directory, symlink, block special, etc), and handle each accordingly. 2.1 Step 1: Validate Input You can invoke the program like the following: ./pfinddirectorypstring You can safely assume the input of the command is always like this, so no need to check argc. You can also assume directory will always be a real directory that exists, not a regular file. The only thing you need to check from the command is pstring (see below). 1234rwxrwxrwxrw-rrrwx Some examples of invalid permissions strings: : abcdefghi = xrwxrwxrw (notice it's the right characters in the wrong places) 3 --rrr-- 4 - 3 rwxrwxrwxrwxrwxrwxrwxrwxrwx If an invalid permissions string is passed (denoted here as pstring ), the following error message should be printed to standard error, and an exit status of EXIT_FAILURE should be returned: Error: Permissions string 'pstring' is invalid. The 'pstring' in the output above should be replaced by whatever the user typed. 2.3 Step 3: Recursively Navigate Directory Tree Get yourself comfortable navigating the directory tree using opendir(), readdir( ), and closedir(). Each time you readdir(), try calling stat() on that file, and reading the permissions, the filename, etc. Then, start matching the permissions against the target. 2.4 Step 4: Put It All Together Your general program flow should be as follows: (1) Initialize the program by checking the permission string is valid; (2) Get the target permissions from the permissions string; (3) Start recursing through the directories, printing out files you encounter where the permissions match the target permissionsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


