Need help to answer these with explanation please
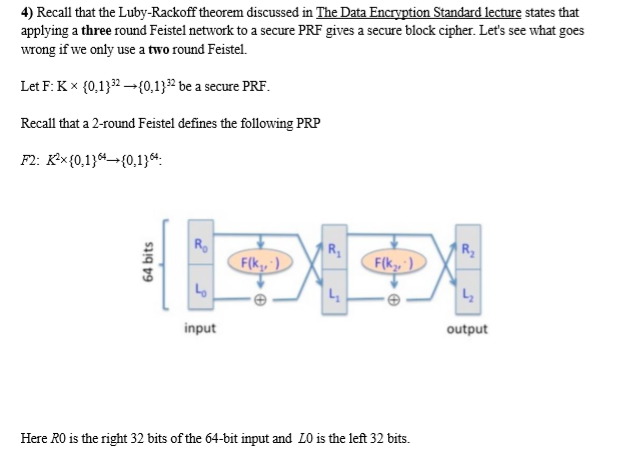

4) Recall that the Luby-Rackoff theorem discussed in The Data Encryption Standard lecture states that applying a three round Feistel network to a secure PRF gives a secure block cipher. Let's see what goes wrong if we only use a two round Feistel. Let F: K {0,1}32 {0,1}32 be a secure PRF Recall that a 2-round Feistel defines the following PRP input output Here RO is the right 32 bits of the 64-bit input and LO is the left 32 bits. One of the following lines is the output of this PRP F2 using a random key, while the other three are the output of a truly random permutation f. 0,1) 10,1) All 64-bit outputs are encoded as 16 hex characters. Can you say which is the output of the PRP? Note that since you are able to distinguish the output of F2 from random, F2 is not a secure block cipher, which is what we wanted to show. [0.5 points] Hint: First argue that there is a detectable pattern in the xor of F2, 0%) and F2(, 1520*2) Then try to detect this pattern in the given outputs. O On input 0s+ the output is "e86d2de2 e1387ae9". On input 10 the output is "1792d21d b645c008". On input 064 the output is " 5f67aba 521 0722b". On input 132032 the output s" bbe033c0 Obc9330e". D On input 0s+ the output is "7c2822eb fdc48bfb". On input 103 the output is "325032a9 c5e2364b". On input 0s4 the output is "7b50baab 07640c3d". On input 132032 the output is "ac343a22 cea46d60" 7) Nonce-based encryption has been implemented in HTTPS and IPSec design Please explain how nonce has been implemented in these two protocols. [0.5 point] HTTPS: IPSec: 4) Recall that the Luby-Rackoff theorem discussed in The Data Encryption Standard lecture states that applying a three round Feistel network to a secure PRF gives a secure block cipher. Let's see what goes wrong if we only use a two round Feistel. Let F: K {0,1}32 {0,1}32 be a secure PRF Recall that a 2-round Feistel defines the following PRP input output Here RO is the right 32 bits of the 64-bit input and LO is the left 32 bits. One of the following lines is the output of this PRP F2 using a random key, while the other three are the output of a truly random permutation f. 0,1) 10,1) All 64-bit outputs are encoded as 16 hex characters. Can you say which is the output of the PRP? Note that since you are able to distinguish the output of F2 from random, F2 is not a secure block cipher, which is what we wanted to show. [0.5 points] Hint: First argue that there is a detectable pattern in the xor of F2, 0%) and F2(, 1520*2) Then try to detect this pattern in the given outputs. O On input 0s+ the output is "e86d2de2 e1387ae9". On input 10 the output is "1792d21d b645c008". On input 064 the output is " 5f67aba 521 0722b". On input 132032 the output s" bbe033c0 Obc9330e". D On input 0s+ the output is "7c2822eb fdc48bfb". On input 103 the output is "325032a9 c5e2364b". On input 0s4 the output is "7b50baab 07640c3d". On input 132032 the output is "ac343a22 cea46d60" 7) Nonce-based encryption has been implemented in HTTPS and IPSec design Please explain how nonce has been implemented in these two protocols. [0.5 point] HTTPS: IPSec









