Answered step by step
Verified Expert Solution
Question
1 Approved Answer
need help with these two labs Hands-On Projects Project 1-1: Examining Data BreachesTextual The Privacy Rights Clearinghouse (PRC) is a nonprofit organization whose goals are


need help with these two labs
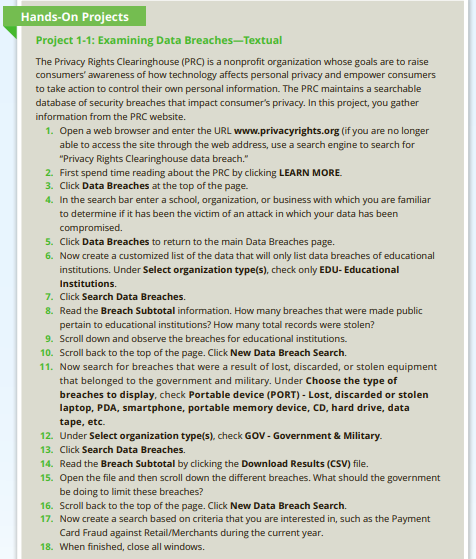
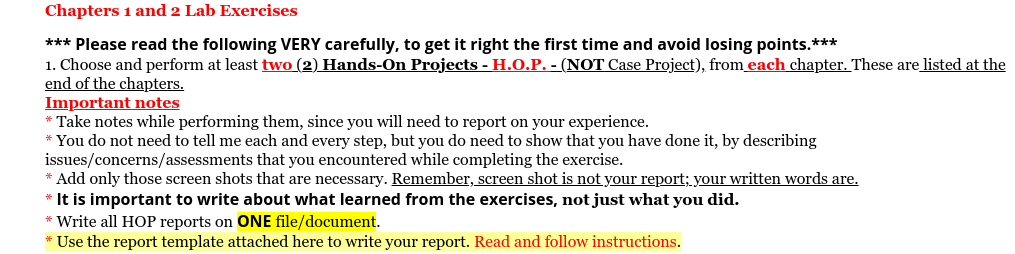
Hands-On Projects Project 1-1: Examining Data BreachesTextual The Privacy Rights Clearinghouse (PRC) is a nonprofit organization whose goals are to raise consumers' awareness of how technology affects personal privacy and empower consumers to take action to control their own personal information. The PRC maintains a searchable database of security breaches that impact consumer's privacy. In this project, you gather information from the PRC website. 1. Open a web browser and enter the URL www.privacyrights.org (if you are no longer able to access the site through the web address, use a search engine to search for "Privacy Rights Clearinghouse data breach." 2. First spend time reading about the PRC by clicking LEARN MORE. 3. Click Data Breaches at the top of the page. 4. In the search bar enter a school, organization, or business with which you are familiar to determine if it has been the victim of an attack in which your data has been compromised 5. Click Data Breaches to return to the main Data Breaches page. 6. Now create a customized list of the data that will only list data breaches of educational institutions. Under Select organization type(s), check only EDU- Educational Institutions 7. Click Search Data Breaches. 8. Read the Breach Subtotal information. How many breaches that were made public pertain to educational institutions? How many total records were stolen? 9. Scroll down and observe the breaches for educational institutions. 10. Scroll back to the top of the page. Click New Data Breach Search. 11. Now search for breaches that were a result of lost, discarded, or stolen equipment that belonged to the government and military. Under Choose the type of breaches to display, check Portable device (PORT) - Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc. 12. Under Select organization type(s), check GOV - Government & Military. 13. Click Search Data Breaches. 14. Read the Breach Subtotal by clicking the Download Results (CSV) file. 15. Open the file and then scroll down the different breaches. What should the government be doing to limit these breaches? 16. Scroll back to the top of the page. Click New Data Breach Search. 17. Now create a search based on criteria that you are interested in, such as the Payment Card Fraud against Retail/Merchants during the current year. 18. When finished, close all windows. Project 1-3: Scanning for Malware Using the Microsoft Safety Scanner In this project, you download and run the Microsoft Safety Scanner to determine if there is any malware on the computer. 1. Determine which system type of Windows you are running. Click Start, Settings. System, and then About this PC. Look under System type for the description. Open your web browser and enter the URL www.microsoft.com/security/scanner /en-us/default.asp (if you are no longer able to access the site through the URL, use a search engine to search for "Microsoft Safety Scanner"). 2. Click Download Now. 3. Select either 32-bit or 64-bit, depending upon which system type of Windows you are running 4. When the program finishes downloading, right-click Start and click File Explorer. 5. Click the Downloads icon in the left pane. 6. Double-click the msert.exe file. 7. If the User Account Control dialog box appears, click Yes. Click Run. 8. Click the check box to accept the license terms for this software. Click Next. 9. Click Next. 10. Select Quick scan if necessary. 11. Click Next 12. Depending on your computer this scan may take several minutes. Analyze the results of the scan to determine if there is any malicious software found in your computer. 13. If you have problems, you can click View detailed results of the scan. After reviewing the results, click OK. If you do not find any problems, click Finish. 14. If any malicious software was found on your computer run the scan again and select Full scan. After the scan is complete, click Finish to close the dialog box. 15. Close all windows. WSX Lab Report (replace X with the weekset number) Then, repeat the format below for each HOP (Hands-On Project) lab report. Note that HOP is NOT Case Project. Project x-y (x is the chapter number and y is the HOP number, for example: project 1-3" is for chapter is HOP 3. Observation (what did you do, see, notice?) Write a short paragraph. You may add a couple of screen-shots. Answer the lab questions Answer any HOP step that has a question in it (i.e. has "?") Indicate the step # for each answer Conclusion (what did you learn from completing this?) Write a short paragraph. Chapters 1 and 2 Lab Exercises *** Please read the following VERY carefully, to get it right the first time and avoid losing points.*** 1. Choose and perform at least two (2) Hands-On Projects - H.O.P. - (NOT Case Project), from each chapter. These are listed at the end of the chapters. Important notes * Take notes while performing them, since you will need to report on your experience. * You do not need to tell me each and every step, but you do need to show that you have done it, by describing issues/concerns/assessments that you encountered while completing the exercise. * Add only those screen shots that are necessary. Remember, screen shot is not your report; your written words are. * It is important to write about what learned from the exercises, not just what you did. * Write all HOP reports on ONE file/document. * Use the report template attached here to write your report. Read and follow instructions. Hands-On Projects Project 1-1: Examining Data BreachesTextual The Privacy Rights Clearinghouse (PRC) is a nonprofit organization whose goals are to raise consumers' awareness of how technology affects personal privacy and empower consumers to take action to control their own personal information. The PRC maintains a searchable database of security breaches that impact consumer's privacy. In this project, you gather information from the PRC website. 1. Open a web browser and enter the URL www.privacyrights.org (if you are no longer able to access the site through the web address, use a search engine to search for "Privacy Rights Clearinghouse data breach." 2. First spend time reading about the PRC by clicking LEARN MORE. 3. Click Data Breaches at the top of the page. 4. In the search bar enter a school, organization, or business with which you are familiar to determine if it has been the victim of an attack in which your data has been compromised 5. Click Data Breaches to return to the main Data Breaches page. 6. Now create a customized list of the data that will only list data breaches of educational institutions. Under Select organization type(s), check only EDU- Educational Institutions 7. Click Search Data Breaches. 8. Read the Breach Subtotal information. How many breaches that were made public pertain to educational institutions? How many total records were stolen? 9. Scroll down and observe the breaches for educational institutions. 10. Scroll back to the top of the page. Click New Data Breach Search. 11. Now search for breaches that were a result of lost, discarded, or stolen equipment that belonged to the government and military. Under Choose the type of breaches to display, check Portable device (PORT) - Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc. 12. Under Select organization type(s), check GOV - Government & Military. 13. Click Search Data Breaches. 14. Read the Breach Subtotal by clicking the Download Results (CSV) file. 15. Open the file and then scroll down the different breaches. What should the government be doing to limit these breaches? 16. Scroll back to the top of the page. Click New Data Breach Search. 17. Now create a search based on criteria that you are interested in, such as the Payment Card Fraud against Retail/Merchants during the current year. 18. When finished, close all windows. Project 1-3: Scanning for Malware Using the Microsoft Safety Scanner In this project, you download and run the Microsoft Safety Scanner to determine if there is any malware on the computer. 1. Determine which system type of Windows you are running. Click Start, Settings. System, and then About this PC. Look under System type for the description. Open your web browser and enter the URL www.microsoft.com/security/scanner /en-us/default.asp (if you are no longer able to access the site through the URL, use a search engine to search for "Microsoft Safety Scanner"). 2. Click Download Now. 3. Select either 32-bit or 64-bit, depending upon which system type of Windows you are running 4. When the program finishes downloading, right-click Start and click File Explorer. 5. Click the Downloads icon in the left pane. 6. Double-click the msert.exe file. 7. If the User Account Control dialog box appears, click Yes. Click Run. 8. Click the check box to accept the license terms for this software. Click Next. 9. Click Next. 10. Select Quick scan if necessary. 11. Click Next 12. Depending on your computer this scan may take several minutes. Analyze the results of the scan to determine if there is any malicious software found in your computer. 13. If you have problems, you can click View detailed results of the scan. After reviewing the results, click OK. If you do not find any problems, click Finish. 14. If any malicious software was found on your computer run the scan again and select Full scan. After the scan is complete, click Finish to close the dialog box. 15. Close all windows. WSX Lab Report (replace X with the weekset number) Then, repeat the format below for each HOP (Hands-On Project) lab report. Note that HOP is NOT Case Project. Project x-y (x is the chapter number and y is the HOP number, for example: project 1-3" is for chapter is HOP 3. Observation (what did you do, see, notice?) Write a short paragraph. You may add a couple of screen-shots. Answer the lab questions Answer any HOP step that has a question in it (i.e. has "?") Indicate the step # for each answer Conclusion (what did you learn from completing this?) Write a short paragraph. Chapters 1 and 2 Lab Exercises *** Please read the following VERY carefully, to get it right the first time and avoid losing points.*** 1. Choose and perform at least two (2) Hands-On Projects - H.O.P. - (NOT Case Project), from each chapter. These are listed at the end of the chapters. Important notes * Take notes while performing them, since you will need to report on your experience. * You do not need to tell me each and every step, but you do need to show that you have done it, by describing issues/concerns/assessments that you encountered while completing the exercise. * Add only those screen shots that are necessary. Remember, screen shot is not your report; your written words are. * It is important to write about what learned from the exercises, not just what you did. * Write all HOP reports on ONE file/document. * Use the report template attached here to write your report. Read and follow instructionsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


