Question: No. Time Source Destination Protocol 1 0.000000 192.168.23.55 100.168.0.4 TI Info 50678 > 23 [SYN) Seq=0 Win=32120 Len=0 MSS-1460... 23 > 50678 (SYN, ACK] Seq=0
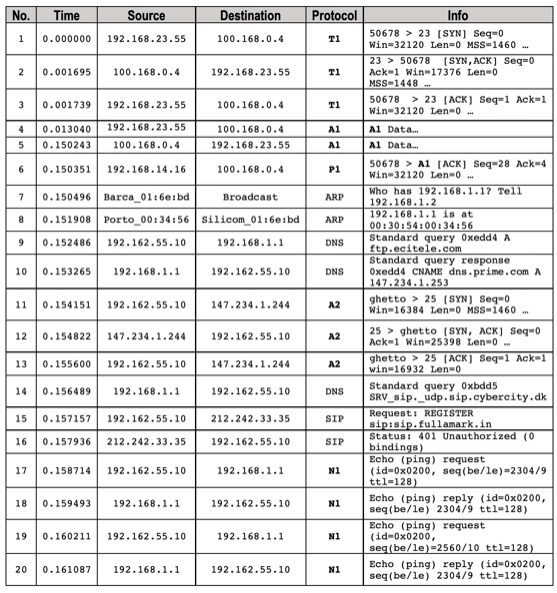
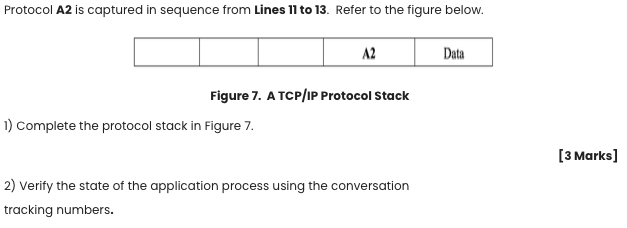
No. Time Source Destination Protocol 1 0.000000 192.168.23.55 100.168.0.4 TI Info 50678 > 23 [SYN) Seq=0 Win=32120 Len=0 MSS-1460... 23 > 50678 (SYN, ACK] Seq=0 Ack-1 Win-17376 Len=0 MSS-1448 .. 50678 > 23 [ACK] Seq=1 Ack=1 Win-32120 Len-0. 2 0.001695 100.168.0.4 192.168.23.55 T1 3 0.001739 192.168.23.55 100.168.0.4 T1 4 192.168.23.55 0.013040 0.150243 100.168.0.4 192.168.23.55 A1 A1 A1 Data... A1 Data... 5 100.168.0.4 6 0.150351 192.168.14.16 100.168.0.4 P1 7 Broadcast ARP 8 0.150496 Barca_01:6e: bd 0.151908 Porto_00:34:56 0.152486 192.162.55.10 ARP Silicom_01:6e:bd 192.168.1.1 9 DNS 10 0.153265 192.168.1.1 192.162.55.10 DNS 11 0.154151 192.162.55.10 147.234.1.244 A2 147.234.1.244 192.162.55.10 A2 192.162.55.10 147.234.1.244 A2 12 0.154822 13 0.155600 14 0.156489 15 0.157157 50678 > A1 [ACK) Seq-28 Ack-4 Win32120 Leno... Who has 192.168.1.1? Tell 192.168.1.2 192.168.1.1 is at 00:30:54:00:34:56 Standard query Oxedd4 A ftp.ecitele.com Standard query response Oxedd4 CNAME dns.prime.com A 147.234.1.253 ghetto > 25 (SYN) Seq0 Win=16384 Len=0 MSS-1460 ... 25 > ghetto (SYN, ACK) Seq=0 Ack-1 Win=25398 Len=0 - ghetto > 25 (ACK) Seq-1 Ack=1 win-16932 Len=0 Standard query Oxbdd5 SRV_sip._udp.sip.cybercity.dk Request: REGISTER sipisip. fullamark.in Status: 401 Unauthorized (0 bindings) Echo (ping) request (id=0x0200, seg(be/le)-2304/9 ttl=128) Echo (ping) reply (id=0x0200, seg(be/le) 2304/9 ttl=128) Echo (ping) request (id=0x0200, seq(be/le)=2560/10 ttl=128) Echo (ping) reply (id=0x0200, seg(be/le) 2304/9 ttl=128) 192.168.1.1 DNS 192.162.55.10 212.242.33.35 SIP 192.162.55.10 212.242.33.35 16 0.157936 192.162.55.10 SIP 17 0.158714 192.162.55.10 192.168.1.1 NI 18 0.159493 192.168.1.1 192.162.55.10 NI 19 0.160211 192.162.55.10 192.168.1.1 N1 20 0.161087 192.168.1.1 192.162.55.10 NI Protocol A2 is captured in sequence from Lines 11 to 13. Refer to the figure below. A2 Data Figure 7. A TCP/IP Protocol Stack 1) Complete the protocol stack in Figure 7. (3 Marks) 2) Verify the state of the application process using the conversation tracking numbers
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


