Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Now you have all these little pieces to encrypt and decrypt your code but it is not put together yet using all the function separately
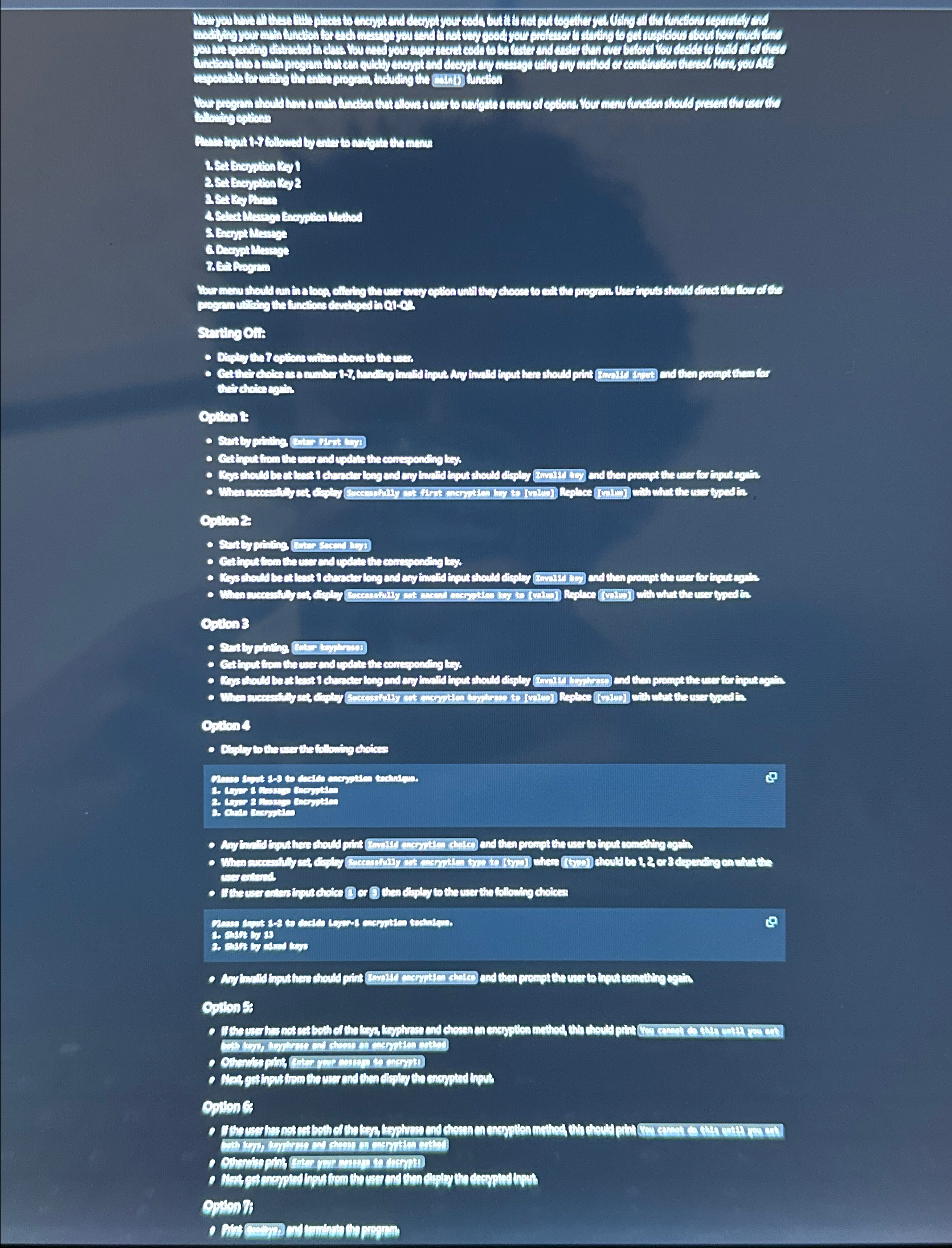
Now you have all these little pieces to encrypt and decrypt your code but it is not put together yet using all the function separately and modifying your main function for each message you send is not very good your professor starting to get suspicious about how much time you are spending distracted in class you need your super secret code to be faster and easier than ever before you decide to build all of these function into a main program that can quickly encrypt and decrypt any message using any method or combination there of here you are responsible for writing the entire program including the main function your program should have a main function that allows a user to navigate a menu of options your menu function should present the user the following options please input one through seven followed by enter to navigate the menu
Set encryption key
Set Encryption key
Set key phrase
Select message encryption method
Encrypt message
Decrypt message
Exit program
Y Your menu should run in a loop offering the user every option until they choose to exit the program user input should direct the flow of the program utilizing the functions develops in Q through Q
Stating off: Display the seven options are written above to the user get their choice as a number one through seven handling invalid input any invalid input here should print invalid input and then prompt them for their choice again option one start by printing enter first key get input from the user and update the corresponding key key should be at least one character long and any invalid input should display invalid key and then prompt the user for input again when successfully set display successfully set first encryption key to value replace value with what the user typed in option to start by printing enter second key get input from the user and update the corresponding key key should be at least one character long and any invalid input should display invalid key and then prompt the user for input again when successfully set display successfully set second encryption key to value replace value with what the user typed in option three start by printing enter key phrase get input from the user and update the corresponding key key should be at least one character long and in any invalid input should display invalid key phrase and then prompted the user for input again when successfully set display successfully set encryption key phrase to value replace value with what the user typed in option for display to the user of the following choices please input one through three to decide encryption technique one layer one encryption two layer two message encryption three chain encryption any invalid input here should print invalid encryption choice and then promptly user input something else with successfully set display successfully set encryption type to type where type should be or three depending on what the user entered if the user enters input choice one or three then the display to the user the following choices please input one through two to decide layer one encryption technique one shift by to shift by mixed keys any invalid input here should print invalid encryption choice and then prompt the user to input something again option five if the user has not set both of the keys key phrase and chosen an encryption method this should print you cannot do this until you set both keys key phrase and chosen an encryption method otherwise print into your message to encrypt get input from the user and then display the encrypted input option six if the user has not set both of the keys key phrases and chosen encryption method they should print you cannot do this until you set both keys key phrase and chosen encryption method otherwise print enter your message to decrypt next get encrypted input from the user and then display the decrypted input option seven print goodbye and terminate the program
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


