Question
Objective: Upon completion of this activity, you will be able to discuss the operation of different types of network firewalls. Student Instructions: Read Chapter 22
Objective:
Upon completion of this activity, you will be able to discuss the operation of different types of network firewalls.
Student Instructions:
Read Chapter 22 of the William Stallings textbook ( Cryptography and Network Security Principles and Practice Fifth Edition William Stallings ). Answer the following questions about network firewalls.
a. List three design goals for a firewall.
b. List four techniques used by firewalls to control access and enforce a security policy.
c. What information is used by a typical packet filtering firewall?
d. What are some weaknesses of a packet filtering firewall?
e. What is the difference between a packet filtering firewall and a stateful inspection firewall?
f. What is an application-level gateway?
g. What is a circuit-level gateway?
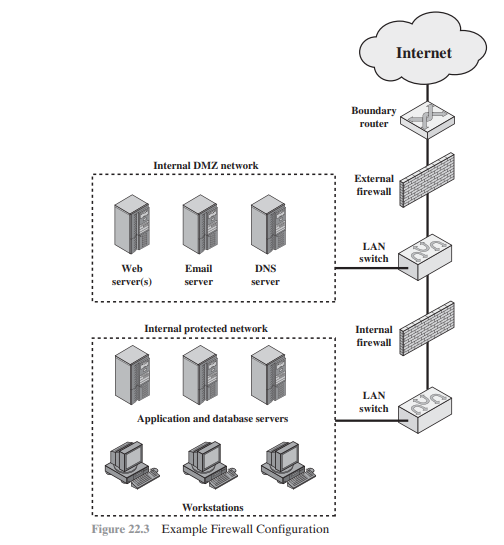
h. What are the differences between firewalls in Figures 2 and 3?
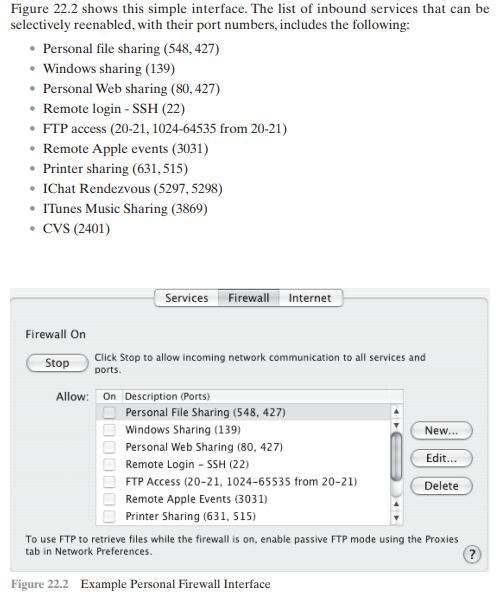
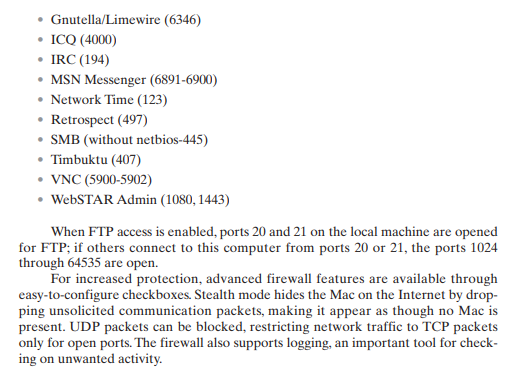
Figure 3
i. Why is it useful to have host-based firewalls?
j. What is the difference between an internal and an external firewall?
Figure 22.2 shows this simple interface. The list of inbound services that can be selectively reenabled, with their port numbers, includes the following: - Personal file sharing (548,427) - Windows sharing (139) - Personal Web sharing (80,427) - Remote login - SSH (22) - FTP access (20-21, 1024-64535 from 20-21) - Remote Apple events (3031) - Printer sharing (631,515) - IChat Rendezvous (5297, 5298) - ITunes Music Sharing (3869) - CVS (2401) Firewall On Click Stop to allow incoming network communication to all services and ports. Allow: On Description (Ports) Personal File Sharing (548,427) Windows Sharing (139) Personal Web Sharing (80,427) Remote Login - SSH (22) FTP Access (20-21, 1024-65535 from 20-21) Remote Apple Events (3031) Printer Sharing (631,515) To use FTP to retrieve files while the firewall is on, enable passive FTP mode using the Proxies tab in Network Preferences. (?) Figure 22.2 Example Personal Firewall Interface When FTP access is enabled, ports 20 and 21 on the local machine are opened for FTP; if others connect to this computer from ports 20 or 21 , the ports 1024 through 64535 are open. For increased protection, advanced firewall features are available through easy-to-configure checkboxes. Stealth mode hides the Mac on the Internet by dropping unsolicited communication packets, making it appear as though no Mac is present. UDP packets can be blocked, restricting network traffic to TCP packets only for open ports. The firewall also supports logging, an important tool for checking on unwanted activityStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


