only answer if you can do them all please
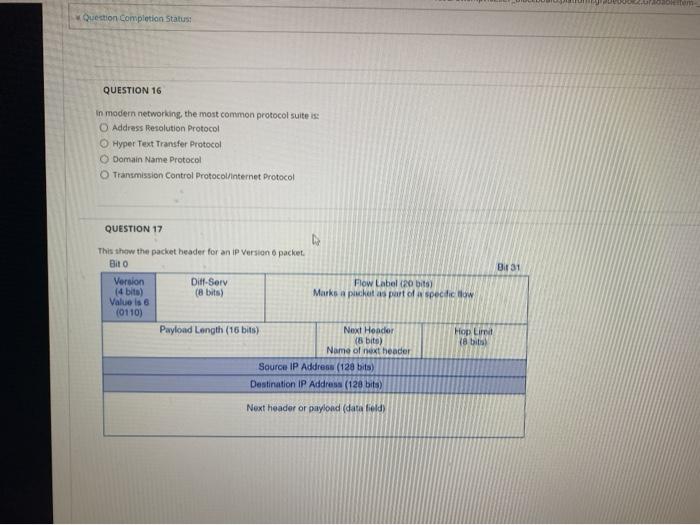
ou estion Completion Statut QUESTION 3 Members of hacker groups LulzSec and Anonymous used this type of attack to steal millions of user account information from Sony Corporation in 2017 a SQL Injection Attack b. Social Engineering Attack Oc Brute Force Attack Od Spear Phishing Attack QUESTION 4 A Trojan Horse la program that hides itself by deleting a system file and taking on the system is name. Tre b QUESTIONS Acer has stects her target performed reconnaissance on the potential target's network and probed active foternet Addresses and hosts, what does the stor the targets network to see if any are open! O OME O MAC Address OS Server Stampa QUESTIONS no and HTTP foods are types of Sounction attacks True Question Completion Status: QUESTION 7 Under the US. Gramm-Leach-alley Act companies must report whether they have any materal control deficencies in their financial reporting process True False QUESTIONS This 2002 Act was enacted to bolster computer and network Security within the federal goverment and affiliated parties byundating ewlyades Sarbanes-Oxley Act HIDMA O European Union Data Protection Directive Federal information Security Management Act QUESTIONS in a company, what does "CSO stand for? QUESTION 10 in classic risk analysis cakulations. "Exposure Factor is the amount of damage that would be sustained in a sing breach True ale QUESTION 11 Whenponding to make surance for your company is a type of his voidante A. ultradense 414965_//outline?legacyurt-252Fwebapps%252Fcalendar 1.252Flaunch4252Fattemota badboard platform.gradebook2.Gradableltem.3106549.1 Question Completion Status QUESTION 12 What is the difference between "Data and Information ? For the toolbar, press ALT F10 Por ALT+FN+F10(Mac). BIU & Paragraph Arial 14px EM A LIN a 2 F QUESTION 13 Athreat agere is a specific instance of a potential threat being realised True Olse QUESTION 14 Aeroday plot some previously unknown vulnerability in a system QUESTION 15 What does stand for QUESTION 16 Question Completion Status: QUESTION 16 In modern networking the most common protocol suite is Address Resolution Protocol Hyper Text Transfer Protocol Domain Name Protocol Transmission Control Protocol/internet Protocol QUESTION 17 This show the packet header for an IP Version 6 packet. Bilo Bit 31 Version (4 bits) Value is 6 (0110) Diff-Serv (8 bits) Flow Label (20 bits) Marks a pickutas part of a specielow Hop Limit (8 bits Payload Length (16 bits) Next Header (8 bits) Name of next beader Source IP Address (128 bits) Destination IP Address (128 bits) Next header or payload (data field) ou estion Completion Statut QUESTION 3 Members of hacker groups LulzSec and Anonymous used this type of attack to steal millions of user account information from Sony Corporation in 2017 a SQL Injection Attack b. Social Engineering Attack Oc Brute Force Attack Od Spear Phishing Attack QUESTION 4 A Trojan Horse la program that hides itself by deleting a system file and taking on the system is name. Tre b QUESTIONS Acer has stects her target performed reconnaissance on the potential target's network and probed active foternet Addresses and hosts, what does the stor the targets network to see if any are open! O OME O MAC Address OS Server Stampa QUESTIONS no and HTTP foods are types of Sounction attacks True Question Completion Status: QUESTION 7 Under the US. Gramm-Leach-alley Act companies must report whether they have any materal control deficencies in their financial reporting process True False QUESTIONS This 2002 Act was enacted to bolster computer and network Security within the federal goverment and affiliated parties byundating ewlyades Sarbanes-Oxley Act HIDMA O European Union Data Protection Directive Federal information Security Management Act QUESTIONS in a company, what does "CSO stand for? QUESTION 10 in classic risk analysis cakulations. "Exposure Factor is the amount of damage that would be sustained in a sing breach True ale QUESTION 11 Whenponding to make surance for your company is a type of his voidante A. ultradense 414965_//outline?legacyurt-252Fwebapps%252Fcalendar 1.252Flaunch4252Fattemota badboard platform.gradebook2.Gradableltem.3106549.1 Question Completion Status QUESTION 12 What is the difference between "Data and Information ? For the toolbar, press ALT F10 Por ALT+FN+F10(Mac). BIU & Paragraph Arial 14px EM A LIN a 2 F QUESTION 13 Athreat agere is a specific instance of a potential threat being realised True Olse QUESTION 14 Aeroday plot some previously unknown vulnerability in a system QUESTION 15 What does stand for QUESTION 16 Question Completion Status: QUESTION 16 In modern networking the most common protocol suite is Address Resolution Protocol Hyper Text Transfer Protocol Domain Name Protocol Transmission Control Protocol/internet Protocol QUESTION 17 This show the packet header for an IP Version 6 packet. Bilo Bit 31 Version (4 bits) Value is 6 (0110) Diff-Serv (8 bits) Flow Label (20 bits) Marks a pickutas part of a specielow Hop Limit (8 bits Payload Length (16 bits) Next Header (8 bits) Name of next beader Source IP Address (128 bits) Destination IP Address (128 bits) Next header or payload (data field)