Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Part 1: Part 2 Please only answer the question if you are 100% sure You are a penetration tester running port scans on a server.
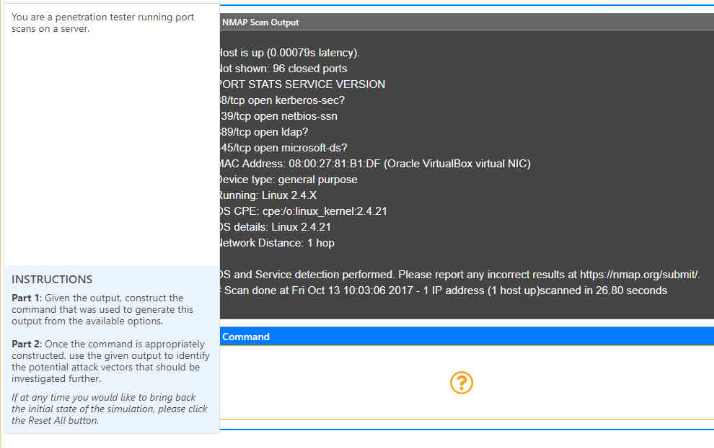
Part 1:
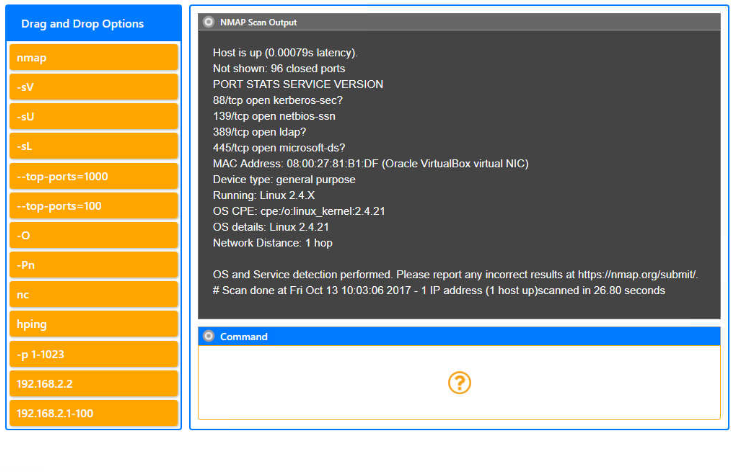
Part 2
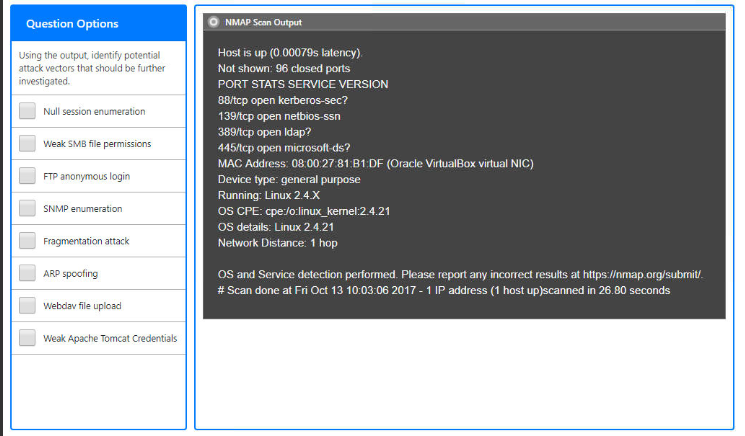
Please only answer the question if you are 100% sure
You are a penetration tester running port scans on a server. NMAP Scan Output Host is up (0.00079s latency). Hot shown: 96 closed ports ORT STATS SERVICE VERSION 8/tcp open kerberos-sec? 39/tcp open netbios-san 89/tcp open Idap? 45/tcp open microsoft ds? MAC Address: 08:00 27.81 B1 DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4 X DS CPE: cpe/o:linux_kernel:2.4.21 details: Linux 2.4.21 Hetwork Distance: 1 hop INSTRUCTIONS ps and Service detection performed. Please report any incorrect results at https:/map org/submit/ Part 1: Given the output construct the Scan done at Fri Oct 13 10:03:06 2017-1 IP address (1 host up)scanned in 26.80 seconds command that was used to generate this output from the available options. Part 2: Once the command is appropriately Command constructed, use the given output to identify the potential attack vectors that should be investigated further If at any time you would like to bring back the initial state of the simulation, please click the Reset All button Drag and Drop Options NMAP Scan Output nmap -SV -SU -SL Host is up (0.00079s latency) Not shown: 96 closed ports PORT STATS SERVICE VERSION 88/tcp open kerberos-sec? 139/tcp open netbios-ssn 389/tcp openldap? 445/tcp open microsoft ds? MAC Address: 08:00:27 81:B1 DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4.X OS CPE: cpe:/o:linux_kernel:2.4.21 OS details: Linux 2.4.21 Network Distance: 1 hop --top-ports=1000 --top-ports=100 -O -Pn OS and Service detection performed. Please report any incorrect results at https:/map.org/submit/ # Scan done at Fri Oct 13 10:03:06 2017-1 IP address (1 host up)scanned in 26.80 seconds nc hping Command -p 1-1023 192.168.2.2 192.168.2.1-100 Question Options NMAP Scan Output Using the output, identify potential attack vectors that should be further investigated. Null session enumeration Weak SMB file permissions Host is up (0.00079s latency) Not shown: 96 closed ports PORT STATS SERVICE VERSION 88/tcp open kerberos-sec? 139/tcp open netbios-ssn 389/tcp open Idap? 445/tcp open microsoft ds? MAC Address: 08:00:27 81:B1DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4x OS CPE: cpe:/o:linux_kernel:2.4.21 OS details: Linux 2.4.21 Network Distance: 1 hop FTP anonymous login SNMP enumeration Fragmentation attack ARP spoofing OS and Service detection performed. Please report any incorrect results at https:/map.org/submit/ #Scan done at Fri Oct 13 10:03:06 2017 - 1 IP address (1 host up)scanned in 26.80 seconds Webdav file upload Weak Apache Tomcat Credentials You are a penetration tester running port scans on a server. NMAP Scan Output Host is up (0.00079s latency). Hot shown: 96 closed ports ORT STATS SERVICE VERSION 8/tcp open kerberos-sec? 39/tcp open netbios-san 89/tcp open Idap? 45/tcp open microsoft ds? MAC Address: 08:00 27.81 B1 DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4 X DS CPE: cpe/o:linux_kernel:2.4.21 details: Linux 2.4.21 Hetwork Distance: 1 hop INSTRUCTIONS ps and Service detection performed. Please report any incorrect results at https:/map org/submit/ Part 1: Given the output construct the Scan done at Fri Oct 13 10:03:06 2017-1 IP address (1 host up)scanned in 26.80 seconds command that was used to generate this output from the available options. Part 2: Once the command is appropriately Command constructed, use the given output to identify the potential attack vectors that should be investigated further If at any time you would like to bring back the initial state of the simulation, please click the Reset All button Drag and Drop Options NMAP Scan Output nmap -SV -SU -SL Host is up (0.00079s latency) Not shown: 96 closed ports PORT STATS SERVICE VERSION 88/tcp open kerberos-sec? 139/tcp open netbios-ssn 389/tcp openldap? 445/tcp open microsoft ds? MAC Address: 08:00:27 81:B1 DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4.X OS CPE: cpe:/o:linux_kernel:2.4.21 OS details: Linux 2.4.21 Network Distance: 1 hop --top-ports=1000 --top-ports=100 -O -Pn OS and Service detection performed. Please report any incorrect results at https:/map.org/submit/ # Scan done at Fri Oct 13 10:03:06 2017-1 IP address (1 host up)scanned in 26.80 seconds nc hping Command -p 1-1023 192.168.2.2 192.168.2.1-100 Question Options NMAP Scan Output Using the output, identify potential attack vectors that should be further investigated. Null session enumeration Weak SMB file permissions Host is up (0.00079s latency) Not shown: 96 closed ports PORT STATS SERVICE VERSION 88/tcp open kerberos-sec? 139/tcp open netbios-ssn 389/tcp open Idap? 445/tcp open microsoft ds? MAC Address: 08:00:27 81:B1DF (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 2.4x OS CPE: cpe:/o:linux_kernel:2.4.21 OS details: Linux 2.4.21 Network Distance: 1 hop FTP anonymous login SNMP enumeration Fragmentation attack ARP spoofing OS and Service detection performed. Please report any incorrect results at https:/map.org/submit/ #Scan done at Fri Oct 13 10:03:06 2017 - 1 IP address (1 host up)scanned in 26.80 seconds Webdav file upload Weak Apache Tomcat CredentialsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


