Part of Seed Labs 2.0 for Seed Ubuntu 20.04 (Firewall Exploration)
The 2.C firewall rules:
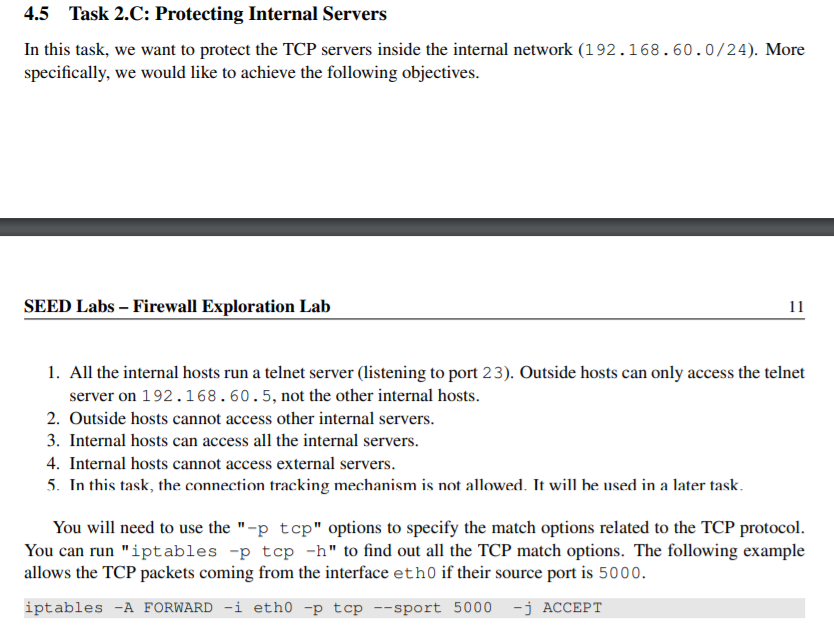
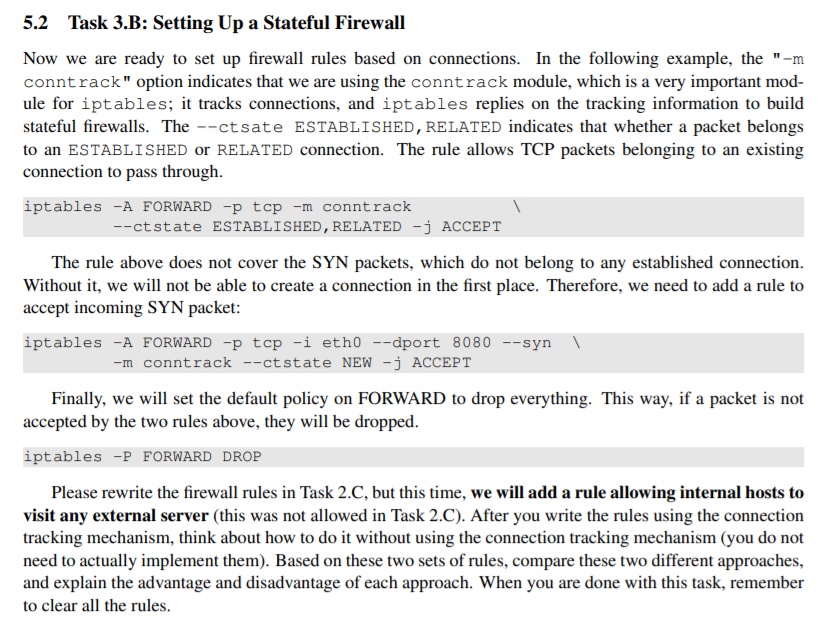
5.2 Task 3.B: Setting Up a Stateful Firewall Now we are ready to set up firewall rules based on connections. In the following example, the "-m conntrack" option indicates that we are using the conntrack module, which is a very important mod- ule for iptables; it tracks connections, and iptables replies on the tracking information to build stateful firewalls. The --tsate ESTABLISHED, RELATED indicates that whether a packet belongs to an ESTABLISHED or RELATED connection. The rule allows TCP packets belonging to an existing connection to pass through. iptables -A FORWARD -p tcp -m contrack --ctstate ESTABLISHED, RELATED -j ACCEPT The rule above does not cover the SYN packets, which do not belong to any established connection. Without it, we will not be able to create a connection in the first place. Therefore, we need to add a rule to accept incoming SYN packet: iptables -A FORWARD -p top -i eth0 --dport 8080 --syn -m contrack --ct state NEW -j ACCEPT Finally, we will set the default policy on FORWARD to drop everything. This way, if a packet is not accepted by the two rules above, they will be dropped. iptables -P FORWARD DROP Please rewrite the firewall rules in Task 2.C, but this time, we will add a rule allowing internal hosts to visit any external server (this was not allowed in Task 2.C). After you write the rules using the connection tracking mechanism, think about how to do it without using the connection tracking mechanism (you do not need to actually implement them). Based on these two sets of rules, compare these two different approaches, and explain the advantage and disadvantage of each approach. When you are done with this task, remember to clear all the rules. 4.5 Task 2.C: Protecting Internal Servers In this task, we want to protect the TCP servers inside the internal network (192.168.60.0/24). More specifically, we would like to achieve the following objectives. SEED Labs - Firewall Exploration Lab 11 1. All the internal hosts run a telnet server (listening to port 23). Outside hosts can only access the telnet server on 192.168.60.5, not the other internal hosts. 2. Outside hosts cannot access other internal servers. 3. Internal hosts can access all the internal servers. 4. Internal hosts cannot access external servers. 5. In this task, the connection tracking mechanism is not allowed. It will be used in a later task. You will need to use the "-p tcp" options to specify the match options related to the TCP protocol. You can run "iptables -p tcp -h" to find out all the TCP match options. The following example allows the TCP packets coming from the interface eth0 if their source port is 5000. iptables -A FORWARD -i etho -p tcp --sport 5000 -j ACCEPT








