Answered step by step
Verified Expert Solution
Question
1 Approved Answer
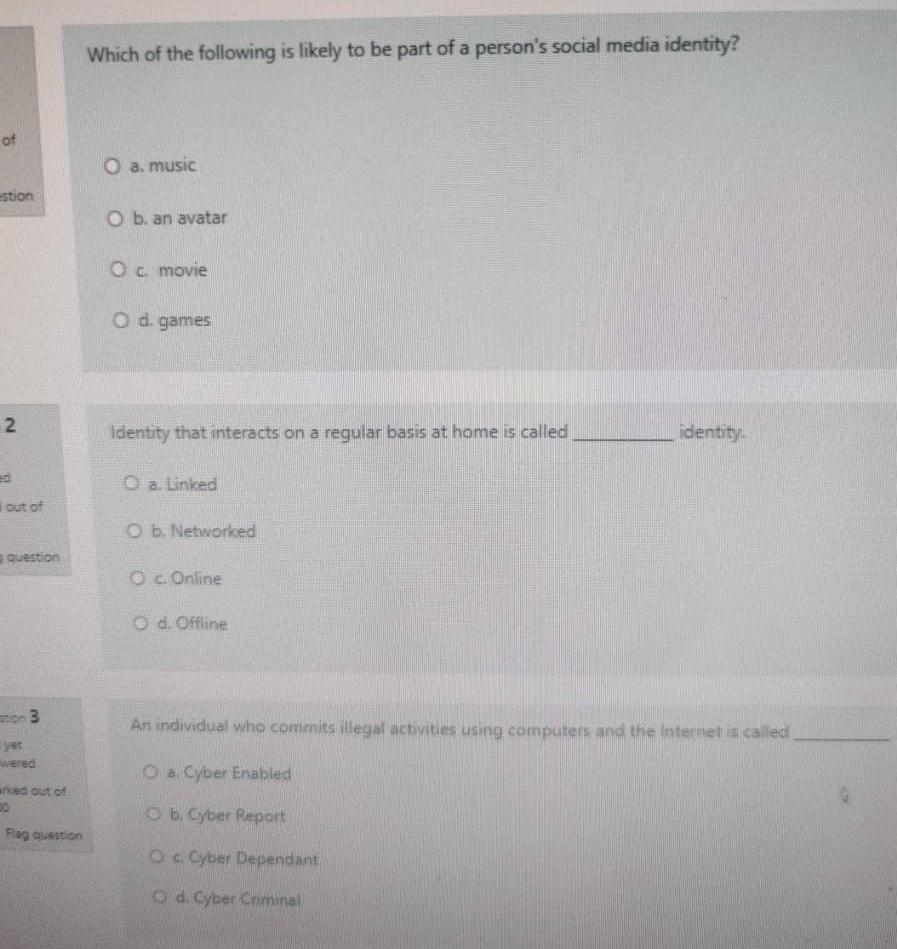
Please answer all questions Which of the following is likely to be part of a person's social media identity? of O a. music estion O
Please answer all questions
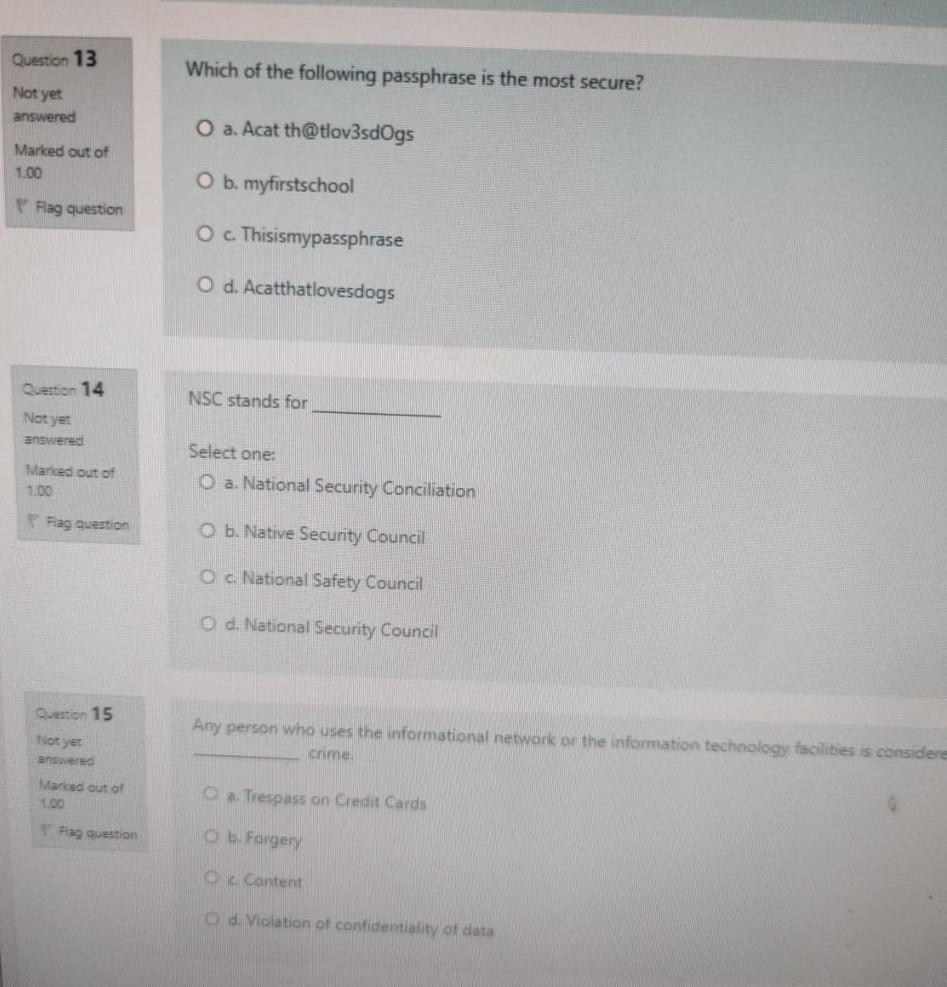
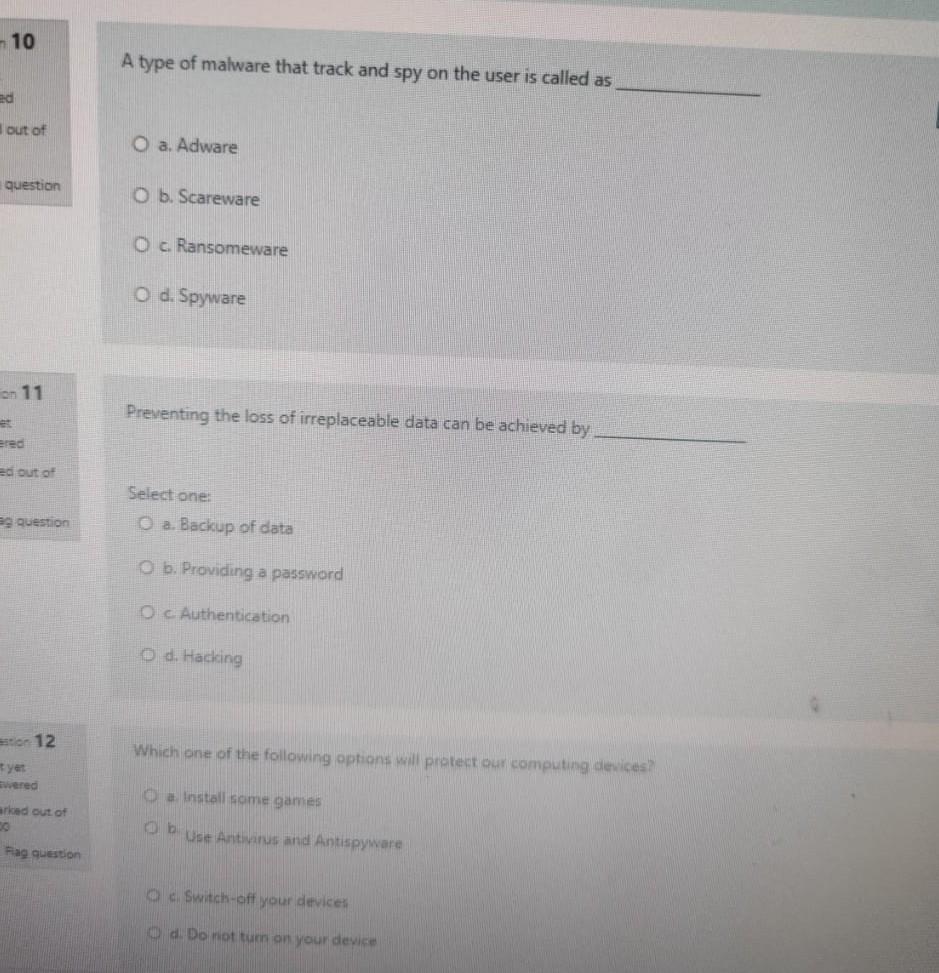
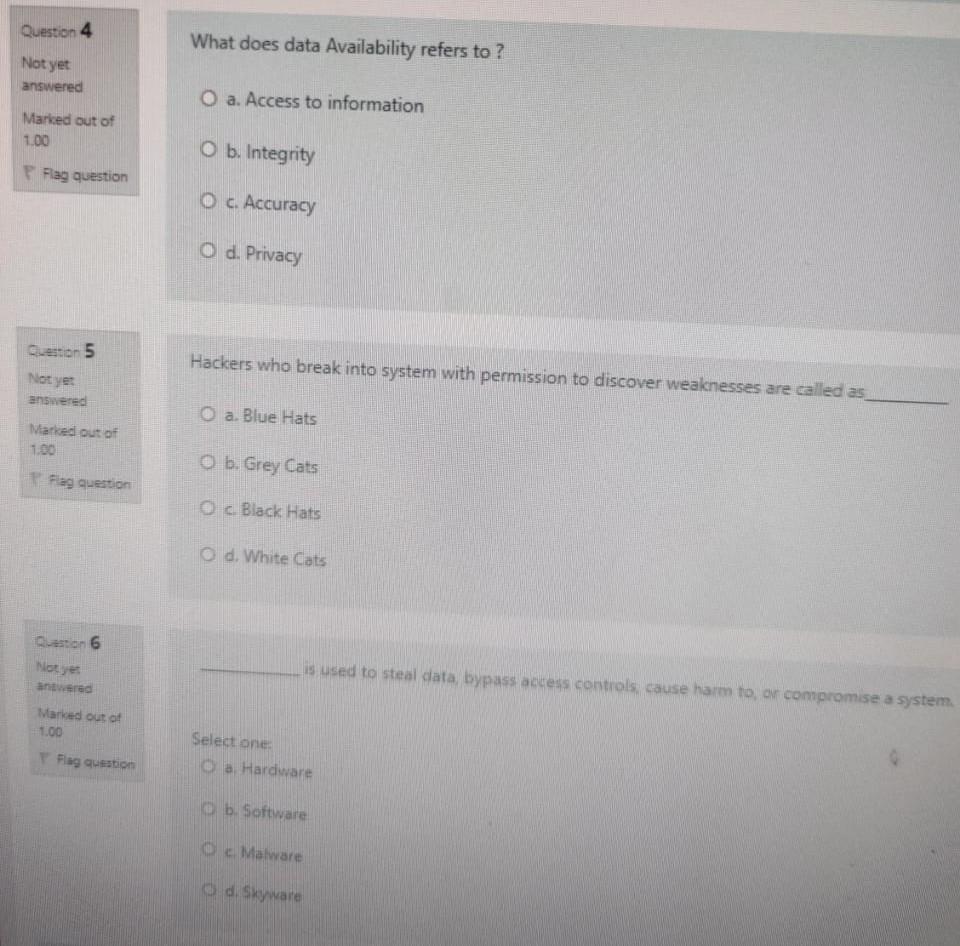
Which of the following is likely to be part of a person's social media identity? of O a. music estion O b. an avatar O c. movie O d.games N Identity that interacts on a regular basis at home is called identity ed O a. Linked out of O b. Networked question Oc Online d. Offline An individual who commits illegal activities using computers and the Internet is called a Cyber Enabled ried out of O b. Cyber Report Flag question Oc Cyber Dependant d. Cyber Criminal Question 13 Which of the following passphrase is the most secure? Not yet answered O a. Acat th@tlov3sdogs Marked out of 1.00 O b. myfirstschool Flag question O c. Thisismypassphrase O d. Acatthatlovesdogs Question 14 NSC stands for Not yet answered Marked out of 1.00 Select one: O a. National Security Conciliation Piag question O b. Native Security Council O c National Safety Council O d. National Security Council Question 15 Not yet Any person who uses the informational network on the information technology facilities is considere Crime Nanted out of 1.00 a. Trespass on Credit Cards Fag guestion Ob Forgery Oc Content d. Violation of confidentiality of data 10 A type of malware that track and spy on the user is called as ed out of O a. Adware question O b. Scareware O c Ransomeware O d. Spyware on 11 Preventing the loss of irreplaceable data can be achieved by ered ed out of Select one: O a. Backup of data e question O b. Providing a password O c Authentication d. Hacking on 12 tyet wered Which one of the following options will protect our computing devices? a Install some games arked out of Ob Ust Antivirus and Antispyware Fag question O c. Switch-off your devices d. Do not tum on your device Question 4 What does data Availability refers to ? Not yet answered O a. Access to information Marked out of 1.00 O b. Integrity Flag question . Accuracy O d. Privacy Question 5 Hackers who break into system with permission to discover weaknesses are called as Not yet answered O a. Blue Hats Narked out of 1.00 b. Grey Cats Flag question O c Black Hats d. White Cats Queston 6 is used to steal data, bypass access controls cause harm toon compromise a system Not yes anted Marked out of 1.00 Flag question Select one: ca Hardware b. Software Malware O di Skyware A type of malware that carries out malicious operations under the guise of a desired operation is 3 ed out of Select one: O a. Virus question O b. Worm O c Rootkit O d. Trojan horse on 8 Data that is written beyond the limits of a buffer is known as ed out of Select one O a. Trojan Horse e question b. Rootkits Oc Buffer Overflow Od. Worm on 9 Which one of the following is a symptoms of Malware a. Memory is not used ked out of Ob There are unknown processes running Fag question OCPU speed is very high d. Increase in Web browsing speed
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


