Answered step by step
Verified Expert Solution
Question
1 Approved Answer
PLEASE ASAP Assuming the following Java servlet code generates query. There is an SQL injection vulnerablity in the generated query (qry). Which of the variable
PLEASE ASAP 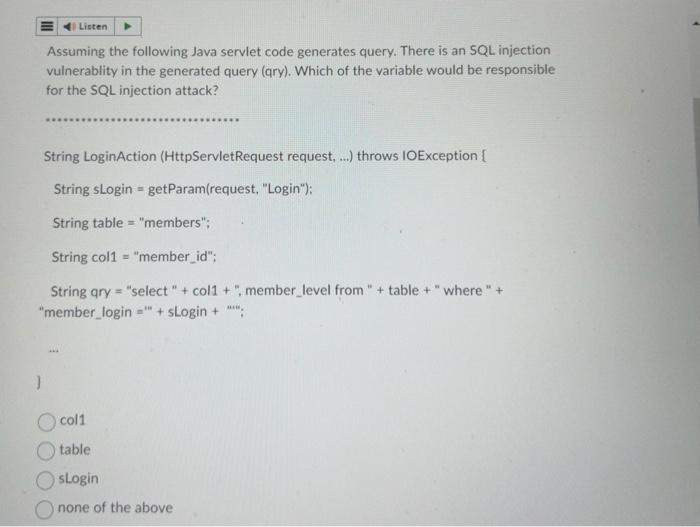
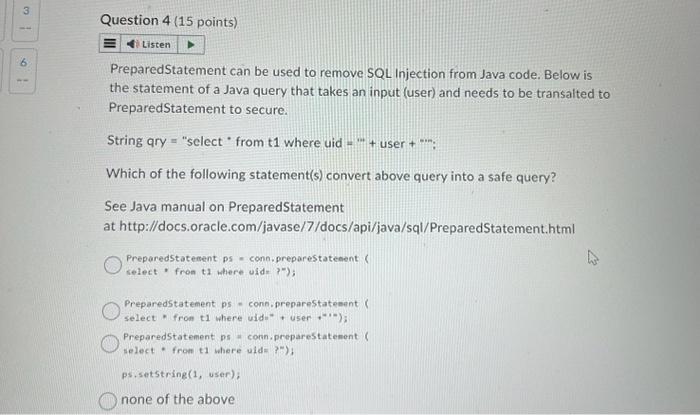
Assuming the following Java servlet code generates query. There is an SQL injection vulnerablity in the generated query (qry). Which of the variable would be responsible for the SQL injection attack? String LoginAction (HttpServletRequest request, ...) throws IOException \{ String sLogin = getParam(request, "Login"): String table = "members"; String col1 = "member_id"; String qry = "select " + col 1+ ", member_level from " + table + " where " + "member_login =" " + sLogin + "w"; col1 table sLogin none of the above PreparedStatement can be used to remove SQL Injection from Java code. Below is the statement of a Java query that takes an input (user) and needs to be transalted to PreparedStatement to secure. String qry = "select from t1 where uid =+ user +; Which of the following statement(s) convert above query into a safe query? See Java manual on PreparedStatement at http://docs.oracle.com/javase/7/docs/api/java/sql/PreparedStatement.html Preparedstatement ps = conn. preparestatenent ( select * fron t1 where uide P"); Preparedstatement ps - conn, preparestatement ( select * from t1 where uidi* + user )j; Preparedstatement iss = conn. preparestatement ( select - fron t1 where uld ?") ; psisetstring(1, user); none of the above 

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


