Question: please check before sending me and please dont use gets,thank you very much! Write a C program decode.c which decrypts text encrypted by substitution.c For
please check before sending me and please dont use gets,thank you very much!
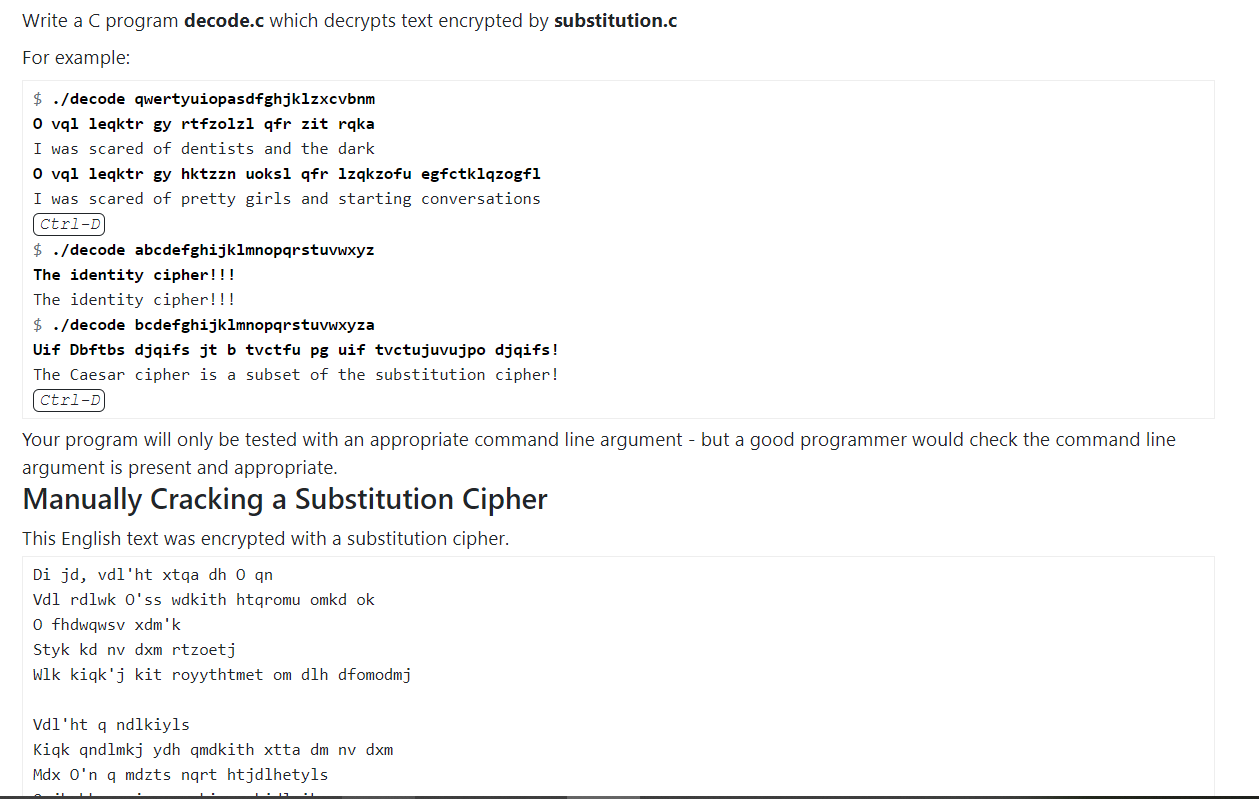
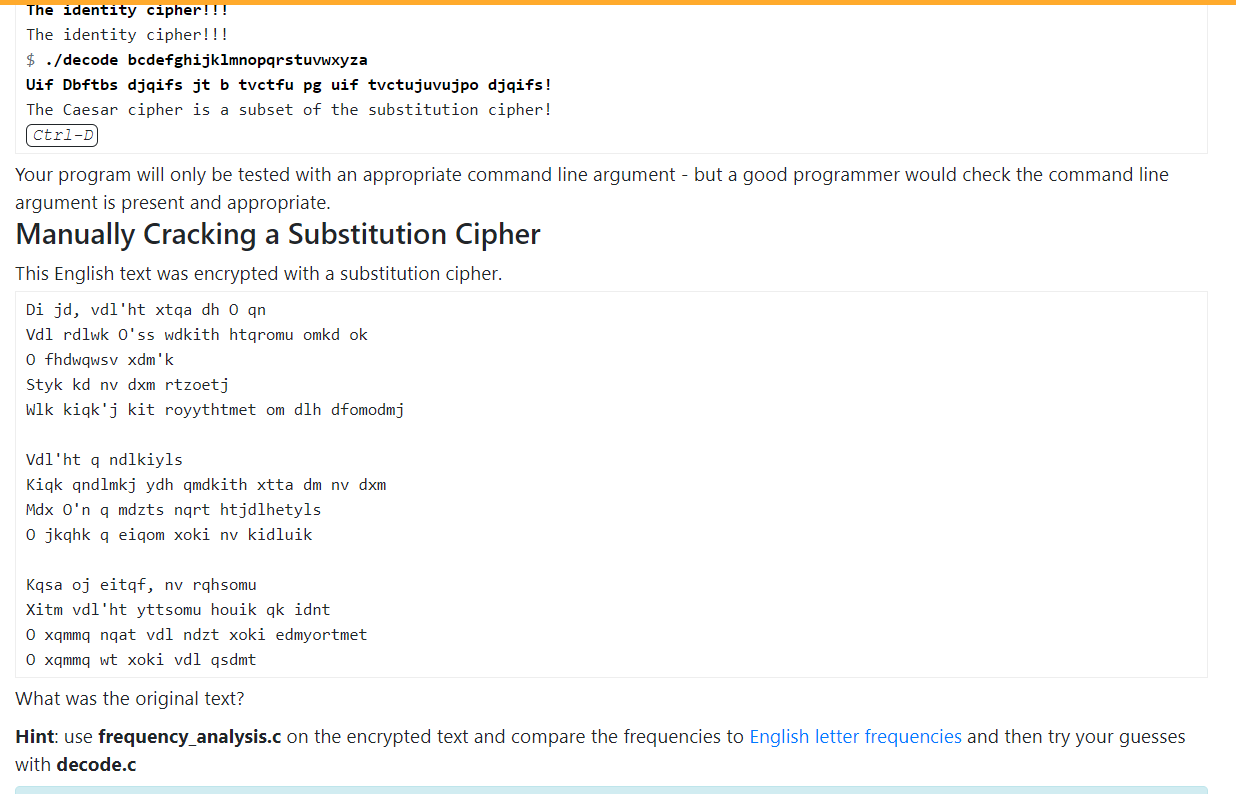
Write a C program decode.c which decrypts text encrypted by substitution.c For example: $ ./decode qwertyuiopasdfghjklzxcvbnm Ovql leqktr gy rtfzolzl qfr zit raka I was scared of dentists and the dark Ovql leqktr gy hktzzn uoksl qfr lzqkzofu egfctklqzogfi I was scared of pretty girls and starting conversations Ctrl-D $ ./decode abcdefghijklmnopqrstuvwxyz The identity cipher!!! The identity cipher!!! $ ./decode bcdefghijklmnopqrstuvwxyza Uif Dbftbs djqifs jt b tvctfu pg uif tvetujuvujpo djqifs! The Caesar cipher is a subset of the substitution cipher! Ctrl-D Your program will only be tested with an appropriate command line argument - but a good programmer would check the command line argument is present and appropriate. Manually Cracking a Substitution Cipher This English text was encrypted with a substitution cipher. Di jd, vdl'ht xtqa dh O qn Vdl rdlwk O'ss wdkith htqromu omkd ok O fhdwqwsv xdm'k Styk kd nv dxm rtzoetj Wlk kiqk'j kit royythtmet om dlh dfomodmj Vdl'ht q ndlkiyls Kiqk qndlmkj ydh qmdkith xtta dm nv dxm Mdx O'n q mdzts nart htjdlhetyls The identity cipher!!! The identity cipher!!! $ ./decode bcdefghijklmnopqrstuvwxyza Uif Dbftbs djqifs jt b tvctfu pg uif tvctujuvujpo djqifs! The Caesar cipher is a subset of the substitution cipher! (Ctrl-D Your program will only be tested with an appropriate command line argument - but a good programmer would check the command line argument is present and appropriate. Manually Cracking a Substitution Cipher This English text was encrypted with a substitution cipher. Di jd, vdl'ht xtqa dh O an Vdl rdlwk O'ss wdkith htqromu omkd ok O fhdwwsv xdm'k Styk kd nv dxm rtzoetj Wlk kiqk'j kit royythtmet om dlh dfomodmj Vdl'ht q ndlkiyls Kick qndlmkj ydh qmdkith xtta dm nv dxm Mdx O'n q mdzts nart htjdlhetyls O jkqhk q eiqom xoki nv kidluik Kasa oj eitqf, nv rahsomu Xitm vdl'ht yttsomu houik gk idnt O xqmmq nqat vdl ndzt xoki edmyortmet O xqmmq wt xoki vdl qsdmt What was the original text? Hint: use frequency_analysis.c on the encrypted text and compare the frequencies to English letter frequencies and then try your guesses with decode.c
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


