Answered step by step
Verified Expert Solution
Question
1 Approved Answer
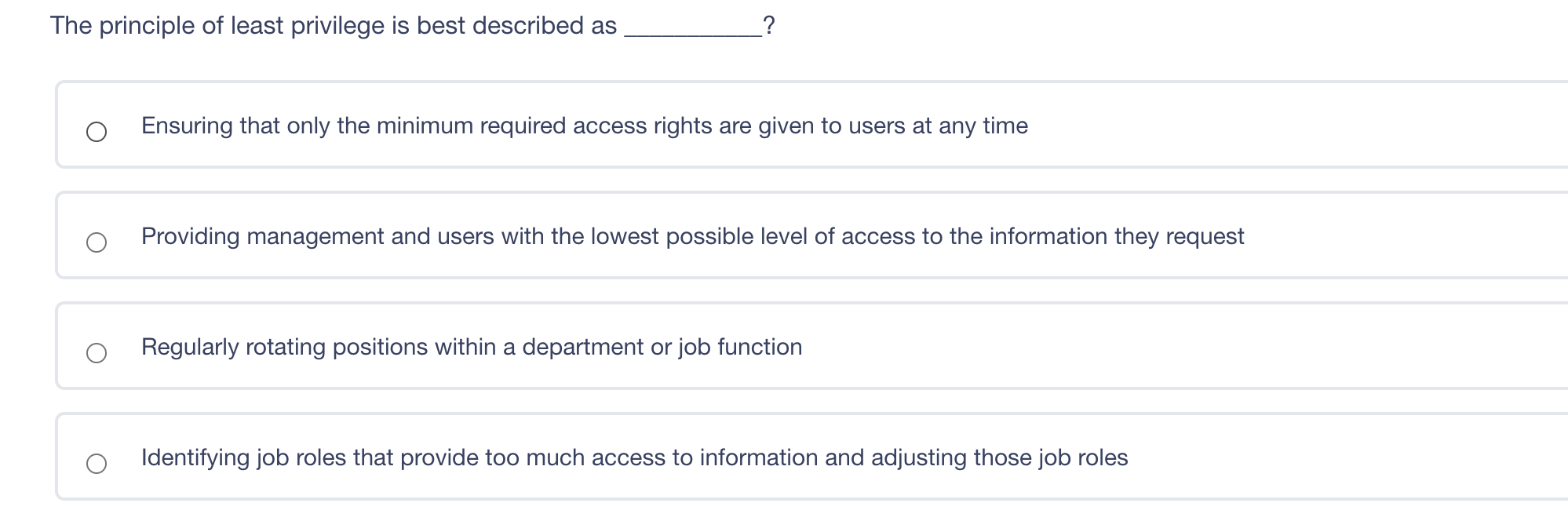
Please give all Questions anwers to get thumbs up The principle of least privilege is best described as ? Ensuring that only the minimum required
Please give all Questions anwers to get thumbs up
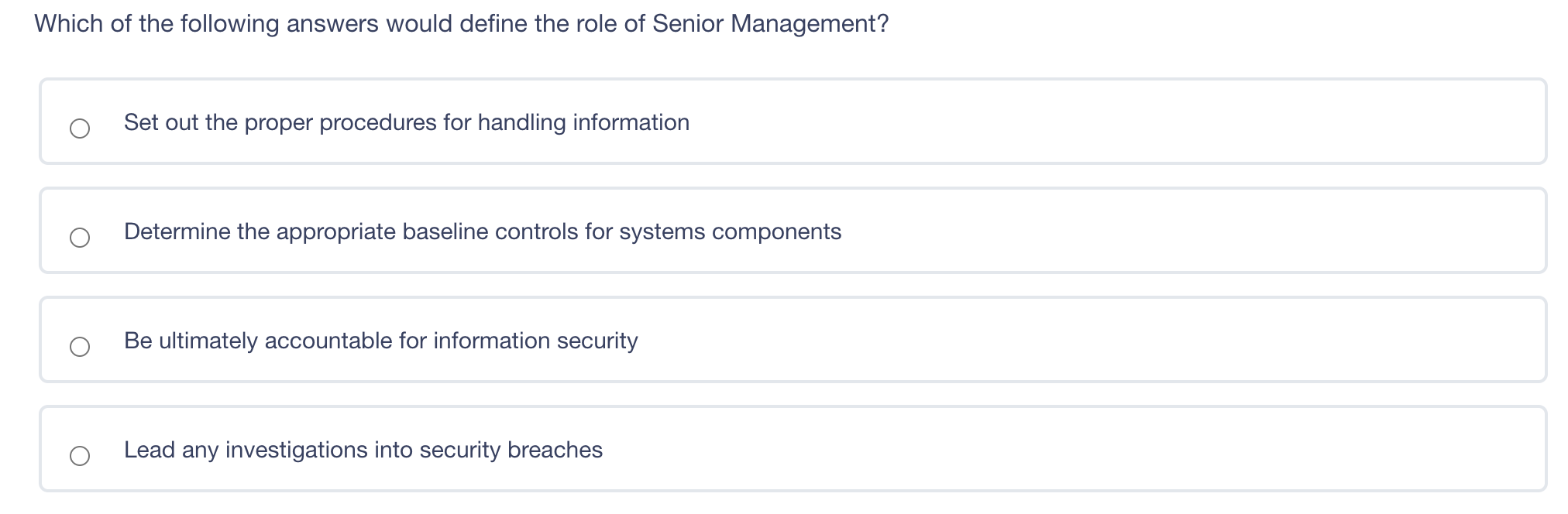
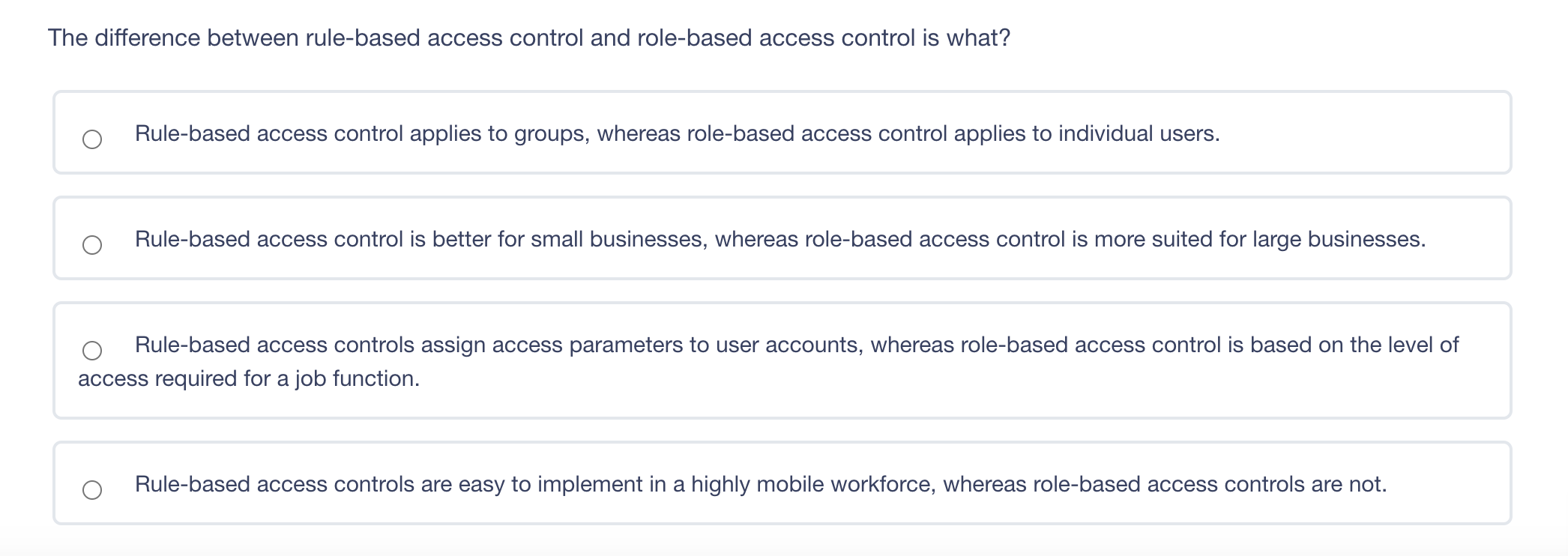
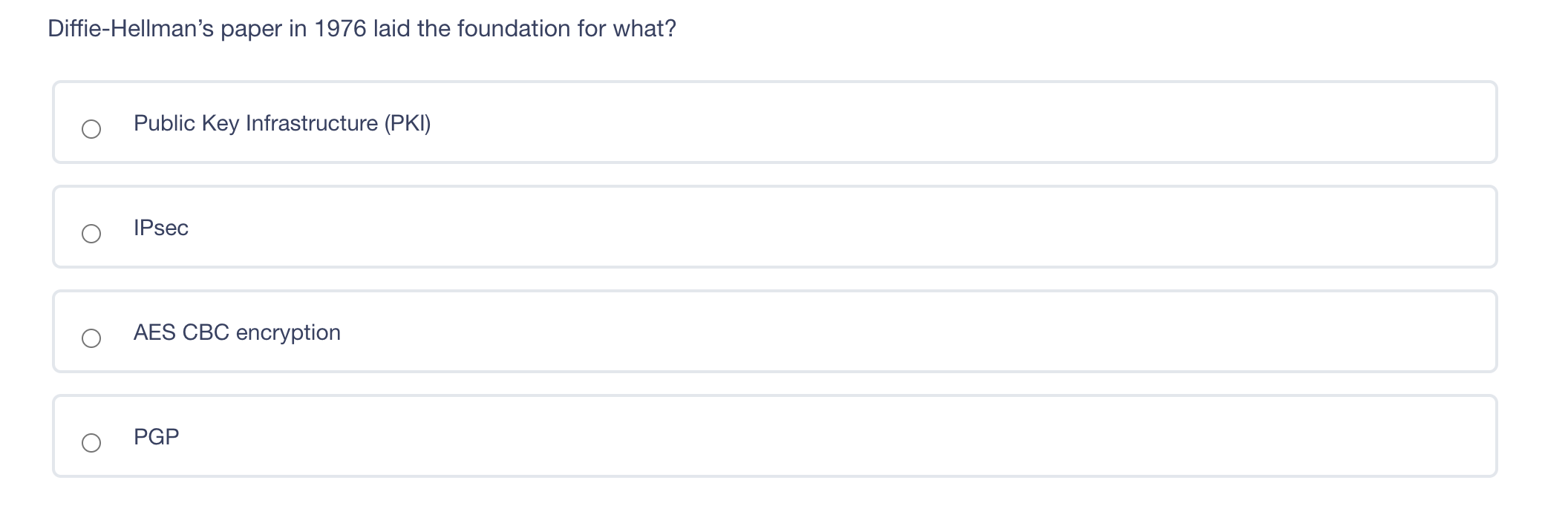
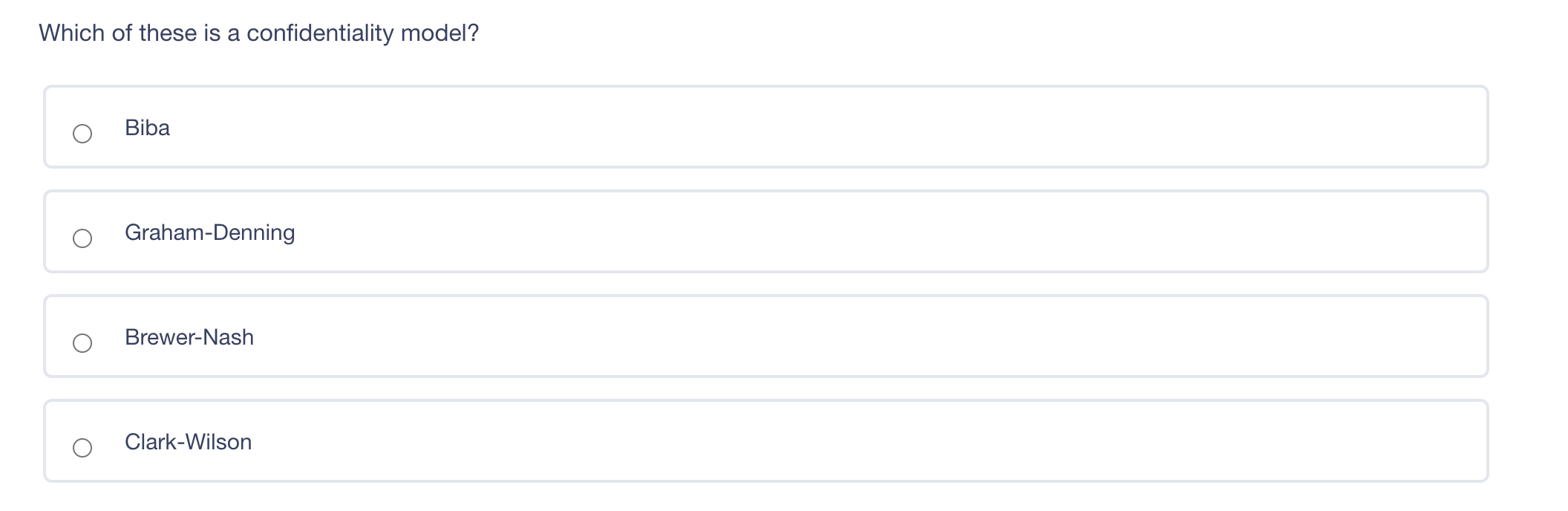
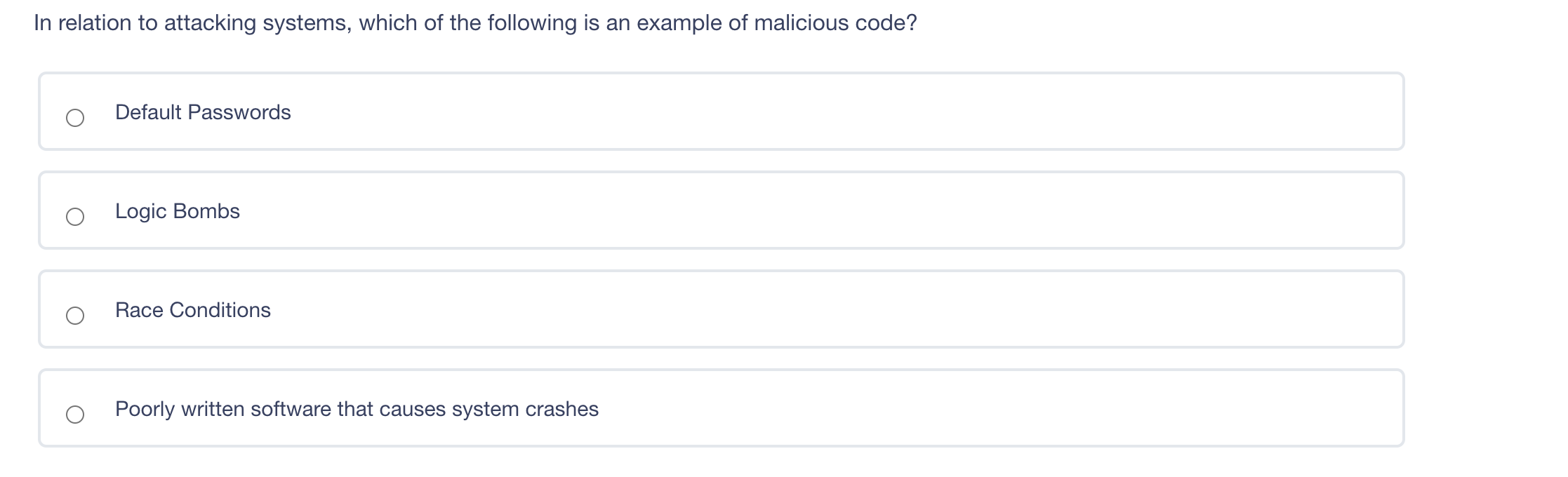
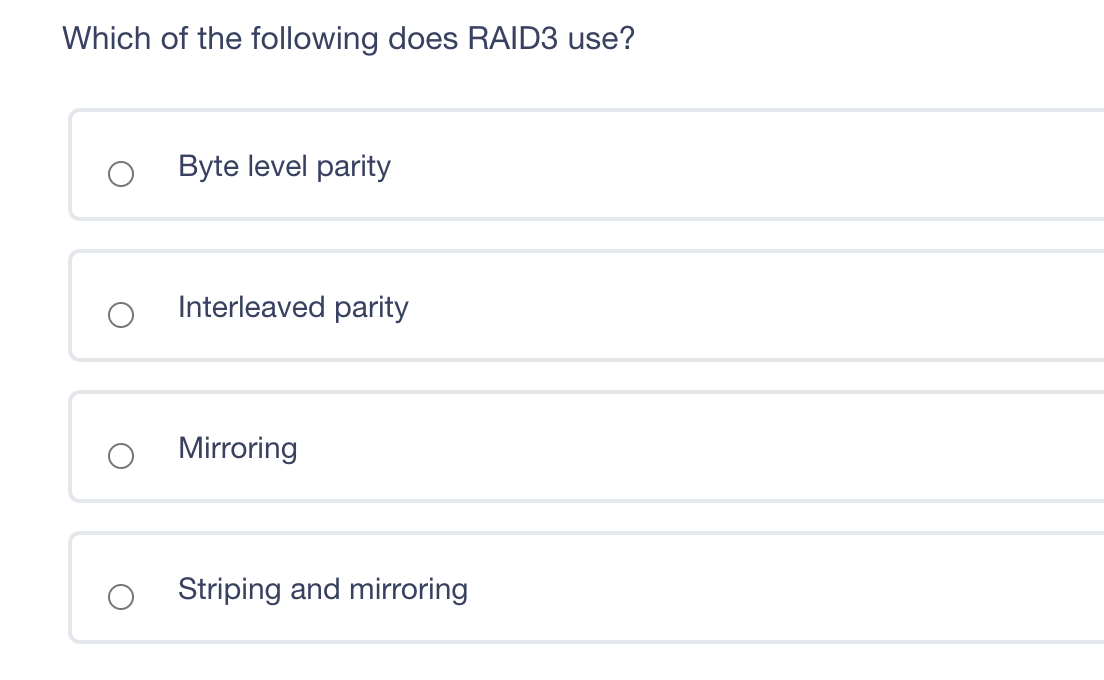
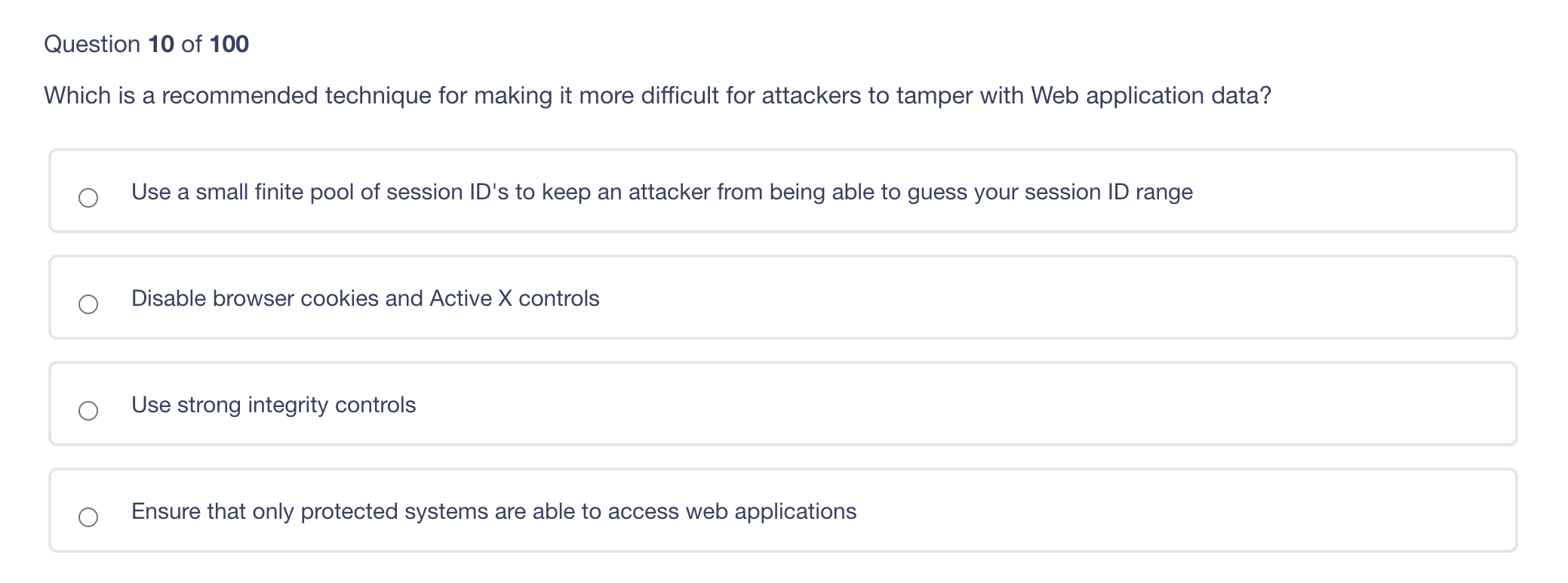
The principle of least privilege is best described as ? Ensuring that only the minimum required access rights are given to users at any time Providing management and users with the lowest possible level of access to the information they request Regularly rotating positions within a department or job function Identifying job roles that provide too much access to information and adjusting those job roles Which of the following answers would define the role of Senior Management? Set out the proper procedures for handling information Determine the appropriate baseline controls for systems components Be ultimately accountable for information security Lead any investigations into security breaches The difference between rule-based access control and role-based access control is what? Rule-based access control applies to groups, whereas role-based access control applies to individual users. Rule-based access control is better for small businesses, whereas role-based access control is more suited for large businesses. Rule-based access controls assign access parameters to user accounts, whereas role-based access control is based on the level of access required for a job function. Rule-based access controls are easy to implement in a highly mobile workforce, whereas role-based access controls are not. Diffie-Hellman's paper in 1976 laid the foundation for what? Public Key Infrastructure (PKI) IPsec AES CBC encryption PGP Which of these is a confidentiality model? Biba Graham-Denning Brewer-Nash Clark-Wilson In relation to attacking systems, which of the following is an example of malicious code? Default Passwords Logic Bombs Race Conditions Poorly written software that causes system crashes Which of the following does RAID3 use? Byte level parity Interleaved parity Mirroring Striping and mirroring Question 10 of 100 Which is a recommended technique for making it more difficult for attackers to tamper with Web application data? Use a small finite pool of session ID's to keep an attacker from being able to guess your session ID range Disable browser cookies and Active X controls Use strong integrity controls Ensure that only protected systems are able to access web applications Which of the following includes educating employees about the security risks inherent to Internet use in the workplace? Employee disciplinary actions Penetration Testing User awareness training Vulnerability AssessmentsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


