Answered step by step
Verified Expert Solution
Question
1 Approved Answer
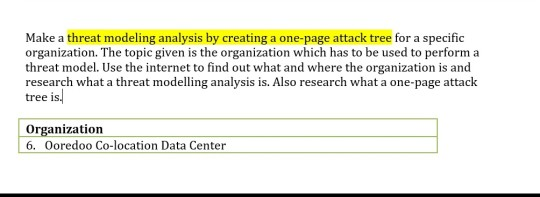
please help in whatever way you can any help is appreciated !! Make a threat modeling analysis by creating a one-page attack tree for a
please help in whatever way you can any help is appreciated !!
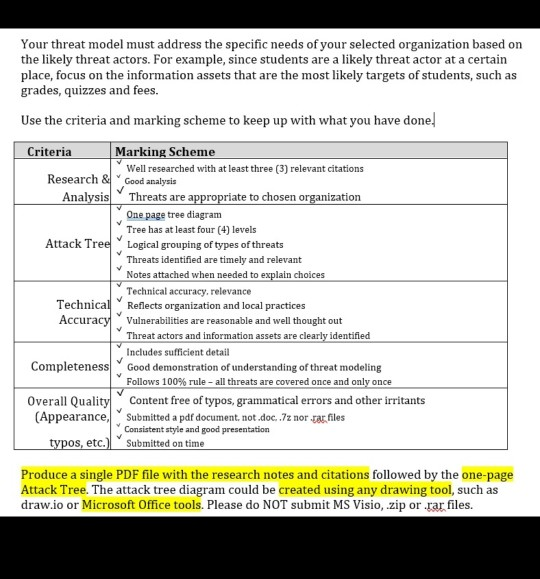
Make a threat modeling analysis by creating a one-page attack tree for a specific organization. The topic given is the organization which has to be used to perform a threat model. Use the internet to find out what and where the organization is and research what a threat modelling analysis is. Also research what a one-page attack tree is. Organization 6. Ooredoo Co-location Data Center Your threat model must address the specific needs of your selected organization based on the likely threat actors. For example, since students are a likely threat actor at a certain place, focus on the information assets that are the most likely targets of students, such as grades, quizzes and fees. Use the criteria and marking scheme to keep up with what you have done. Criteria Marking Scheme Well researched with at least three (3) relevant citations Research & Good analysis Analysis Threats are appropriate to chosen organization One page tree diagram Tree has at least four (4) levels Attack Tree Logical grouping of types of threats Threats identified are timely and relevant Notes attached when needed to explain choices Technical accuracy, relevance Technical Reflects organization and local practices Accuracy. Vulnerabilities are reasonable and well thought out Threat actors and information assets are clearly identified Includes sufficient detail Completeness Good demonstration of understanding of threat modeling Follows 100% rule - all threats are covered once and only once Overall Quality Content free of typos, grammatical errors and other irritants (Appearance, Submitted a pdf document, not.doc, .7z nor tar files Consistent style and good presentation typos, etc.) Submitted on time Produce a single PDF file with the research notes and citations followed by the one-page Attack Tree. The attack tree diagram could be created using any drawing tool, such as draw.io or Microsoft Office tools. Please do NOT submit MS Visio, zip or rar files. Make a threat modeling analysis by creating a one-page attack tree for a specific organization. The topic given is the organization which has to be used to perform a threat model. Use the internet to find out what and where the organization is and research what a threat modelling analysis is. Also research what a one-page attack tree is. Organization 6. Ooredoo Co-location Data Center Your threat model must address the specific needs of your selected organization based on the likely threat actors. For example, since students are a likely threat actor at a certain place, focus on the information assets that are the most likely targets of students, such as grades, quizzes and fees. Use the criteria and marking scheme to keep up with what you have done. Criteria Marking Scheme Well researched with at least three (3) relevant citations Research & Good analysis Analysis Threats are appropriate to chosen organization One page tree diagram Tree has at least four (4) levels Attack Tree Logical grouping of types of threats Threats identified are timely and relevant Notes attached when needed to explain choices Technical accuracy, relevance Technical Reflects organization and local practices Accuracy. Vulnerabilities are reasonable and well thought out Threat actors and information assets are clearly identified Includes sufficient detail Completeness Good demonstration of understanding of threat modeling Follows 100% rule - all threats are covered once and only once Overall Quality Content free of typos, grammatical errors and other irritants (Appearance, Submitted a pdf document, not.doc, .7z nor tar files Consistent style and good presentation typos, etc.) Submitted on time Produce a single PDF file with the research notes and citations followed by the one-page Attack Tree. The attack tree diagram could be created using any drawing tool, such as draw.io or Microsoft Office tools. Please do NOT submit MS Visio, zip or rar filesStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


