Please help me in solving this assignment
Regards.
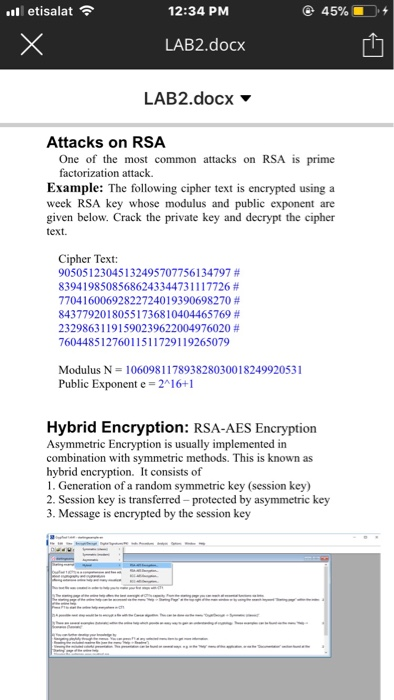
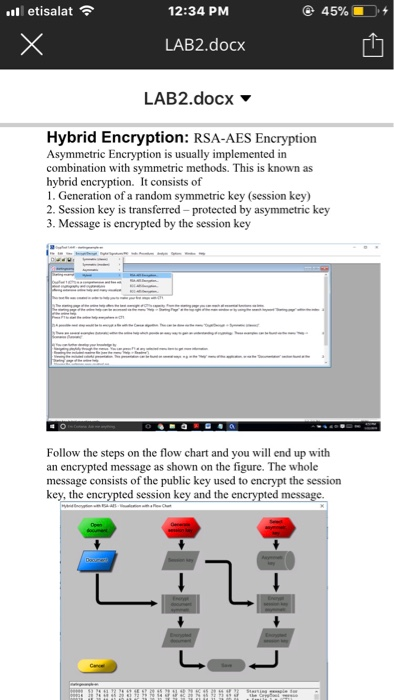
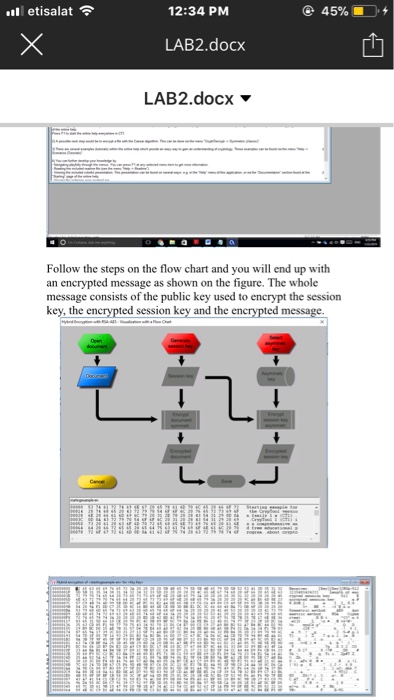
etisalat 12:34 PM @ 45% iO. + LAB2.docx LAB2.docx Attacks on RSA One of the most common attacks on RSA is prime factorization attack Example: The following cipher text is encrypted using a week RSA key whose modulus and public exponent are given below. Crack the private key and decrypt the cipher text. Cipher Text: 905051 230451 324957077561 34797 # 83941 98508568624334473 1 1 1 7726 # 77041 60069282272401 9390698270 # 843 779201 80551 73681 0404465769 # 23298631 1 9 1 5902 39622004976020 # 76044851276011511729119265079 Modulus N 106098117893828030018249920531 Public Exponent e 2 16+1 Hybrid Encryption: RSA-AES Encryption Asymmetric Encryption is usually implemented in combination with symmetric methods. This is known as hybrid encryption. It consists of 1. Generation of a random symmetric key (session key) 2. Session key is transferred-protected by asymmetric key 3. Message is encrypted by the session key etisalat 12:34 PM @ 45% iO. + LAB2.docx LAB2.docx Hybrid Encryption: RSA-AES Encryption Asymmetric Encryption is usually implemented in combination with symmetric methods. This is known as hybrid encryption. It consists of 1. Generation of a random symmetric key (session key 2. Session key is transferred-protected by asymmetric key 3. Message is encrypted by the session key !! Follow the steps on the flow chart and you will end up with an encrypted message as shown on the figure. The whol message consists of the public key used to encrypt the session key, the encrypted session key and the encrypted message. l etisalat 12:34 PM LAB2.docx LAB2.docx Follow the steps on the flow chart and you wil end up with an encrypted message as shown on the figure. The whole message consists of the public key used to encrypt the session key, the e session key and the etisalat 12:34 PM @ 45% iO. + LAB2.docx LAB2.docx Attacks on RSA One of the most common attacks on RSA is prime factorization attack Example: The following cipher text is encrypted using a week RSA key whose modulus and public exponent are given below. Crack the private key and decrypt the cipher text. Cipher Text: 905051 230451 324957077561 34797 # 83941 98508568624334473 1 1 1 7726 # 77041 60069282272401 9390698270 # 843 779201 80551 73681 0404465769 # 23298631 1 9 1 5902 39622004976020 # 76044851276011511729119265079 Modulus N 106098117893828030018249920531 Public Exponent e 2 16+1 Hybrid Encryption: RSA-AES Encryption Asymmetric Encryption is usually implemented in combination with symmetric methods. This is known as hybrid encryption. It consists of 1. Generation of a random symmetric key (session key) 2. Session key is transferred-protected by asymmetric key 3. Message is encrypted by the session key etisalat 12:34 PM @ 45% iO. + LAB2.docx LAB2.docx Hybrid Encryption: RSA-AES Encryption Asymmetric Encryption is usually implemented in combination with symmetric methods. This is known as hybrid encryption. It consists of 1. Generation of a random symmetric key (session key 2. Session key is transferred-protected by asymmetric key 3. Message is encrypted by the session key !! Follow the steps on the flow chart and you will end up with an encrypted message as shown on the figure. The whol message consists of the public key used to encrypt the session key, the encrypted session key and the encrypted message. l etisalat 12:34 PM LAB2.docx LAB2.docx Follow the steps on the flow chart and you wil end up with an encrypted message as shown on the figure. The whole message consists of the public key used to encrypt the session key, the e session key and the