Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please help me with this question Incident Reso Hank Law, web Company locat suspicious act response Report on June 30, 2004. 16. Attack! w webmaster
please help me with this question 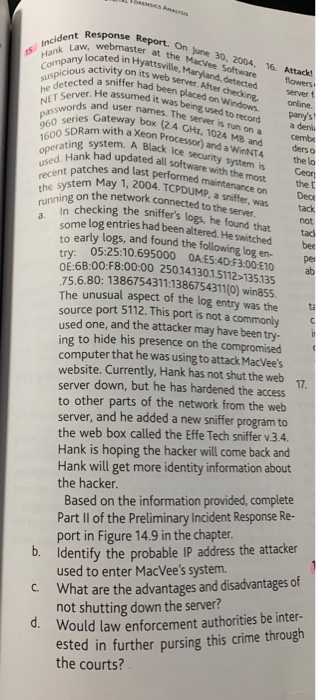


Incident Reso Hank Law, web Company locat suspicious act response Report on June 30, 2004. 16. Attack! w webmaster at the MacVee Sot software located in Hyattsville, Maryland deter on its web server. After checking Her had been placed on Windows sumed it was being used to record and user names. The server is run on a ries Gateway box (2.4 GHz, 1024 MB Ram with a Xeon Processor) and a WinNT4 system. A Black Ice security System is ad updated all software with the most atches and last performed maintenance May 1, 2004. TCPDUMP, a sniffer, was passwords and 960 series 1600 SDRam w operating syste recent patches a the system May running on the ne a in checki tad Mowers detected a sniffer had Server CT Server. He assumed i online pany's a denis Cembe derso the lo Hank had updated all software Geon the Dect on the network connected to the server tack checking the sniffer's logs, he found that not some log entries had been altered. He switched to early logs, and found the following log en- ber try 05:25:10.695000 OA:E5:4D-F3.00-E10 OE:63:00:F8:00:00 250.14.130.1.5112135135 75.6.80: 1386754311:13867543110) win855 The unusual aspect of the log entry was the source port 5112. This port is not a commonly used one, and the attacker may have been try- ing to hide his presence on the compromised computer that he was using to attack MacVee's website. Currently, Hank has not shut the web server down, but he has hardened the access to other parts of the network from the web server, and he added a new sniffer program to the web box called the Effe Tech sniffer v.3.4. Hank is hoping the hacker will come back and Hank will get more identity information about b. the hacker Based on the information provided, complete Part II of the Preliminary Incident Response Re- port in Figure 14.9 in the chapter. Identify the probable IP address the attacker used to enter MacVee's system. What are the advantages and disadvantages of not shutting down the server? Would law enforcement authorities be inter- ested in further pursing this crime through the courts? C. Figure 14.9. Sample Preliminary Incident Response Report PRELIMINARY INCIDENT RESPONSE REPORT Part I: Description of Victim 1. Name of company 2. Company host and sites involved 3. Company Contact: a. Name of Individual b. E-mail d. Mailing Address Position c. Phone Part II: Description of the Incident 1. Date of the incident: 2. GMT time of the incident: 3. Physical location of the attacked system (company headquarters, other site or statal 4. Operating system on the attacked system: 5. Hardware: 6. Security systems in use on the attacked system (name and version) 7. Mission of the attacked system (What is its function?): . . Describe how the attack was detected. 9Describe the attacker's ass etc.). 14-23 os. siffespoofing, vodi 10. Estimate time duration of the incident from desection to completion 11. If possible, estimate how long the sacker was the wystem before being detected 12. Description of the damage done in the wack. 13. Provide an estimated dollar valuation of the damage show calculations 14. Describe activities taken by the victim up to the time of filing the report 15. Attach copies of appropriate loes (un to 2011 laborate the times on the If the times on the boys are not reconcile them to the Term Part III. Suspect(s) Information 1. 2. Source IP address for the attack Provide a complete description of how this IP address was collected 3. Organization responsible for IP address 4. Contact information for the organization in Item 33. a. Name of individual b. E-mail C.Phone d. Mailing Address Position 5. E-mail address of the attacker, if known 6. ICQ ID number of the attacker, if known 7. Name of the attacker, if known 8. Address of the attacker, if known 9. Description of further contact that the attacker has requested 10. The date and time when the attacker is demanding further contact 11. If possible describe the suspected reason for the attack (extortion, fraud, terror, mischievous behavior, etc.). 12. Attach copies of messages or threats left by the attacker (e-mail messages coding and messages on web defacement, etc.). 13. Attach appropriate copies of Whois, Rwhois, Traceroute, Ping, Nslookup, and Finger searches on the suspect(s). Currently, not all local law enforcement officials are familiar with Internet fraud. Few local law enforce- ment officials will be familiar with the technical information that is provided to them which makes redress for victims an unlikely outcome. If the attack is part of a coordinated attack by hackers on several high- profile sites die banks or big retailers) and the dollar value of the damages is significant, federal or state law enforcement will likely have an interest in the crime. If law enforcement accepts the case arents officers can serve subpoenas for the disclosure of additional evidence such as the needed ISP loes 


Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


