Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please include comments in the program Your Task An important class of algorithms that some computer scientists concern themselves with are encryption and decryption techniques.
please include comments in the program
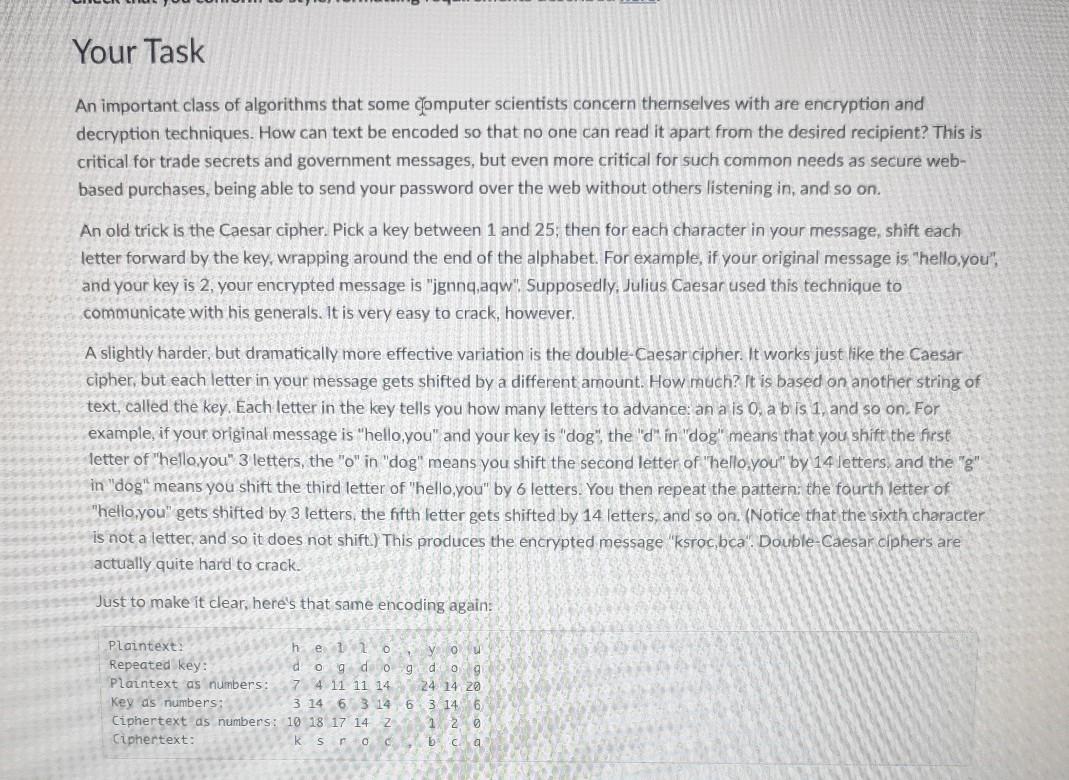
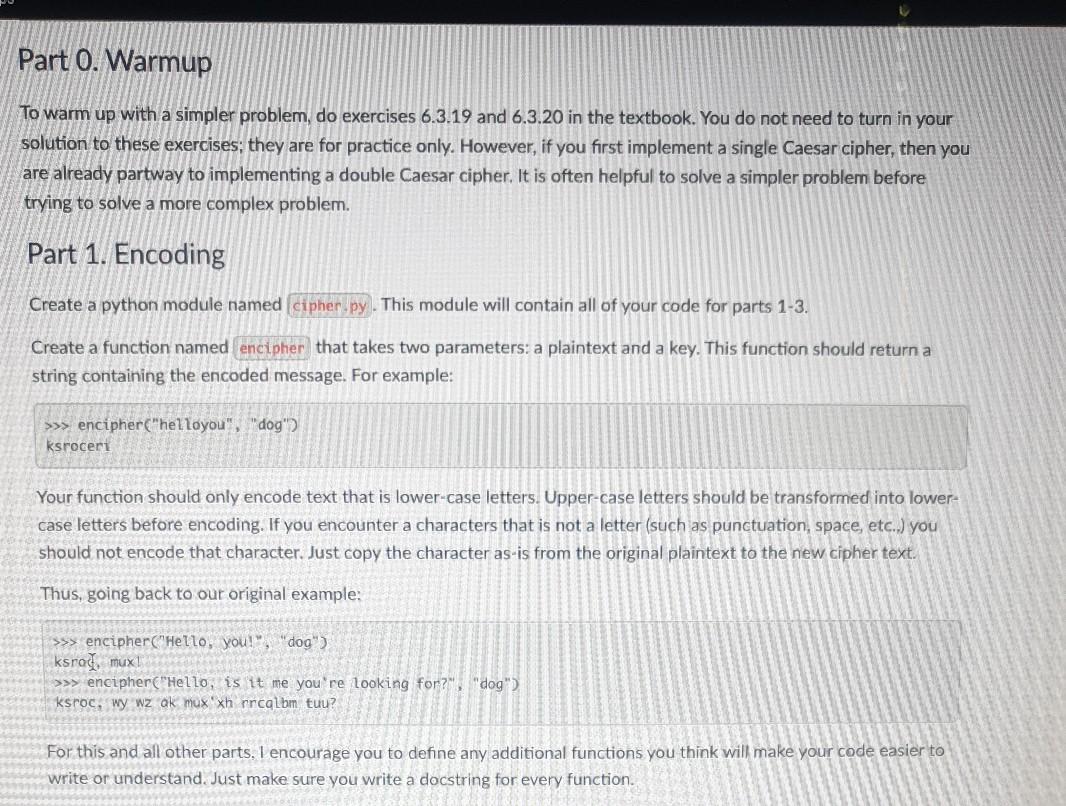
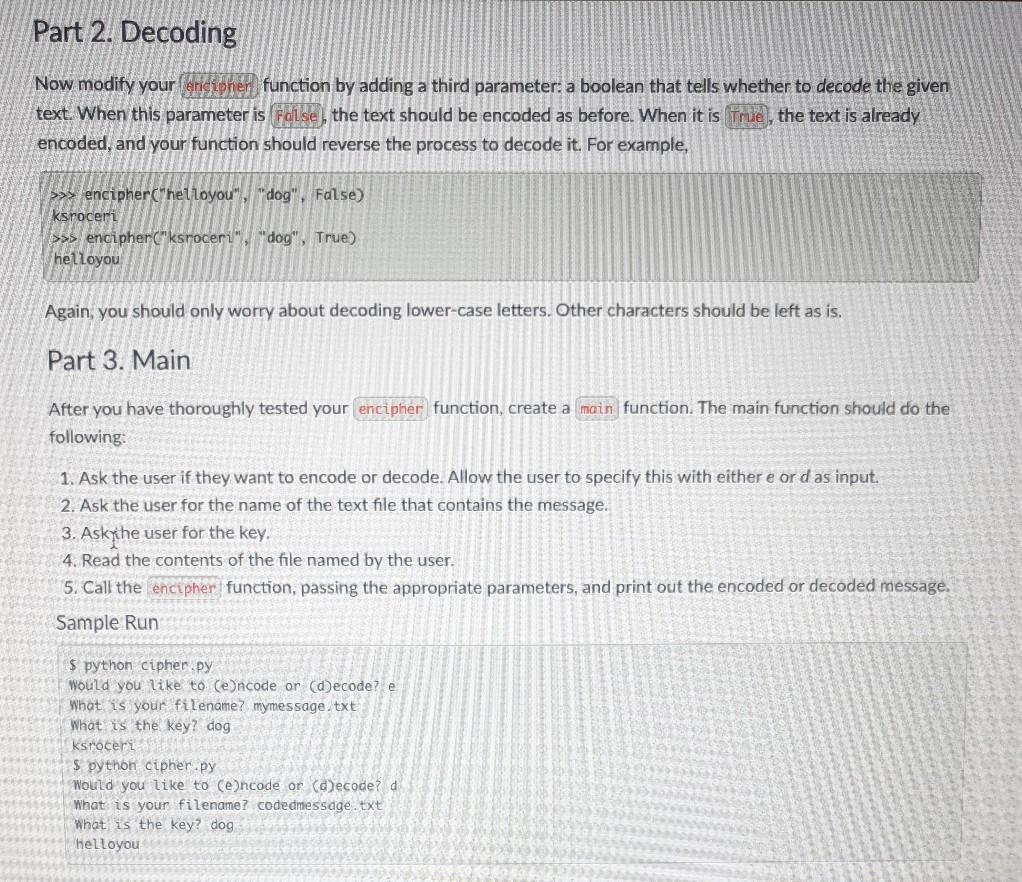
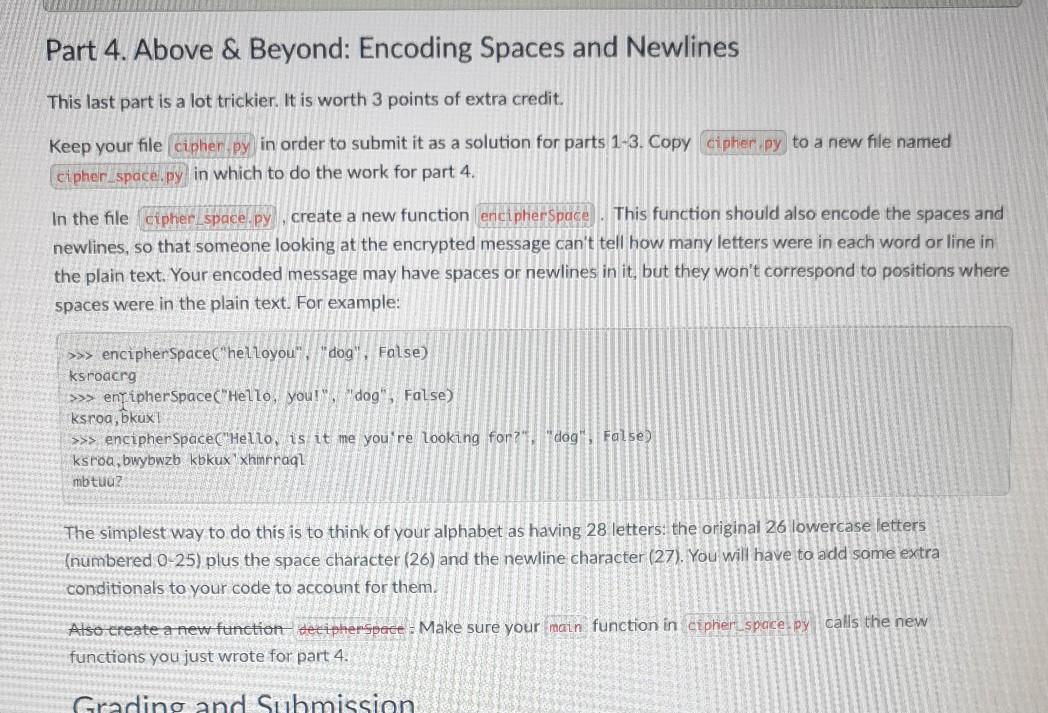
Your Task An important class of algorithms that some computer scientists concern themselves with are encryption and decryption techniques. How can text be encoded so that no one can read it apart from the desired recipient? This is critical for trade secrets and government messages, but even more critical for such common needs as secure web- based purchases, being able to send your password over the web without others listening in, and so on. An old trick is the Caesar cipher. Pick a key between 1 and 25, then for each character in your message, shift each letter forward by the key, wrapping around the end of the alphabet. For example, if your original message is "hello,you". and your key is 2, your encrypted message is "ignng,agw". Supposedly, Julius Caesar used this technique to communicate with his generals. It is very easy to crack, however, A slightly harder, but dramatically more effective variation is the double-Caesar cipher. It works just like the Caesar cipher, but each letter in your message gets shifted by a different amount. How much? It is based on another string of text, called the key. Each letter in the key tells you how many letters to advance: an a is 0, a b is 1, and so on. For example, if your original message is "hello,you" and your key is "dog" the "d in "dog' means that you shift the first letter of "hello.you" 3 letters, the "o" in "dog" means you shift the second le of "hello.you" by 14 letters, and the "g" in "dog" means you shift the third letter of "hello,you" by 6 letters. You then repeat the pattern: the fourth letter of "hello, you" gets shifted by 3 letters, the fifth letter gets shifted by 14 letters, and so on. (Notice that the sixth character is not a letter, and so it does not shift.) This produces the encrypted message "ksroc bca". Double-Caesar ciphers are actually quite hard to crack. Just to make it clear, here's that same encoding again: you Plaintext he 120 Repeated key: dog do g d 09 Plantext as numbers: 7 4 11 11 14 24 14 20 Key as numbers: 3 14 6 3 14 6 3. 146 Ciphertext as numbers: 19 18 17 14 Z 126 Cuphertext: k srobca Part 0. Warmup To warm up with a simpler problem, do exercises 6.3.19 and 6.3.20 in the textbook. You do not need to turn in your solution to these exercises, they are for practice only. However, if you first implement a single Caesar cipher, then you are already partway to implementing a double Caesar cipher. It is often helpful to solve a simpler problem before trying to solve a more complex problem. Part 1. Encoding Create a python module named cipher.py . This module will contain all of your code for parts 1-3. Create a function named encipher that takes two parameters: a plaintext and a key. This function should return a string containing the encoded message. For example: >>> encipher("helloyou", "dog") ksroceri Your function should only encode text that is lower-case letters. Upper-case letters should be transformed into lower- case letters before encoding. If you encounter a characters that is not a letter (such as punctuation, space, etc..) you should not encode that character. Just copy the character as-is from the original plaintext to the new cipher text. Thus, going back to our original example: >>> encipher("Hello, you!", "dog") ksrod mux! >>> encipher("Hello, is it me you're looking for?", "dog") ksroc, Wy wzak mux xh nrcalom tuu? For this and all other parts. I encourage you to define any additional functions you think will make your code easier to write or understand. Just make sure you write a docstring for every function. Part 2. Decoding Now modify your (anicipher function by adding a third parameter: a boolean that tells whether to decode the given text. When this parameter is false, the text should be encoded as before. When it is true, the text is already encoded, and your function should reverse the process to decode it. For example, >>> encipher("helloyou", "dog", False) ksroceri >>> encipher("ksroceri", "dog", True) hel Loyou Again, you should only worry about decoding lower-case letters. Other characters should be left as is, Part 3. Main After you have thoroughly tested your encipher function, create a main function. The main function should do the following: 1. Ask the user if they want to encode or decode. Allow the user to specify this with either e or d as input. 2. Ask the user for the name of the text file that contains the message. 3. Askythe user for the key. 4. Read the contents of the file named by the user. 5. Call the encipher function, passing the appropriate parameters, and print out the encoded or decoded message. Sample Run $ python cipher.py Would you like to (encode or (decode? e What is your filename? mymessage.txt What is the key? dog ksroceri $ python cipher.py Would you like to encode or (decode? d What is your filename? codedmessage.txt What is the key? dog helloyou Part 4. Above Beyond: Encoding Spaces and Newlines This last part is a lot trickier. It is worth 3 points of extra credit. Keep your file cipher.py in order to submit it as a solution for parts 1-3. Copy cipher py to a new file named Icipher_spacel.py in which to do the work for part 4. In the file cipher space.py create a new function encipher Space This function should also encode the spaces and newlines, so that someone looking at the encrypted message can't tell how many letters were in each word or line in the plain text. Your encoded message may have spaces or newlines in it, but they won't correspond to positions where spaces were in the plain text. For example: >>> encipherSpace("helloyou" "dog", False) ksroacrg >>> enripherSpace("Hello, you!", "dog", False) ksroa, bkux >>> encipherSpace("Hello, is it me you're looking for?" "dog", False) ksroa, bwybwzb kbkux xhmrragl mbtuu? The simplest way to do this is to think of your alphabet as having 28 letters: the original 26 lowercase letters (numbered 0-25) plus the space character (26) and the newline character (27). You will have to add some extra conditionals to your code to account for them. Also create a new function decipherspace. Make sure your main function in cipher space.py calls the new functions you just wrote for part 4. Grading and Submission Grading and Submission Document your functions and organize your code per section 3.4 of the textbook. Submit one file, cipher.py, through this assignment on Canvas. If you attempted part 4 for extra credit, also submit cipher_space.py Style, comments, following instructions, and clarity - 4 pts Part 1: Encoding - 8 pts Part 2: Decoding - 3 pts Part 3: Main - 3 pts Part 4: Above & Beyond: Encoding spaces and newlines - 3 pts . jaugmex99.mgareko hmixStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


