Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Please read the question carefully and explain your work clearly Computer A sends 200bit data packets to computer B. The capacity of the physical
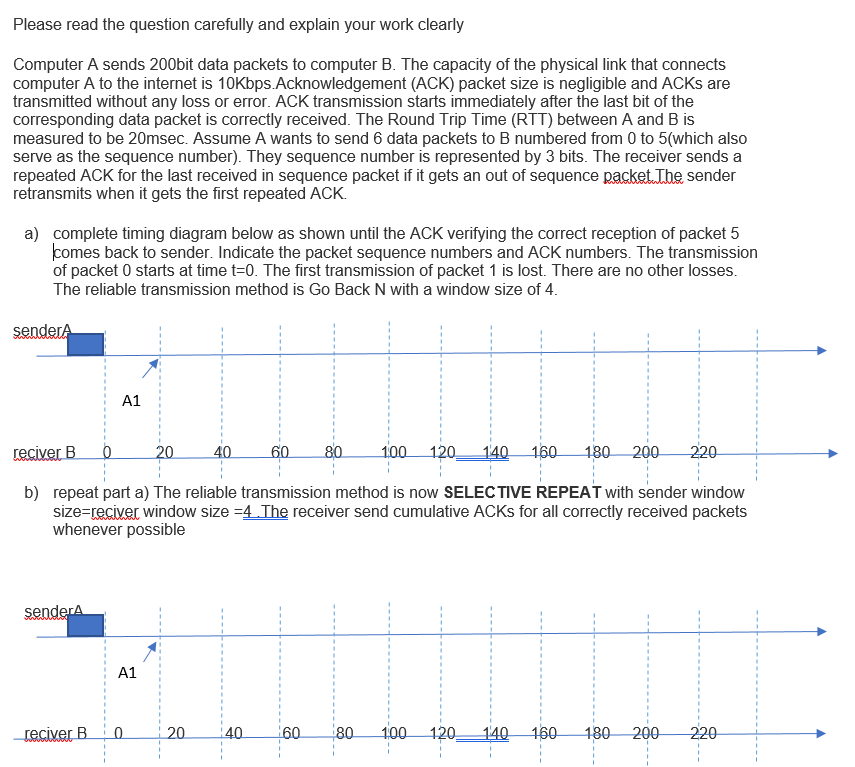

Please read the question carefully and explain your work clearly Computer A sends 200bit data packets to computer B. The capacity of the physical link that connects computer A to the internet is 10Kbps.Acknowledgement (ACK) packet size is negligible and ACKs are transmitted without any loss or error. ACK transmission starts immediately after the last bit of the corresponding data packet is correctly received. The Round Trip Time (RTT) between A and B is measured to be 20msec. Assume A wants to send 6 data packets to B numbered from 0 to 5(which also serve as the sequence number). They sequence number is represented by 3 bits. The receiver sends a repeated ACK for the last received in sequence packet if it gets an out of sequence packet. The sender retransmits when it gets the first repeated ACK. a) complete timing diagram below as shown until the ACK verifying the correct reception of packet 5 comes back to sender. Indicate the packet sequence numbers and ACK numbers. The transmission of packet 0 starts at time t=0. The first transmission of packet 1 is lost. There are no other losses. The reliable transmission method is Go Back N with a window size of 4. senderA reciver B 1:00 120 140 160 180 200 220 b) repeat part a) The reliable transmission method is now SELECTIVE REPEAT with sender window size=reciver window size =4. The receiver send cumulative ACKS for all correctly received packets whenever possible senderA A1 reciver B A1 0 20 20 40 40 60 60 80 1:00 120. 140 160 180 200 220 1 Transport Layer Security (TLS) is one of the most widely used security services in computer network. TLS relies on Transmission Control Protocol (Layer 4 protocol of OSI model) to provide an end-to-end reliable service. Discuss how TLS overcome the following security threats: (i) (ii) (iii) (iv) (v) Password being eavesdropped by using packet sniffer. Man in the middle attack. IP address spoofing Flooding of SYN message Replay attack [10 marks]
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


